193
Configuring IEEE 802.1x Port-Based Authentication
Information About Configuring IEEE 802.1x Port-Based Authentication
Figure 20 Message Exchange
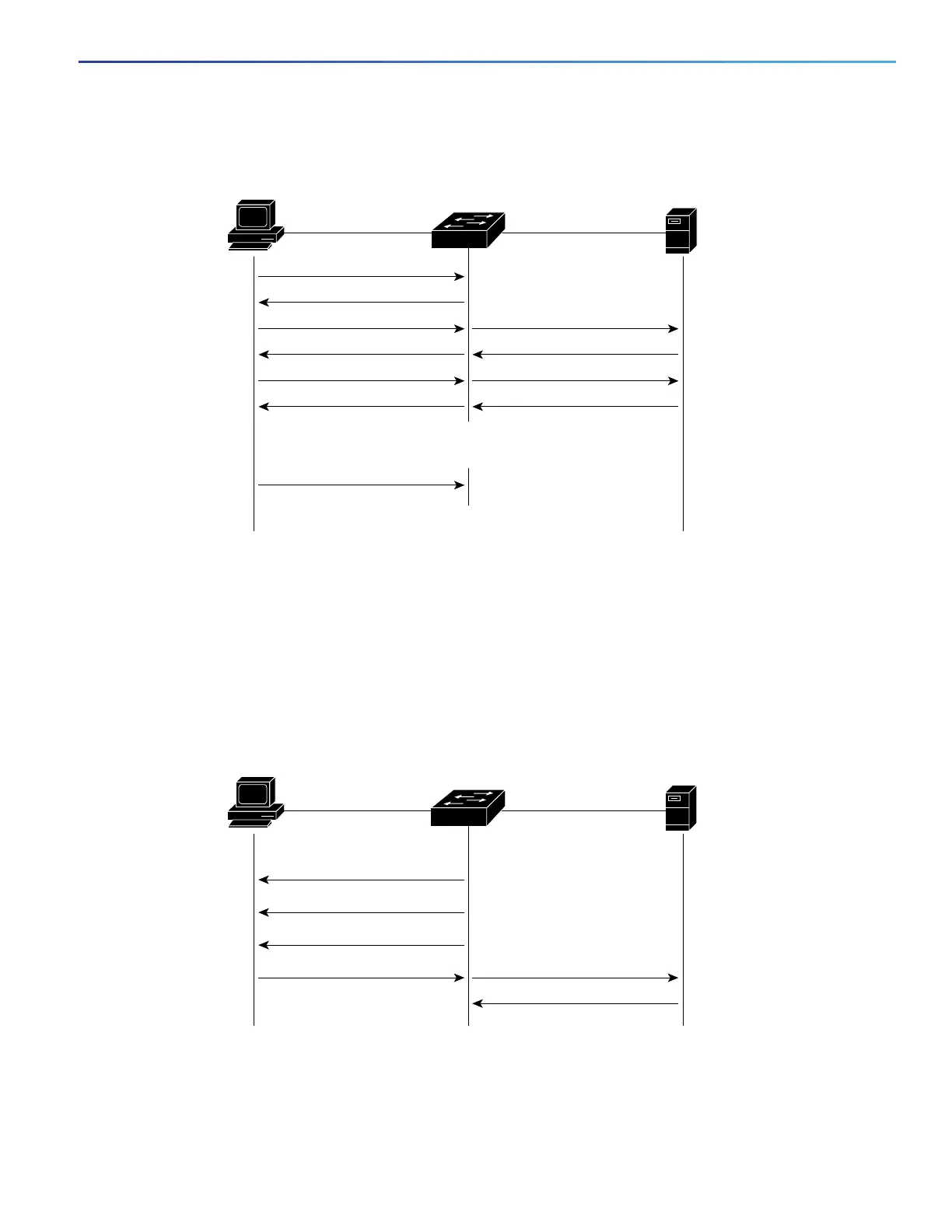
If 802.1x authentication times out while waiting for an EAPOL message exchange and MAC authentication bypass is
enabled, the switch can authorize the client when the switch detects an Ethernet packet from the client. The switch uses
the MAC address of the client as its identity and includes this information in the RADIUS-access/request frame that is
sent to the RADIUS server. After the server sends the switch the RADIUS-access/accept frame (authorization is
successful), the port becomes authorized. If authorization fails and a guest VLAN is specified, the switch assigns the port
to the guest VLAN. If the switch detects an EAPOL packet while waiting for an Ethernet packet, the switch stops the MAC
authentication bypass process and stops 802.1x authentication.
Figure 21 Message Exchange During MAC Authentication Bypass
101228
Client
Port Authorized
Port Unauthorized
EAPOL-Start
EAP-Request/Identity
EAP-Response/Identity
EAP-Request/OTP
EAP-Response/OTP
EAP-Success
RADIUS Access-Request
RADIUS Access-Challenge
RADIUS Access-Request
RADIUS Access-Accept
EAPOL-Logoff
Authentication
server
(RADIUS)
141681
Client
Switch
EAPOL Request/Identity
EAPOL Request/Identity
EAPOL Request/Identity
RADIUS Access/Request
RADIUS Access/Accept
Ethernet packet
Authentication
server
(RADIUS)

 Loading...
Loading...











