Security Configuration
8-17
11.Select OK to save the updates to the to Excessive Actions configuration used by the WIPS policy. Select
Reset to revert to the last saved configuration.
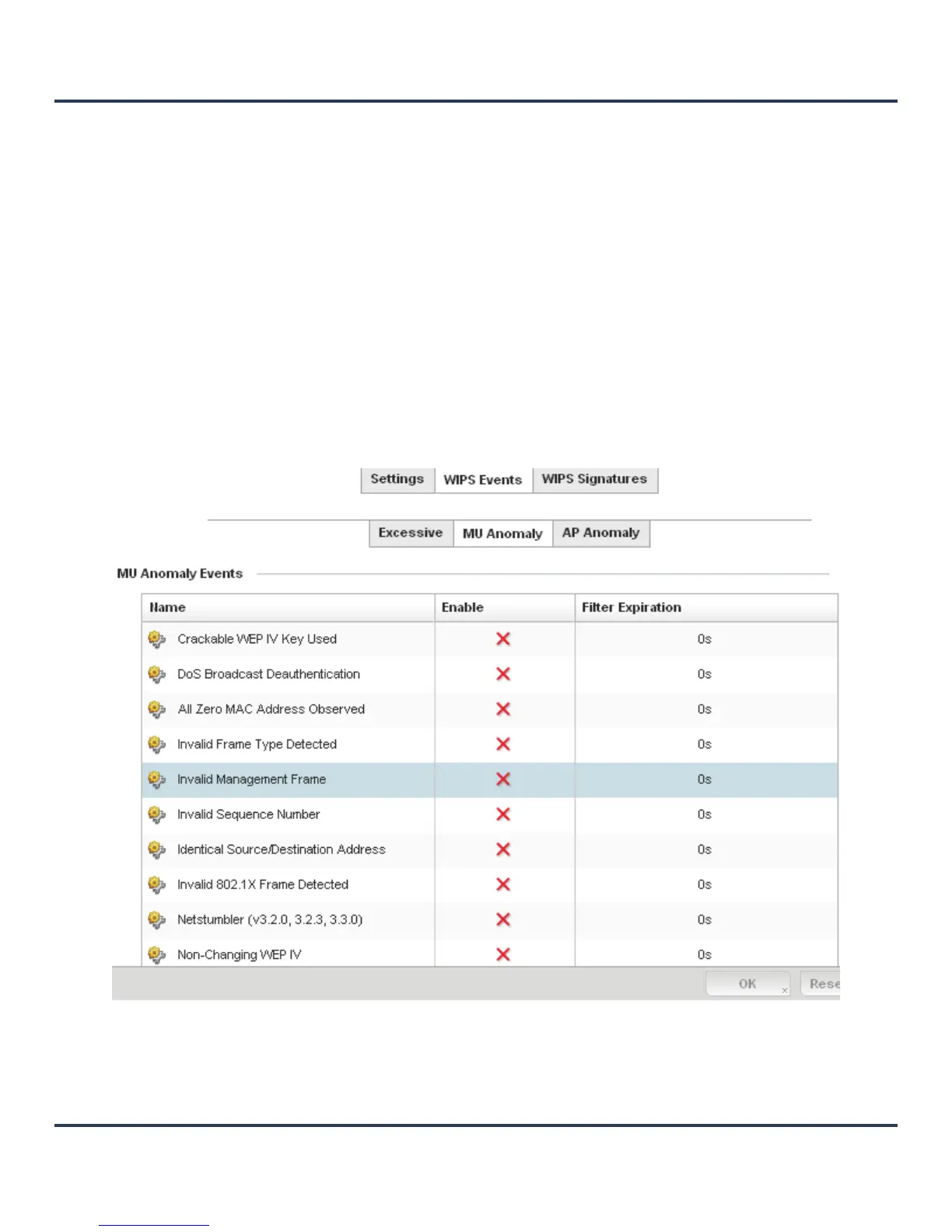
12.Select the MU Anomaly tab:
Figure 8-10 WIPS Events screen - MU Anomaly tab
MU Anomaly events are suspicious events performed by wireless clients that can compromise the
security and stability of the network. Use this MU Anomaly screen to configure the intervals clients can
be filtered upon the generation of each defined event.
Filter Expiration Set the duration the anomaly causing client is filtered. This creates a
special ACL entry and frames coming from the client are dropped. The
default setting is 0 seconds.
This value is applicable across the RF Domain. If a station is detected
performing an attack and is filtered by an Access Point, the information is
passed to the domain controller. The domain controller then propagates
this information to all the Access Points in the RF Domain.
Client Threshold Set the client threshold after which the filter is triggered and an event
generated.
Radio Threshold Set the radio threshold after which an event is recorded to the events
history.

 Loading...
Loading...











