65-4
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 65 Configuring Dynamic Access Policies
Understanding VPN Access Policies
Step 2 To create a new dynamic access policy, click Add. To modify an existing policy, click Edit.
Step 3 To test already configured polices, click Test Dynamic Access Policies.
Fields
• Priority—Displays the priority of the DAP record. The adaptive security appliance uses this value
to logically sequence the access lists when aggregating the network and web-type ACLs from
multiple DAP records. The adaptive security appliance orders the records from highest to lowest
priority number, with lowest at the bottom of the table. Higher numbers have a higher priority, that
is a DAP record with a value of 4 has a higher priority than a record with a value of 2. You cannot
manually sort them.
• Name—Displays the name of the DAP record.
• Network ACL List—Displays the name of the firewall access list that applies to the session.
• Web-Type ACL List—Displays the name of the SSL VPN access list that applies to the session.
• Description—Describes the purpose of the DAP record.
• Test Dynamic Access Policies button—Click to test already configured DAP records.
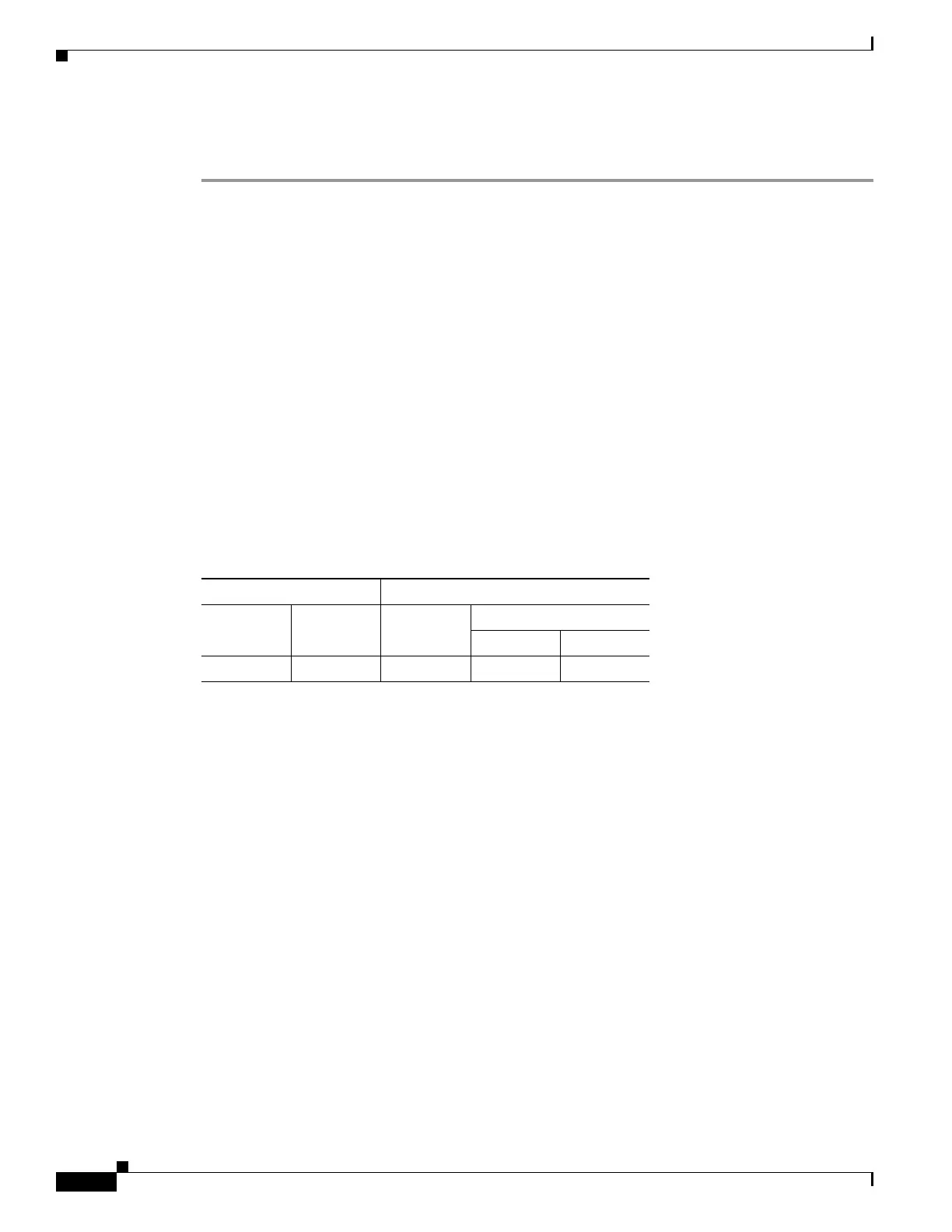
Modes
The following table shows the modes in which this feature is available:
DAP Support for Remote Access Connection Types
The DAP system supports the following remote access methods:
• IPsec VPN
• Clientless (browser-based) SSLVPN
• Cisco AnyConnect SSL VPN
• PIX cut-through proxy (posture assessment not available)
DAP and AAA
DAP complements AAA services. It provides a limited set of authorization attributes that can override
those AAA provides. The adaptive security appliance selects DAP records based on the AAA
authorization information for the user and posture assessment information for the session. The adaptive
security appliance can select multiple DAP records depending on this information, which it then
aggregates to create DAP authorization attributes.
You can specify AAA attributes from the Cisco AAA attribute hierarchy, or from the full set of response
attributes that the adaptive security appliance receives from a RADIUS or LDAP server. For more
information about DAP and AAA, see the section, Add/Edit AAA Attributes.
Firewall Mode Security Context
Routed Transparent Single
Multiple
Context System
•••——

 Loading...
Loading...