44-4
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 44 Configuring the TLS Proxy for Encrypted Voice Inspection
Prerequisites for the TLS Proxy for Encrypted Voice Inspection
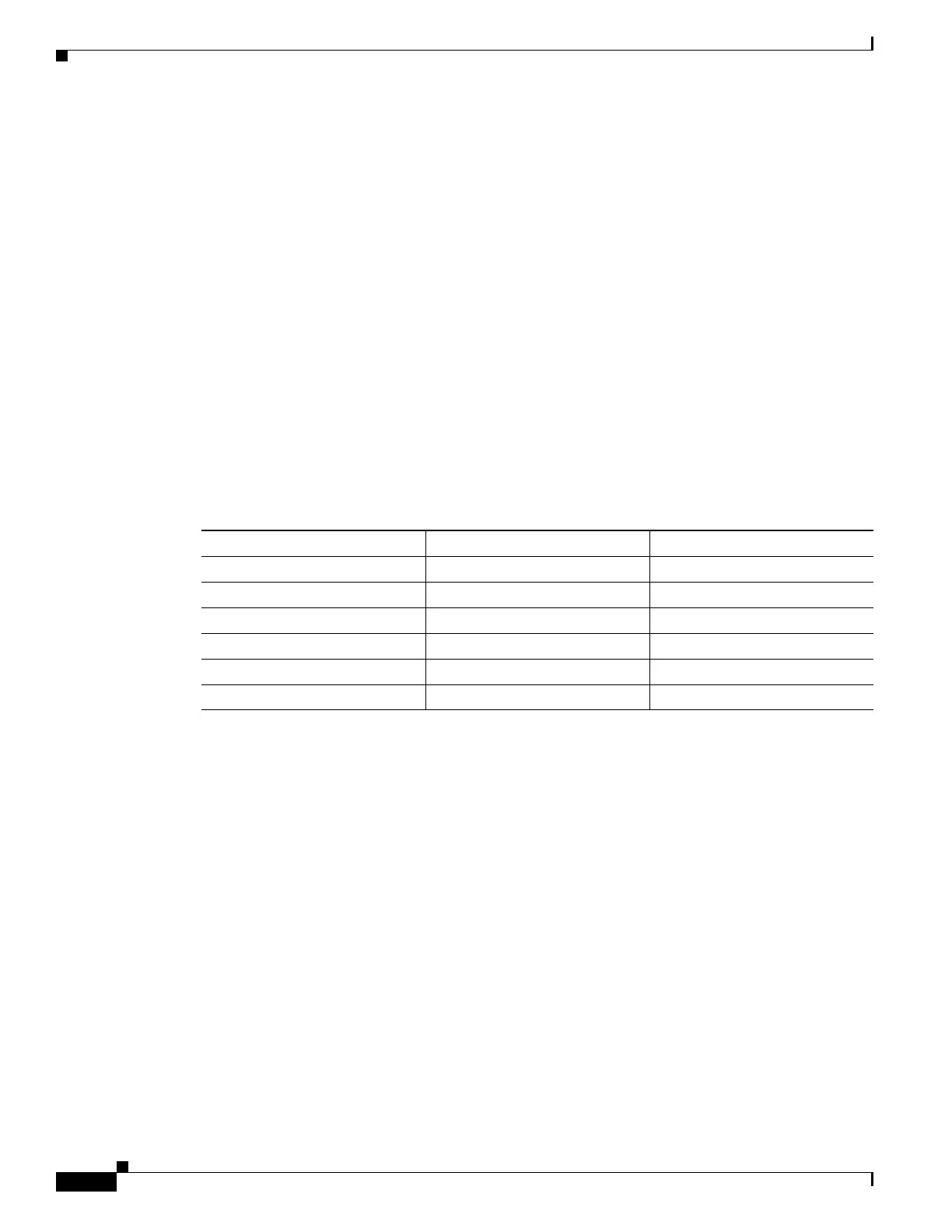
Table 44-1 shows the default and maximum TLS session details by platform.
For more information about licensing, see Chapter 4, “Managing Feature Licenses.”
Prerequisites for the TLS Proxy for Encrypted Voice Inspection
Before configuring TLS proxy, the following prerequisites are required:
• You must set clock on the security appliance before configuring TLS proxy. To set the clock
manually and display clock, use the clock set and show clock commands. We recommend that the
security appliance use the same NTP server as the Cisco Unified CallManager cluster. TLS
handshake may fail due to certificate validation failure if clock is out of sync between the security
appliance and the Cisco Unified CallManager server.
• 3DES-AES license is needed to interoperate with the Cisco Unified CallManager. AES is the default
cipher used by the Cisco Unified CallManager and Cisco IP Phone.
• Import the following certificates which are stored on the Cisco UCM. These certificates are required
by the adaptive security appliance for the phone proxy.
–
Cisco_Manufacturing_CA
–
CAP-RTP-001
1. Phone Proxy, Presence Federation Proxy, and Encrypted Voice Inspection applications use TLS proxy sessions for their connections. Each TLS proxy
session is counted against the UC license limit. All of these applications are licensed under the UC Proxy umbrella, and can be mixed and matched. Some
applications might use multiple sessions for a connection. For example, if you configure a phone with a primary and backup Cisco Unified
Communications Manager, there are 2 TLS proxy connections, so 2 UC Proxy sessions are used.
Note: Mobility Advantage Proxy does not require a license, and its TLS proxy sessions do not count towards the UC license limit.
The maximum number of UC sessions you can use also depends on the TLS proxy session limit:
- For license part numbers ending in “K8” (for example, licenses under 250 users), TLS proxy sessions are limited to 1000.
- For license part numbers ending in “K9” (for example, licenses 250 users or larger), the TLS proxy limit depends on your configuration and the platform
model. To configure the TLS proxy limit, use the Configuration > Firewall > Unified Communications > TLS Proxy pane.
Note: K8 and K9 refer to whether the license is restricted for export: K8 is unrestricted, and K9 is restricted.
You might also use SRTP encryption sessions for your connections:
- For K8 licenses, SRTP sessions are limited to 250.
- For K9 licenses, there is not limit.
Note: Only calls that require encryption/decryption for media are counted towards the SRTP limit; if passthrough is set for the call, even if both legs are
SRTP, they do not count towards the limit.
2. With the 10,000-session license, the total combined sessions can be 10,000, but the maximum number of Phone Proxy sessions is 5000.
Table 44-1 Default and Maximum TLS Sessions on the Security Appliance
Security Appliance Platform Default TLS Sessions Maximum TLS Sessions
ASA 5505 10 80
ASA 5510 100 200
ASA 5520 300 1200
ASA 5540 1000 4500
ASA 5550 2000 4500
ASA 5580 4000 13,000

 Loading...
Loading...