7-4
Catalyst 2950 Desktop Switch Software Configuration Guide
78-11380-03
Chapter7 Configuring 802.1X Port-Based Authentication
Understanding 802.1X Port-Based Authentication
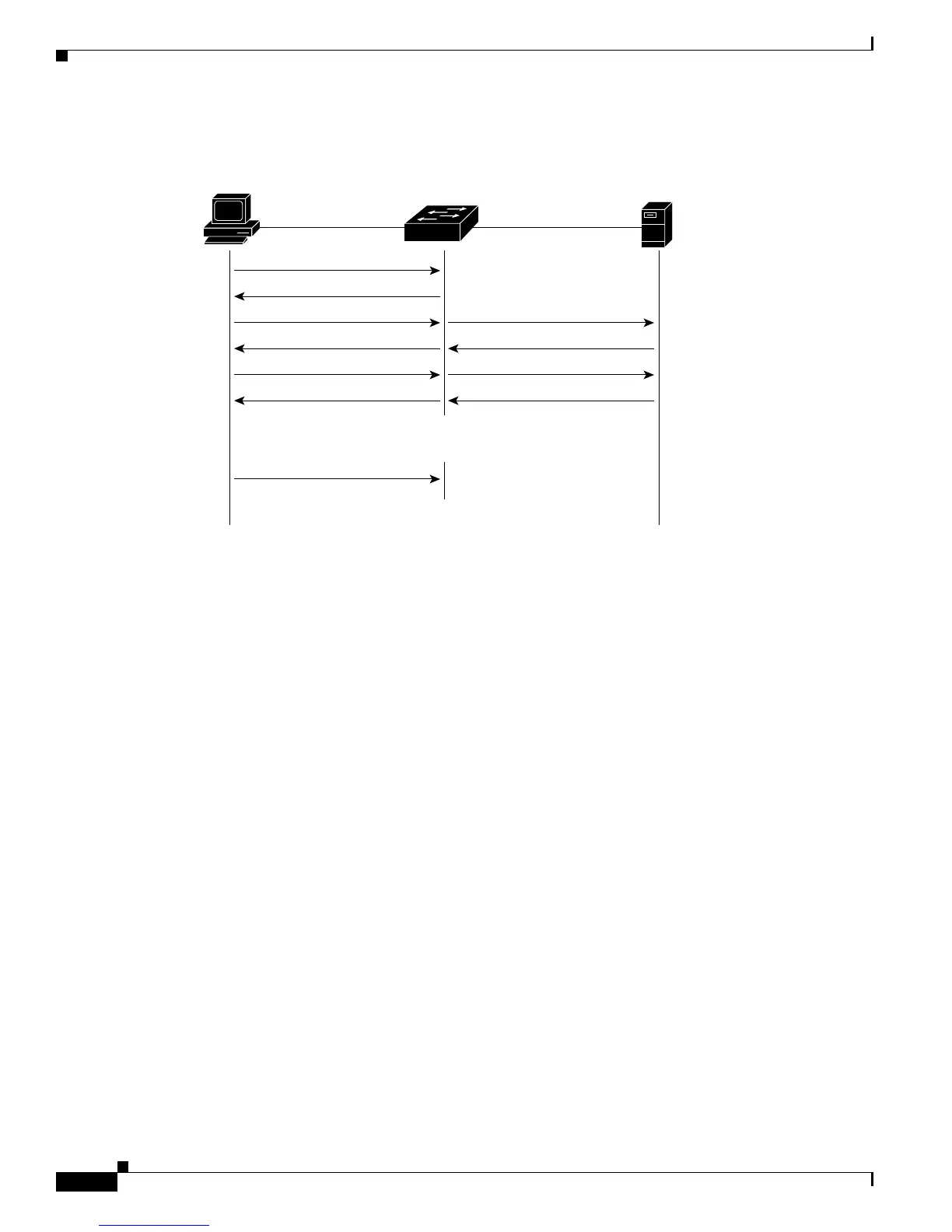
Figure 7-2 Message Exchange
Ports in Authorized and Unauthorized States
The switch port state determines whether or not the client is granted access to the network. The port starts in
the unauthorized state. While in this state, the port disallows all ingress and egress traffic except for 802.1X
packets. When a client is successfully authenticated, the port transitions to the authorized state, allowing all
traffic for the client to flow normally.
If a client that does not support 802.1X is connected to an unauthorized 802.1X port, the switch requests
the client’s identity. In this situation, the client does not respond to the request, the port remains in the
unauthorized state, and the client is not granted access to the network.
In contrast, when an 802.1X-enabled client connects to a port that is not running 802.1X , the client
initiates the authentication process by sending the EAPOL-start frame. When no response is received,
the client sends the request for a fixed number of times. Because no response is received, the client
begins sending frames as if the port is in the authorized state.
You control the port authorization state by using the dot1x port-control interface configuration
command and these keywords:
• force-authorized—disables 802.1X and causes the port to transition to the authorized state without
any authentication exchange required. The port transmits and receives normal traffic without
802.1X-based authentication of the client. This is the default setting.
• force-unauthorized—causes the port to remain in the unauthorized state, ignoring all attempts by
the client to authenticate. The switch cannot provide authentication services to the client through the
interface.
Client
Catalyst 2950 switch
Port Authorized
Port Unauthorized
EAPOL-Start
EAP-Request/Identity
EAP-Response/Identity
EAP-Request/OTP
EAP-Response/OTP
EAP-Success
RADIUS Access-Request
RADIUS Access-Challenge
RADIUS Access-Request
RADIUS Access-Accept
EAPOL-Logoff
Authentication
server
(RADIUS)
65231

 Loading...
Loading...















