100
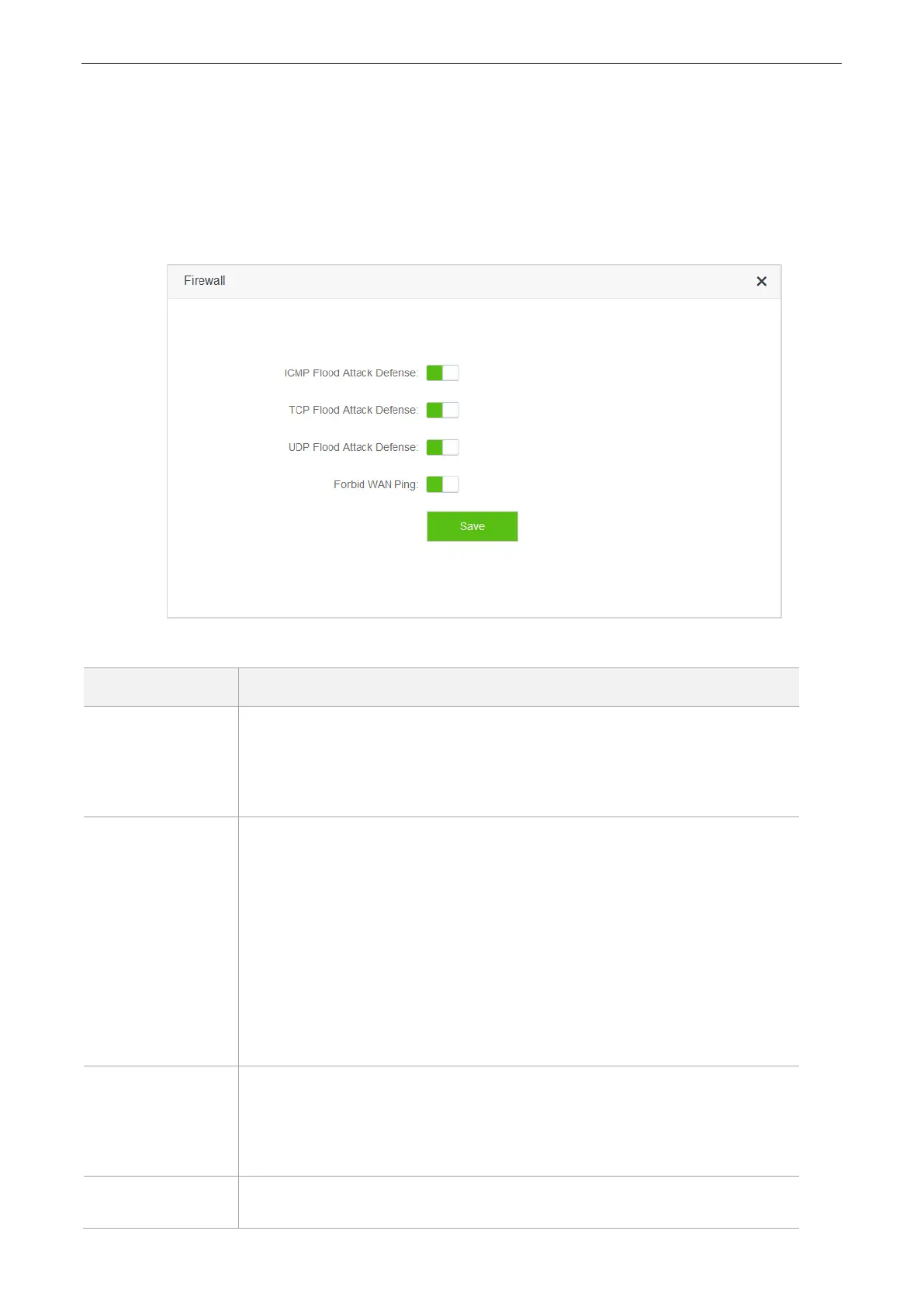
10.6 Firewall
The Firewall function can protect the router against some common DoS attacks such as ICMP Flood Attack, TCP
Flood Attack, and UCP Flood Attack. It forbids WAN Ping as well, helping secure your network.
To access the configuration page, click Advanced Settings > Firewall. By default, the Firewall function is
enabled. It is recommended to retain the default settings.
Parameter descriptions
ICMP Flood Attack
Defense
ICMP Flood Attack is an attack using ICMP packets. If an attacker sends many
ICMP ECHO packets to destination host, which results in ICMP flood. Then
destination host pays much time and resources on ICMP ECHO but nothing on
normal requests or responses, which achieves attack against destination host.
In TCP protocol, when one client sends connection request and initialization to
server, protocol stack in server will leave Backlog Quene for information exchange
in connecting process.
Attackers make use of Backlog Quene and send TCP connection requests only
with SYN to server mark many times by special program. Server will regard those
requests as uncompleted and establish sessions for them in Backlog Queue.
If those SYN requests are more than what server can hold, Backlog Queue will be
full. Then server will not accept new request so that other legal connection will be
refused.
UCP Flood Attack works on the similar principle as ICMP Flood Attack. If an
attacker sends many UDP packets to destination host. Then destination host pays
much time and resources on UDP packets but nothing on normal packet requests
or responses, which achieves attack against destination host.
When host in the internet tries to ping WAN IP address of the router, the router
will ignore that ping request automatically, protecting itself from external Ping
 Loading...
Loading...