43-2
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 43 Configuring the Cisco Phone Proxy
Information About the Cisco Phone Proxy
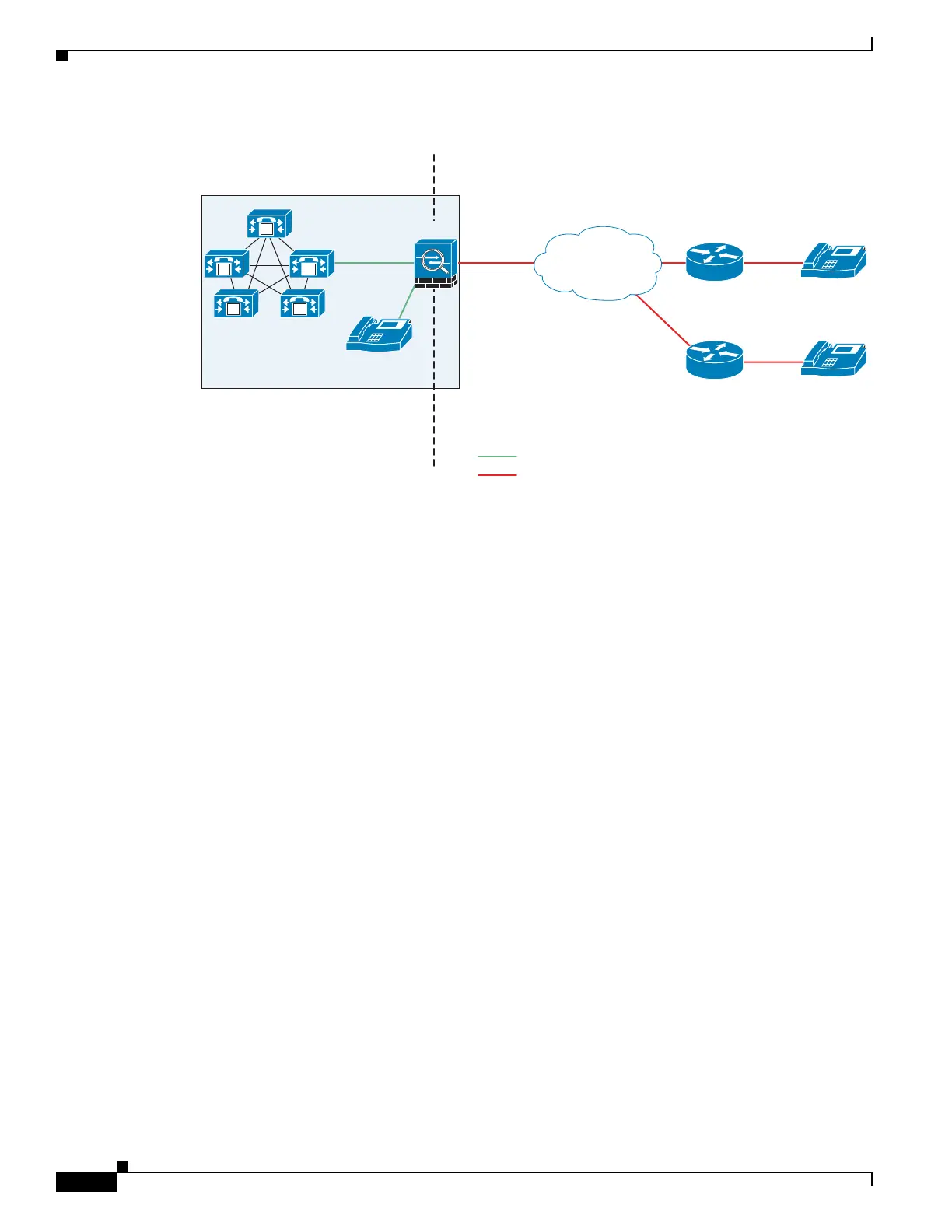
Figure 43-1 Phone Proxy Secure Deployment
The phone proxy supports a Cisco UCM cluster in mixed mode or nonsecure mode. Regardless of the
cluster mode, the remote phones that are capable of encryption are always forced to be in encrypted
mode. TLS (signaling) and SRTP (media) are always terminated on the adaptive security appliance. The
adaptive security appliance can also perform NAT, open pinholes for the media, and apply inspection
policies for the SCCP and SIP protocols. In a nonsecure cluster mode or a mixed mode where the phones
are configured as nonsecure, the phone proxy behaves in the following ways:
• The TLS connections from the phones are terminated on the adaptive security appliance and a TCP
connection is initiated to the Cisco UCM.
• SRTP sent from external IP phones to the internal network IP phone via the adaptive security
appliance is converted to RTP.
In a mixed mode cluster where the internal IP phones are configured as authenticated, the TLS
connection is not converted to TCP to the Cisco UCM but the SRTP is converted to RTP.
In a mixed mode cluster where the internal IP phone is configured as encrypted, the TLS connection
remains a TLS connection to the Cisco UCM and the SRTP from the remote phone remains SRTP to the
internal IP phone.
Since the main purpose of the phone proxy is to make the phone behave securely while making calls to
a nonsecure cluster, the phone proxy performs the following major functions:
• Creates the certificate trust list (CTL) file, which is used to perform certificate based authentication
with remote phones.
• Modifies the IP phone configuration file when it is requested via TFTP, changes security fields from
nonsecure to secure, and signs all files sent to the phone. These modifications secure remote phones
by forcing the phones to perform encrypted signaling and media.
• Terminates TLS signaling from the phone and initiates TCP or TLS to Cisco UCM
• Inserts itself into the media path by modifying the Skinny and SIP signaling messages.
• Terminates SRTP and initiates RTP/SRTP to the called party.
271631
Internet
ASA
Internal
IP phone
IP
IP
Remote
IP phone
IP
Remote
IP phone
M M
M
MM
TLS/SRTPTCP/RTP
Unencrypted signaling
Encrypted signaling
Un-trusted / Outside / SecuredTrusted / Inside / Un-Secured
Enterprise
Home Router
w/NAT
Home Router
w/NAT

 Loading...
Loading...