51-3
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 51 Configuring Threat Detection
Configuring Basic Threat Detection Statistics
Types of Traffic Monitored
Only through-the-box traffic is monitored; to-the-box traffic is not included in threat detection.
Default Settings
Basic threat detection statistics are enabled by default.
Table 51-1 lists the default settings. You can view all these default settings using the show
running-config all threat-detection command in Tools > Command Line Interface.
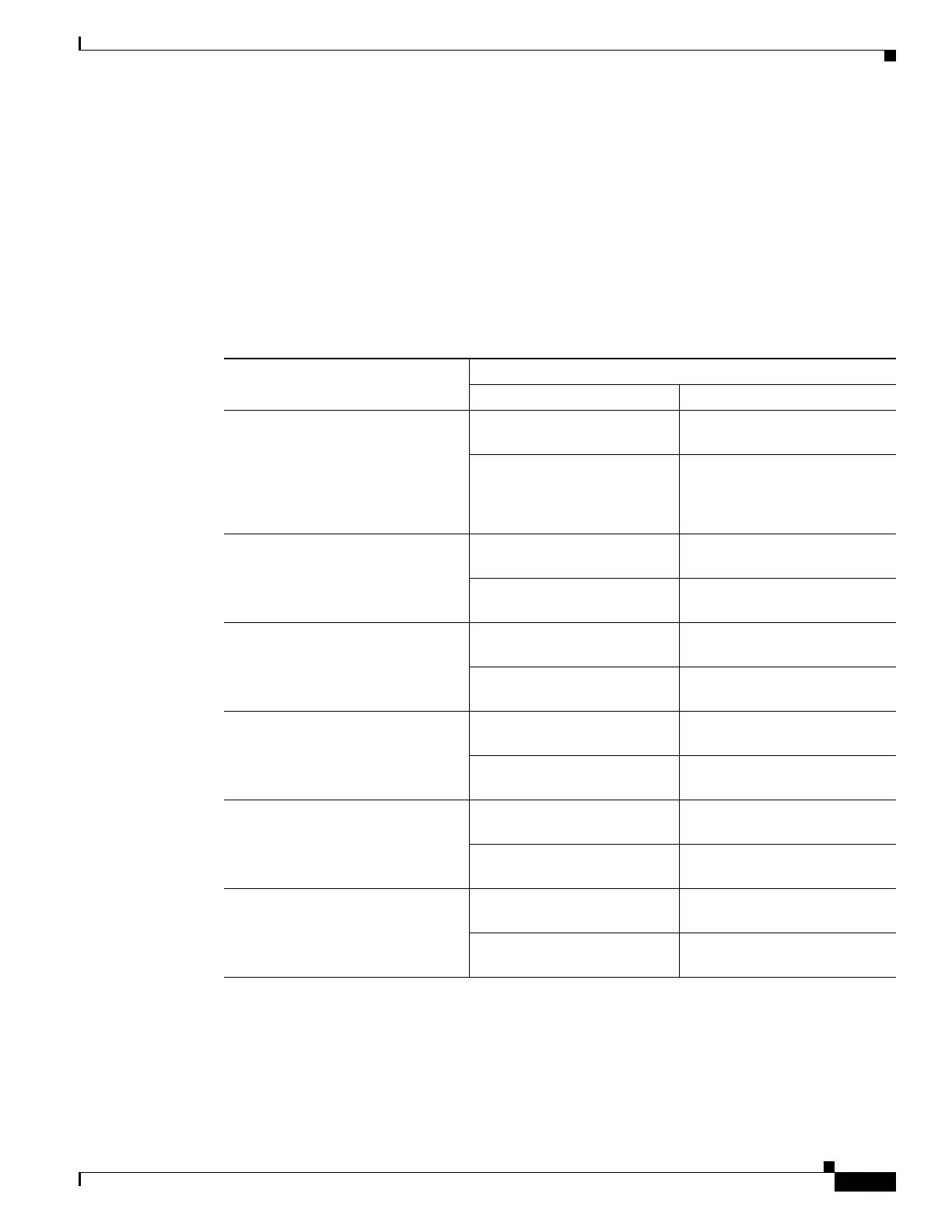
Table 51-1 Basic Threat Detection Default Settings
Packet Drop Reason
Trigger Settings
Average Rate Burst Rate
• DoS attack detected
• Bad packet format
• Connection limits exceeded
• Suspicious ICMP packets
detected
100 drops/sec over the last 600
seconds.
400 drops/sec over the last 10
second period.
80 drops/sec over the last 3600
seconds.
320 drops/sec over the last 60
second period.
Scanning attack detected 5 drops/sec over the last 600
seconds.
10 drops/sec over the last 10
second period.
4 drops/sec over the last 3600
seconds.
8 drops/sec over the last 60
second period.
Incomplete session detected such as
TCP SYN attack detected or no data
UDP session attack detected
(combined)
100 drops/sec over the last 600
seconds.
200 drops/sec over the last 10
second period.
80 drops/sec over the last 3600
seconds.
160 drops/sec over the last 60
second period.
Denial by access lists 400 drops/sec over the last 600
seconds.
800 drops/sec over the last 10
second period.
320 drops/sec over the last
3600 seconds.
640 drops/sec over the last 60
second period.
• Basic firewall checks failed
• Packets failed application
inspection
400 drops/sec over the last 600
seconds.
1600 drops/sec over the last 10
second period.
320 drops/sec over the last
3600 seconds.
1280 drops/sec over the last 60
second period.
Interface overload 2000 drops/sec over the last
600 seconds.
8000 drops/sec over the last 10
second period.
1600 drops/sec over the last
3600 seconds.
6400 drops/sec over the last 60
second period.

 Loading...
Loading...