46-2
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 46 Configuring Cisco Unified Presence
Information About Cisco Unified Presence
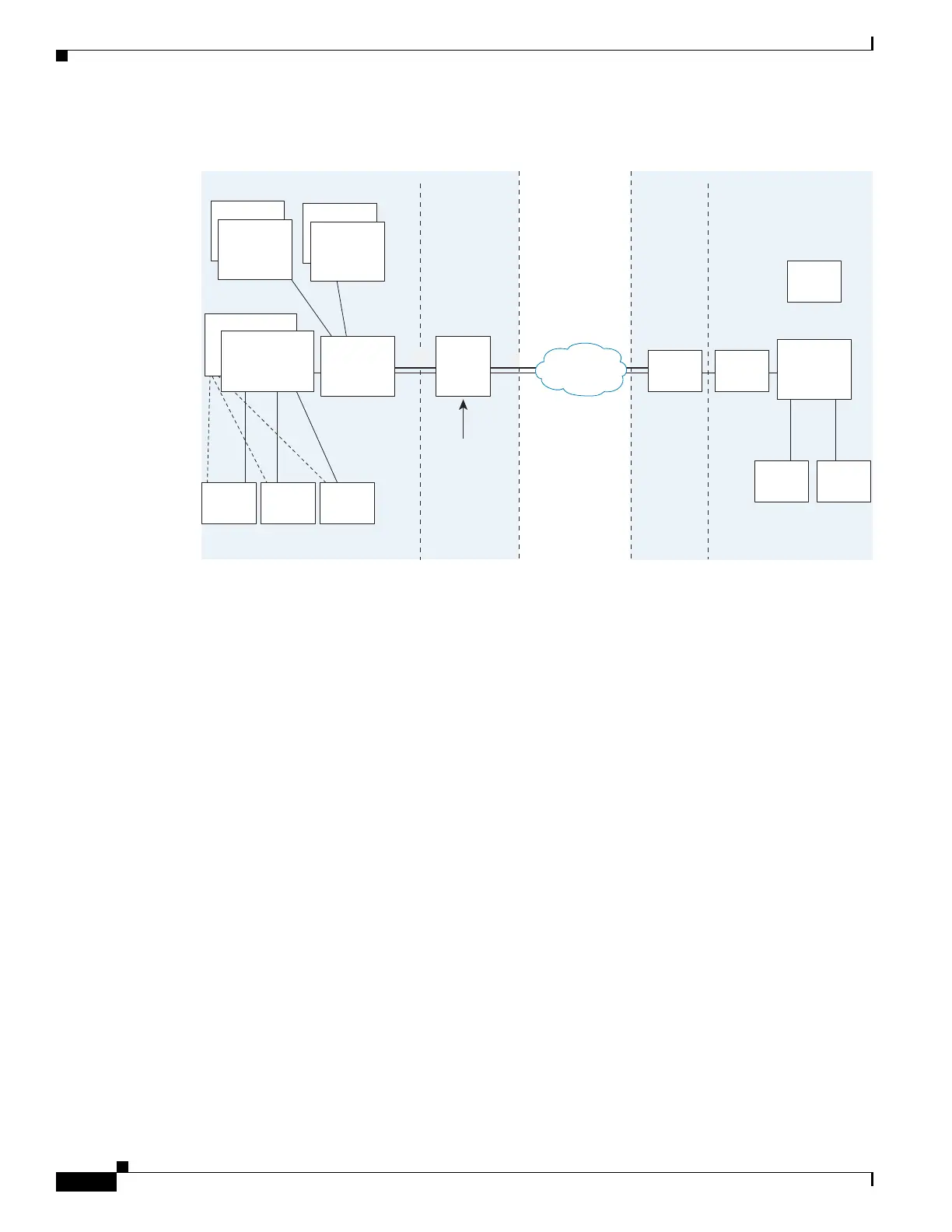
Figure 46-1 Typical Cisco Unified Presence/LCS Federation Scenario
In the above architecture, the adaptive security appliance functions as a firewall, NAT, and TLS proxy,
which is the recommended architecture. However, the adaptive security appliance can also function as
NAT and the TLS proxy alone, working with an existing firewall.
Either server can initiate the TLS handshake (unlike IP Telephony or Cisco Unified Mobility, where only
the clients initiate the TLS handshake). There are by-directional TLS proxy rules and configuration.
Each enterprise can have an adaptive security appliance as the TLS proxy.
In Figure 46-1, NAT or PAT can be used to hide the private address of Entity X. In this situation, static
NAT or PAT must be configured for foreign server (Entity Y) initiated connections or the TLS handshake
(inbound). Typically, the public port should be 5061. The following static PAT command is required for
the Cisco UP that accepts inbound connections:
hostname(config)# static (inside,outside) tcp 192.0.2.1 5061 10.0.0.2 5061 netmask
255.255.255.255
The following static PAT must be configured for each Cisco UP that could initiate a connection (by
sending SIP SUBSCRIBE) to the foreign server.
For Cisco UP with the address 10.0.0.2, enter the following command:
hostname(config)# static (inside,outside) tcp 192.0.2.1 5062 10.0.0.2 5062 netmask
255.255.255.255
hostname(config)# static (inside,outside) udp 192.0.2.1 5070 10.0.0.2 5070 netmask
255.255.255.255
hostname(config)# static (inside,outside) tcp 192.0.2.1 5060 10.0.0.2 5060 netmask
255.255.255.255
For another Cisco UP with the address 10.0.0.3, you must use a different set of PAT ports, such as 45062
or 45070:
hostname(config)# static (inside,outside) tcp 192.0.2.1 45061 10.0.0.3 5061 netmask
255.255.255.255
271637
SIP
Internet
Cisco
UP
(US)
Cisco UCM
Cisco
UP
(UK)
Cisco UCM
Cisco
UP
(HK)
Cisco UCM
ASA
8.0.4
LCS
AD
DMZ DMZ
Enterprise X Enterprise Y
private private network
Routing
Proxy
(
Cisco
UP)
192.0.2.1
192.0.2.254
10.0.0.2
Access
Proxy
LCS
Director
MOC
(Yao)
UC
(Ann)
Orative
(Ann)
IPPM
(Ann)
MOC
(Zak)
Outside
Functions as:
• TLS Proxy
• NAT w/SIP
rewrite
• Firewall
Inside

 Loading...
Loading...