EMBEDDED Intel486™ PROCESSOR HARDWARE REFERENCE MANUAL
5-2
cle takes place. Note that this cycle occurs regardless of the state of the KEN# input. The KEN#
input’s function is discussed in the next section.
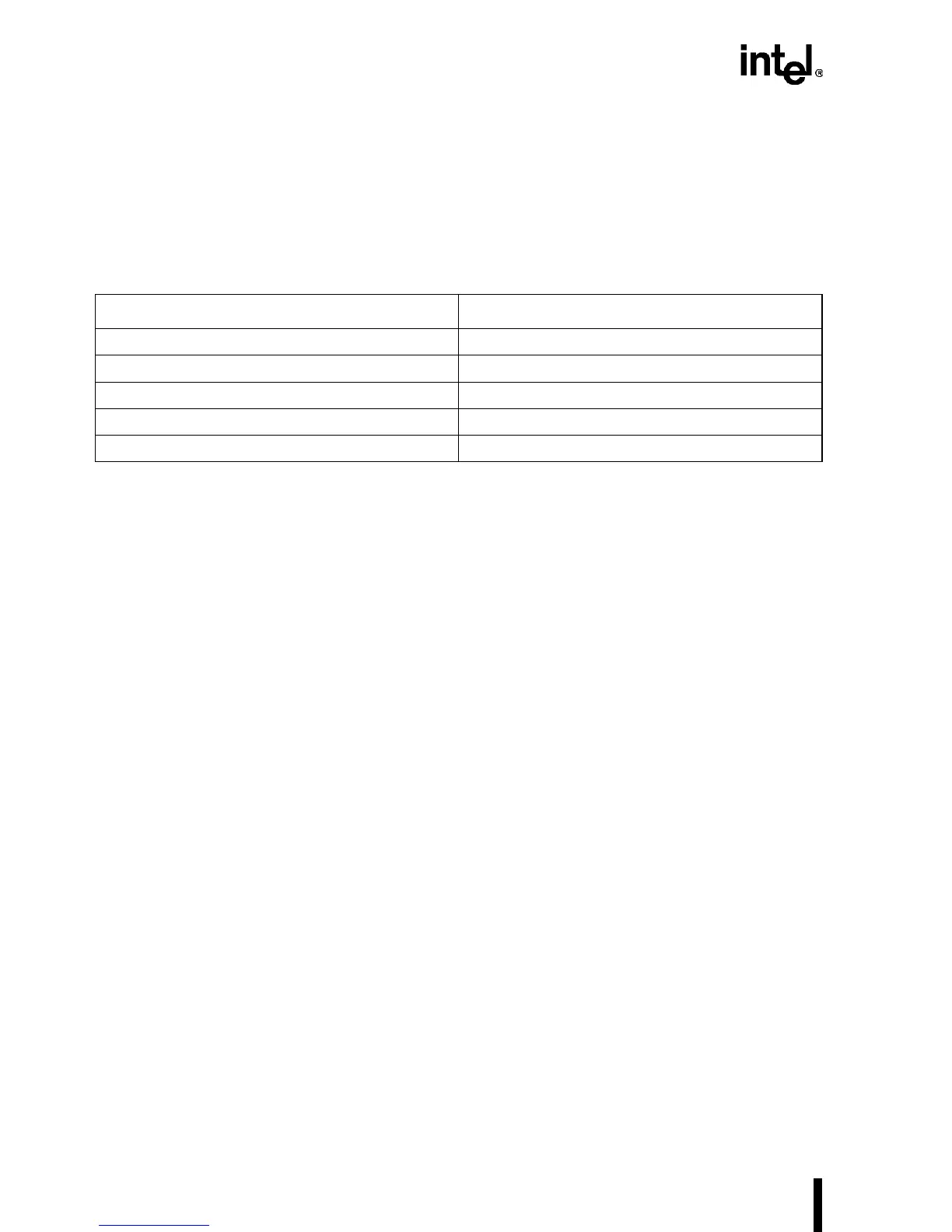
With this definition we see that several cases are included as “burstable.” Some examples of
burstable cycles are listed in Table 5-1. These cycle lengths are shown in bytes to clarify the case
listed.
The last two cases show that write cycles are burstable. In the last case a write cycle is transferred
on an 8- or 16-bit bus. If BRDY# is returned to terminate this cycle, the CPU generates another
write cycle without activating ADS#.
Using the burst write feature has debatable performance benefit. Some systems may implement
special functions that benefit from the use of burst writes. However, the Intel486 processor does
not write cache lines. Therefore, all write cycles are 4 bytes long. Most of the devices that use
dynamic bus sizing are read-only. This fact further reduces the utility of burst writes.
Due to these facts, a memory subsystem design normally does not implement burst write cycles.
The BRDY# input is asserted only during main memory read cycles. RDY# is used to terminate
all memory write cycles. RDY# is also used for all cycles that are not in the memory subsystem
or are not capable of supporting burst cycles. The RDY# input is used, for example, to terminate
an EPROM or I/O cycle.
5.2.2 The KEN# Input
The primary purpose of the KEN# input is to determine whether a cycle is to be cached. Only
read data and code cycles can be cached. Therefore, these cycles are the only cycles affected by
the KEN# input.
Figure 5-1 shows a typical burst cycle. In this sequence, the value of KEN# is important in two
different places. First, to begin a cacheable cycle, KEN# must be active the clock before BRDY#
is returned. Second, KEN# is sampled the clock before BLAST# is active. At this time the CPU
determines whether this line is written to the cache.
The state of KEN# also determines when read cycles can be burst. Most read cycles are initiated
as 4 bytes long from the processor’s cache unit. When KEN# is sampled active, the clock before
BRDY# or RDY# is asserted, the cycle is converted to a 16-byte cache line fill by the bus unit.
This way, a cycle which would not have been burst can now be burst by activating BRDY#.
Some read cycles can be burst without activating KEN#. The most prevalent example of this type
of read cycle is a code fetch. All code fetches are generated as 16-byte cycles from the processor’s
Table 5-1. Access Length of Typical CPU Functions
Bus Cycle Size (Bytes)
All code fetches 16
Descriptor loads 8
Cacheable reads 16
Floating-point operand loads 8
Bus size 8 (16) writes 4 (Max)
 Loading...
Loading...











