65-7
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 65 Configuring Dynamic Access Policies
Understanding VPN Access Policies
DAP and AntiVirus, AntiSpyware, and Personal Firewall Programs
The security appliance uses a DAP policy when the user attributes matches the configured AAA and
endpoint attributes. The Prelogin Assessment and Host Scan modules of Cisco Secure Desktop return
information to the security appliance about the configured endpoint attributes, and the DAP subsystem
uses that information to select a DAP record that matches the values of those attributes.
Most, but not all, antivirus, antispyware, and personal firewall programs support active scan, which
means that the programs are memory-resident, and therefore always running. Host Scan checks to see if
an endpoint has a program installed, and if it is memory-resident as follows:
• If the installed program does not support active scan, Host Scan reports the presence of the software.
The DAP system selects DAP records that specify the program.
• If the installed program does support active scan, and active scan is enabled for the program, Host
Scan reports the presence of the software. Again the security appliance selects DAP records that
specify the program.
• If the installed program does support active scan and active scan is disabled for the program, Host
Scan ignores the presence of the software. The security appliance does not select DAP records that
specify the program. Further, the output of the debug trace command, which includes a lot of
information about DAP, does not indicate the program presence, even though it is installed.
DAP Connection Sequence
The following sequence outlines a typical remote access connection establishment.
1. A remote client attempts a VPN connection.
2. The adaptive security appliance performs posture assessment, using configured NAC and Cisco
Secure Desktop Host Scan values.
3. The adaptive security appliance authenticates the user via AAA. The AAA server also returns
authorization attributes for the user.
4. The adaptive security appliance applies AAA authorization attributes to the session, and establishes
the VPN tunnel.
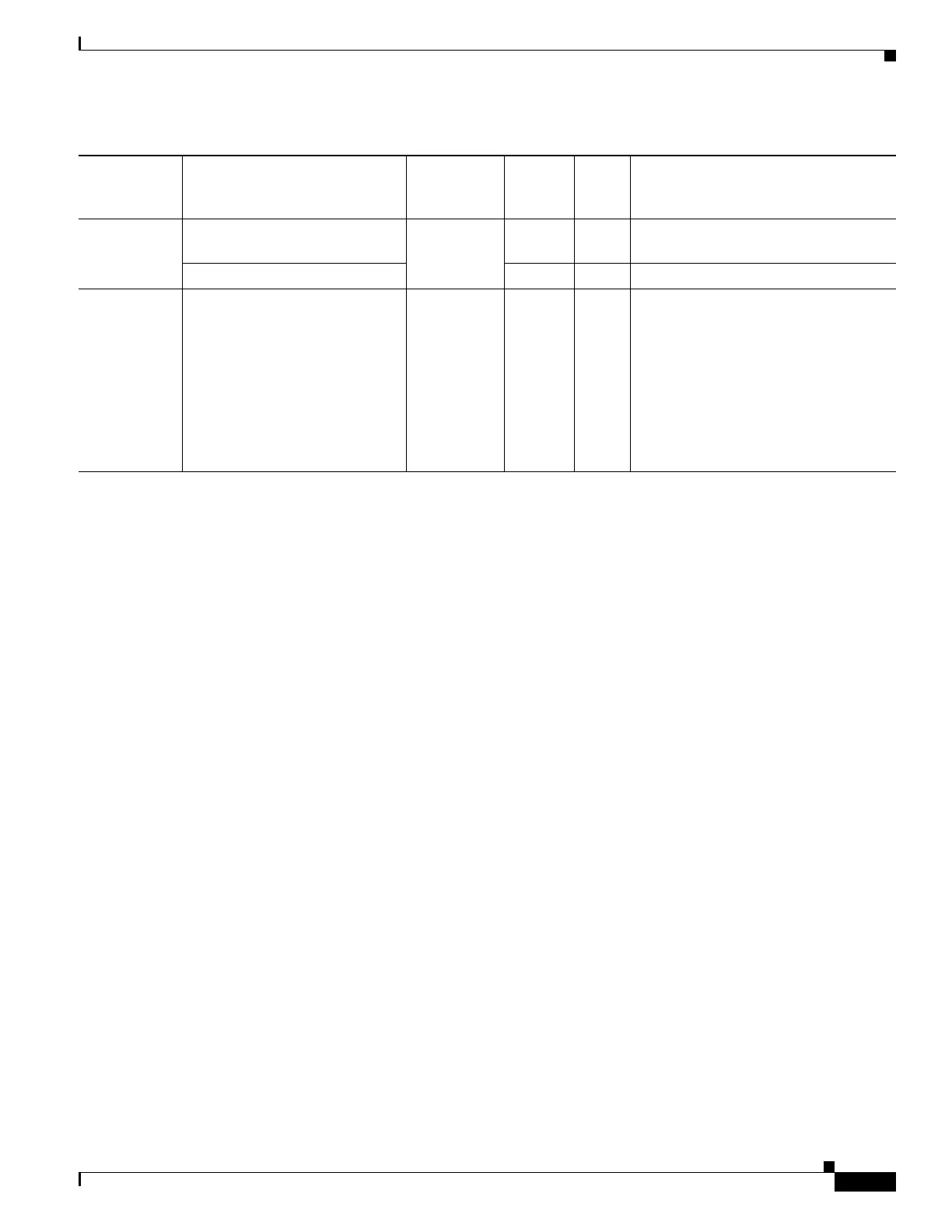
Registry endpoint.registry["label"].type Secure
Desktop
dword
string
—dword
endpoint.registry["label"].value string 255 Value of the registry entry
VLAN endoint.vlan.type CNA string — VLAN type:
ACCESS
AUTH
ERROR
GUEST
QUARANTINE
ERROR
STATIC
TIMEOUT
Table 65-3 Endpoint Attribute Definitions (continued)
Attribute Type Attribute Name Source Value
Max
String
Length Description

 Loading...
Loading...