47-4
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 47 Configuring Cisco Intercompany Media Engine Proxy
Information About Cisco Intercompany Media Engine Proxy
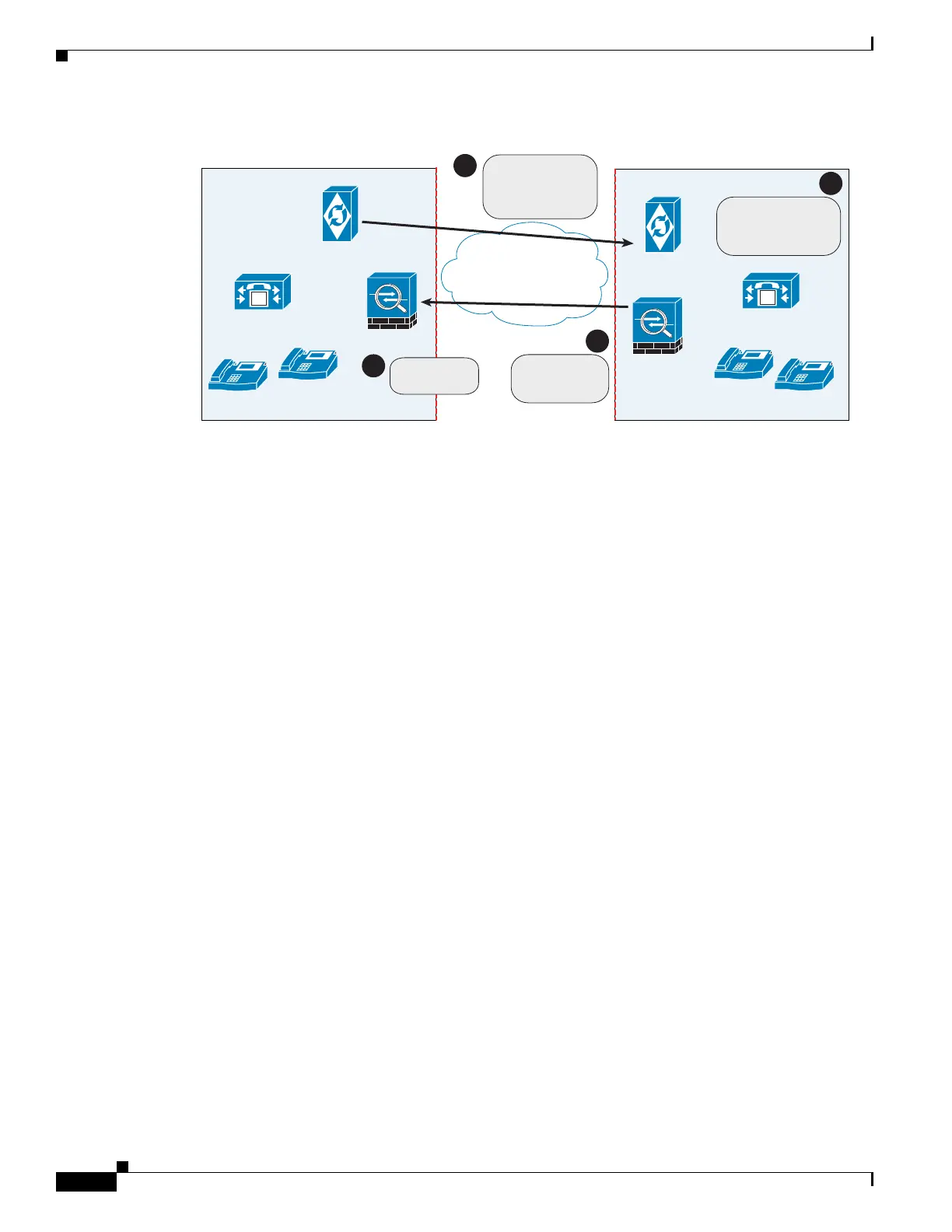
Figure 47-2 Ticket Verification Process with Cisco Intercompany Media Engine
As illustrated in Figure 47-2. Enterprise B makes a PSTN call to enterprise A. That call completes
successfully. Later, Enterprise B Cisco Intercompany Media Engine server initiates validation
procedures with Enterprise A. These validation procedures succeed. During the validation handshake,
Enterprise B sends Enterprise A its domain name. Enterprise A verifies that this domain name is not on
the blacklisted set of domains. Assuming it is not, Enterprise A creates a ticket.
Subsequently, someone in Enterprise B calls that number again. That call setup message from Enterprise
B to Enterprise A includes the ticket in the X-Cisco-UC-IME-Ticket header field in the SIP INVITE
message. This message arrives at the Enterprise A adaptive security appliance. The adaptive security
appliance verifies the signature and computes several checks on the ticket to make sure it is valid. If the
ticket is valid, the adaptive security appliance forwards the request to Cisco UCM (including the ticket).
Because the adaptive security appliance drops requests that lack a valid ticket, unauthorized calls are
never received by Cisco UCM.
The ticket password is a 128 bit random key, which can be thought of as a shared password between the
adaptive security appliance and the Cisco Intercompany Media Engine server. This password is
generated by the Cisco Intercompany Media Engine server and is used by a Cisco Intercompany Media
Engine SIP trunk to generate a ticket to allow a call to be made between Cisco Intercompany Media
Engine SIP trunks. A ticket is a signed object that contains a number of fields that grant permission to
the calling domain to make a Cisco Intercompany Media Engine call to a specific number. The ticket is
signed by the ticket password.
The Cisco Intercompany Media Engine also required that you configure an epoch for the password. The
epoch contains an integer that updates each time that the password is changed. When the proxy is
configured the first time and a password entered for the first time, enter 1 for the epoch integer. Each
time you change the password, increment the epoch to indicate the new password. You must increment
the epoch value each time your change the password.
Typically, you increment the epoch sequentially; however, the adaptive security appliance allows you to
choose any value when you update the epoch. If you change the epoch value, the tickets in use at remote
enterprises become invalid. The incoming calls from the remote enterprises fallback to the PSTN until
the terminating enterprise reissues tickets with the new epoch value and password.
The epoch and password that you configure on the adaptive security appliance must match the epoch and
password configured on the Cisco Intercompany Media Engine server. If you change the password or
epoch on the adaptive security appliance, you must update them on the Cisco Intercompany Media
Engine server. See the Cisco Intercompany Media Engine server documentation for information.
Enterprise A
Cisco UCM
M
Enterprise B
IP
IP
IP
IP
Internet
Cisco UCM
M
ASA
ASA
Enterprise B gets
authorization ticket
from A at end of
validation protocol
UC-IME server passes
ticket to UCM and it’s
stored as part of VoIP
route
248761
1
2
Enterprise B
calls A and
includes ticket
3
ASA validates
ticket
4
UC-IME
Server
UC-IME
Server

 Loading...
Loading...