54-3
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 54 Configuring the IPS Application on the AIP SSM and SSC
Information About the AIP SSM and SSC
most secure because every packet that you identify for inspection is analyzed before being allowed
through. Also, the AIP SSM/SSC can implement a blocking policy on a packet-by-packet basis. This
mode, however, can affect throughput.
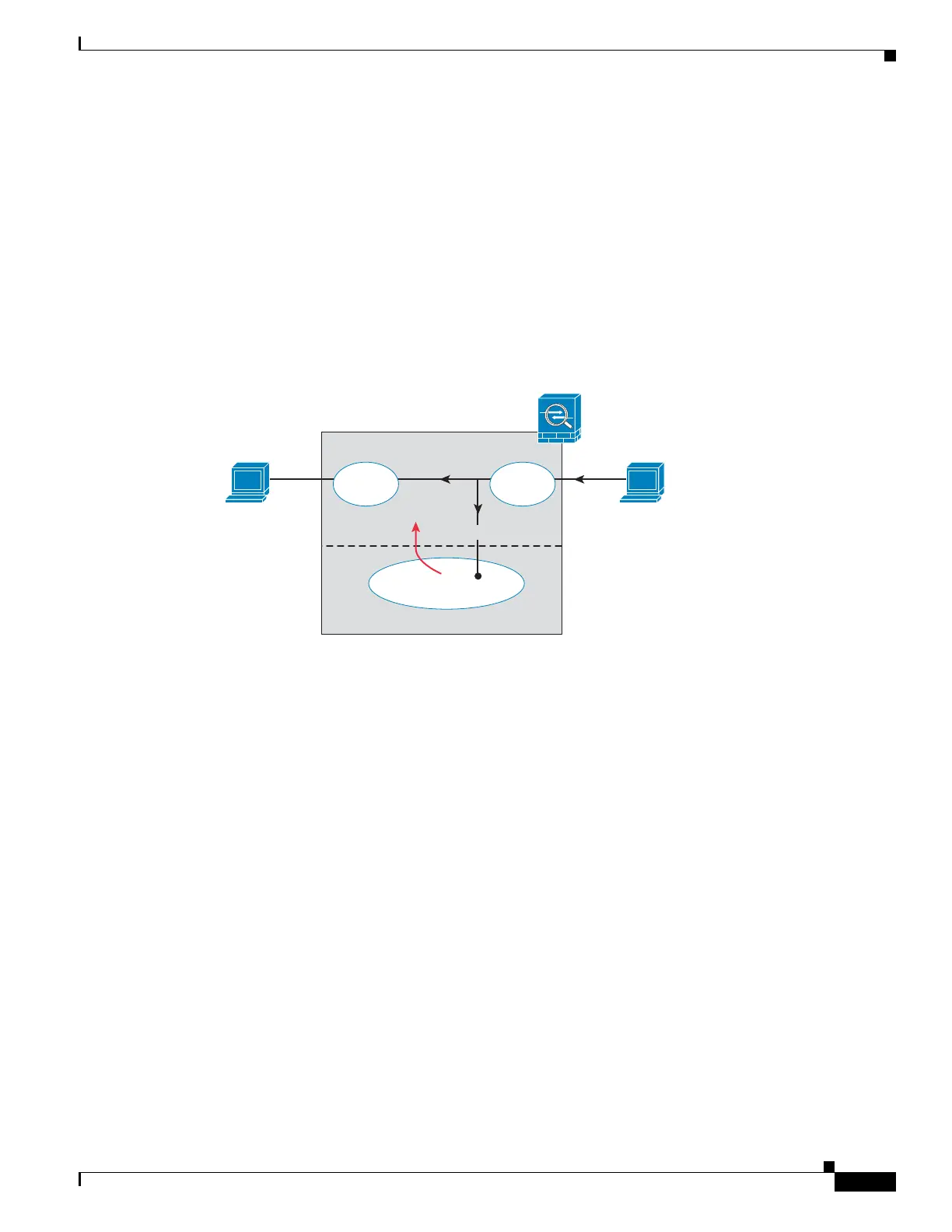
• Promiscuous mode—This mode sends a duplicate stream of traffic to the AIP SSM/SSC. This mode
is less secure, but has little impact on traffic throughput. Unlike the inline mode, in promiscuous
mode the AIP SSM/SSC can only block traffic by instructing the adaptive adaptive security
appliance to shun the traffic or by resetting a connection on the adaptive adaptive security appliance.
Also, while the AIP SSM/SSC is analyzing the traffic, a small amount of traffic might pass through
the adaptive adaptive security appliance before the AIP SSM/SSC can shun it. Figure 54-2 shows
the AIP SSM/SSC in promiscuous mode. In this example, the AIP SSM/SSC sends a shun message
to the adaptive security appliance for traffic it identified as a threat.
Figure 54-2 AIP SSM/SSC Traffic Flow in the Adaptive Security Appliance: Promiscuous Mode
Using Virtual Sensors (AIP SSM Only)
The AIP SSM running IPS software Version 6.0 and above can run multiple virtual sensors, which means
you can configure multiple security policies on the AIP SSM. You can assign each context or single
mode adaptive security appliance to one or more virtual sensors, or you can assign multiple security
contexts to the same virtual sensor. See the IPS documentation for more information about virtual
sensors, including the maximum number of sensors supported.
Figure 54-3 shows one security context paired with one virtual sensor (in inline mode), while two
security contexts share the same virtual sensor.
Security Appliance
Main System
inside
AIP SSM/SSC
IPS inspection
outside
Backplane
VPN
Policy
Firewall
Policy
Shun
message
251158
Copied Traffic

 Loading...
Loading...