B-28
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Appendix B Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
Enforcing Logon Hours and Time-of-Day Rules
In this use case we configure and enforce the hours that a clientless SSL user is allowed to access the
network. A good example of this is when you want to allow a business partner access to the network
only during normal business hours.
For this case, on the AD server, we use the Office field to enter the name of the partner. This field uses
the physicalDeliveryOfficeName attribute. Then we create an attribute map on the adaptive security
appliance to map that attribute to the Cisco attribute Access-Hours. During authentication, the adaptive
security appliance retrieves the value of physicalDeliveryOfficeName (the Office field) and maps it to
Access-Hours.
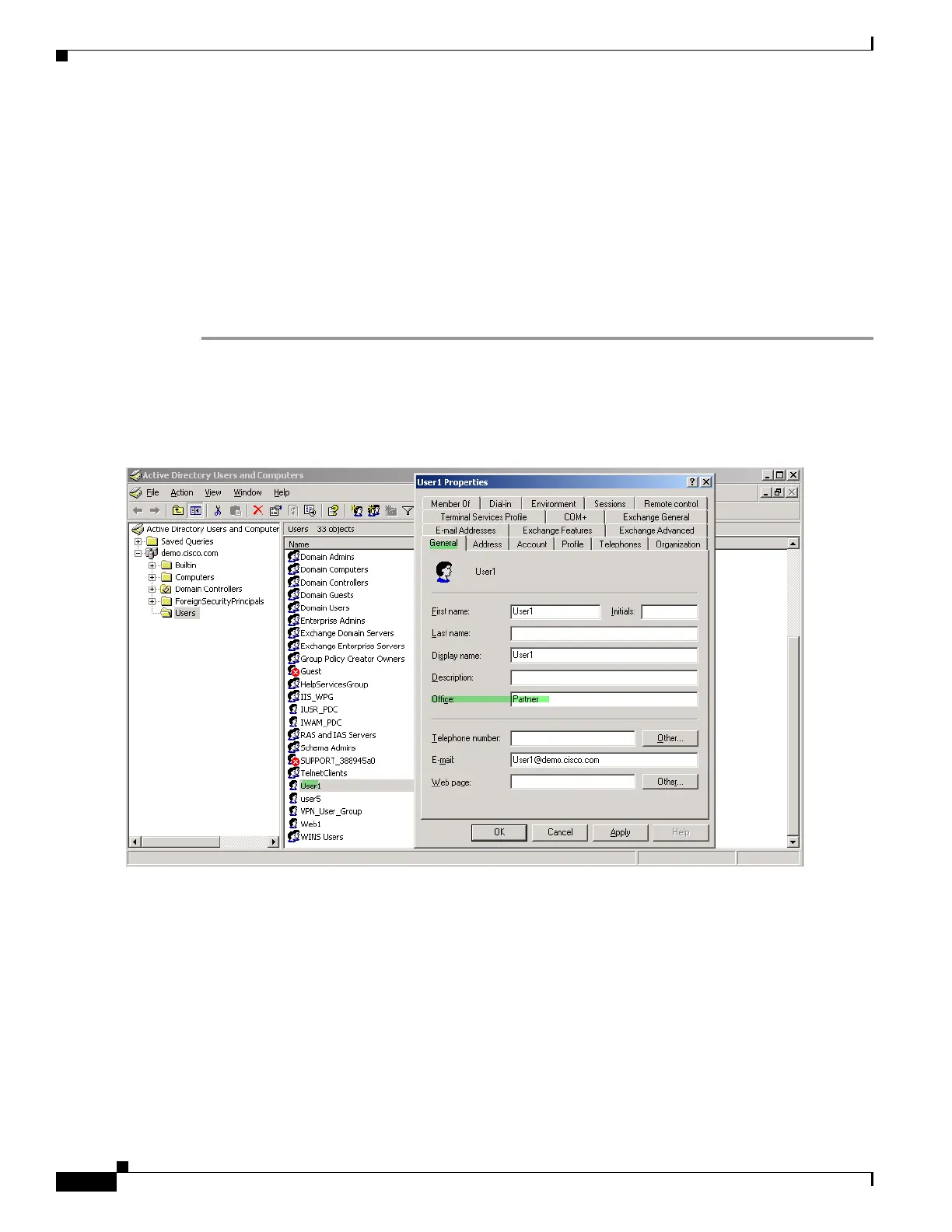
Step 1 Configure the user attributes on the AD LDAP server.
Select the user. Right click on Properties. The Properties window displays (Figure B-12). For this case,
we use the Office field of the General tab:
Figure B-12 Active Directory - Time-range
Step 2
Create an attribute map.
In this case we create the attribute map access_hours and map the AD attribute
physicalDeliveryOfficeName used by the Office field to the Cisco attribute Access-Hours.
For example:
hostname(config)# ldap attribute-map access_hours
hostname(config-ldap-attribute-map)# map-name physicalDeliveryOfficeName Access-Hours
Step 3 Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 3.3.3.4, in the AAA
server group MS_LDAP, and associates the attribute map access_hours that you created in step 2:
hostname(config)# aaa-server MS_LDAP host 3.3.3.4

 Loading...
Loading...