46-4
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 46 Configuring Cisco Unified Presence
Information About Cisco Unified Presence
For the TLS handshake, the two entities could validate the peer certificate via a certificate chain to
trusted third-party certificate authorities. Both entities enroll with the CAs. The adaptive security
appliance as the TLS proxy must be trusted by both entities. The adaptive security appliance is always
associated with one of the enterprises. Within that enterprise (Enterprise X in Figure 46-1), the entity
and the adaptive security appliance could authenticate each other via a local CA, or by using self-signed
certificates.
To establish a trusted relationship between the adaptive security appliance and the remote entity (Entity
Y), the adaptive security appliance can enroll with the CA on behalf of Entity X (Cisco UP). In the
enrollment request, the Entity X identity (domain name) is used.
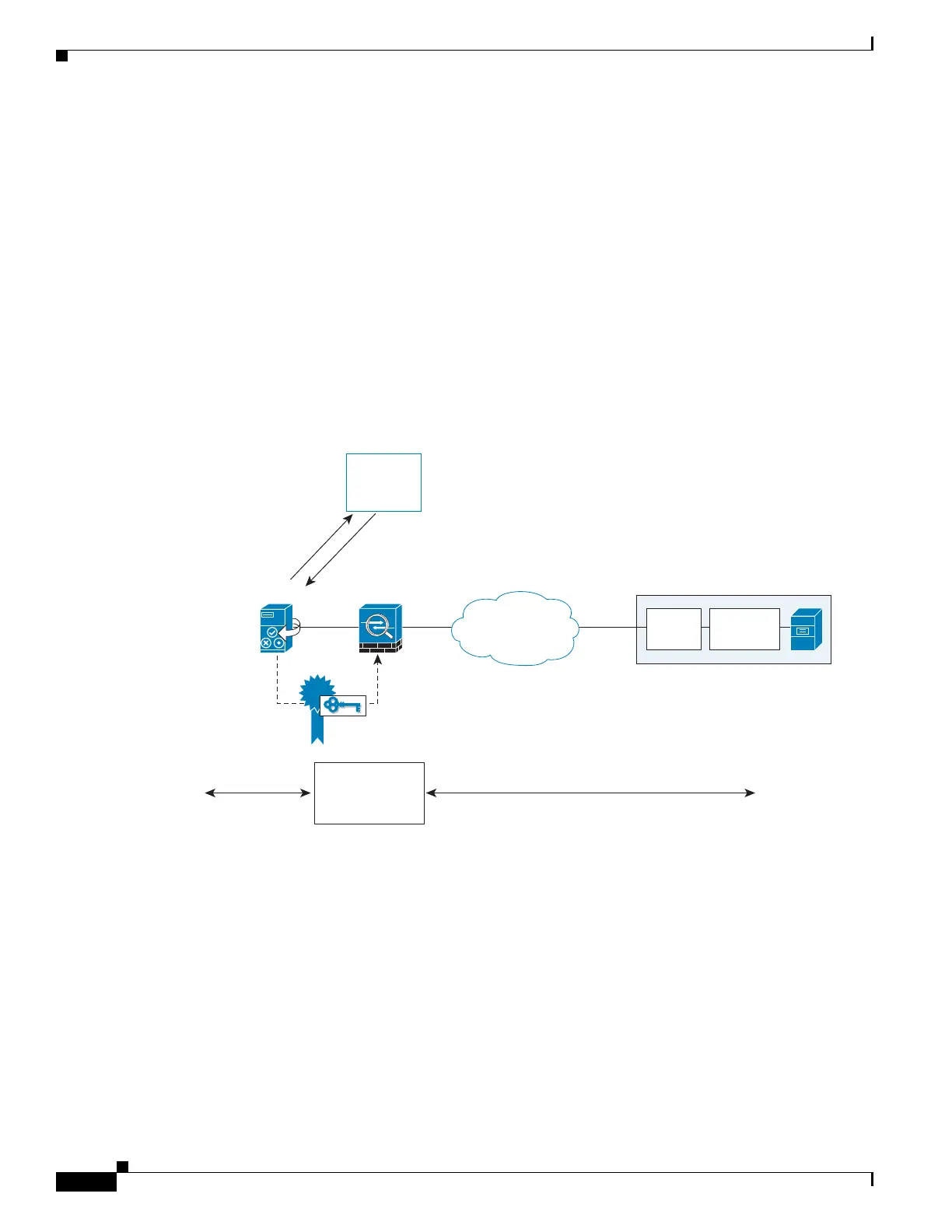
Figure 46-3 shows the way to establish the trust relationship. The adaptive security appliance enrolls
with the third party CA by using the Cisco UP FQDN as if the adaptive security appliance is the Cisco
UP.
Figure 46-3 How the Security Appliance Represents Cisco Unified Presence – Certificate
Impersonate
Security Certificate Exchange Between Cisco UP and the Security Appliance
You need to generate the keypair for the certificate (such as cup_proxy_key) used by the adaptive
security appliance, and configure a trustpoint to identify the self-signed certificate sent by the adaptive
security appliance to Cisco UP (such as
cup_proxy) in the TLS handshake.
For the adaptive security appliance to trust the Cisco UP certificate, you need to create a trustpoint to
identify the certificate from the Cisco UP (such as
cert_from_cup), and specify the enrollment type as
terminal to indicate that you will paste the certificate received from the Cisco UP into the terminal.
271639
Internet
Access
Proxy
LCS/OCS
Director
Inspected and
Modified
(if needed)
Certificate
Authority
Certificate
Certificate with
Private Key
ASA
Cisco UP
Enroll with FQDN
of Cisco UP
Microsoft Presence Server
Key 1
Key 2
TLS (Self-signed,
or from local CA)
TLS (Cisco UP Certificate)
3rd Party CA

 Loading...
Loading...