28-19
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 28 Configuring Twice NAT
Configuration Examples for Twice NAT
• Different Translation Depending on the Destination (Dynamic PAT), page 28-19
• Different Translation Depending on the Destination Address and Port (Dynamic PAT), page 28-28
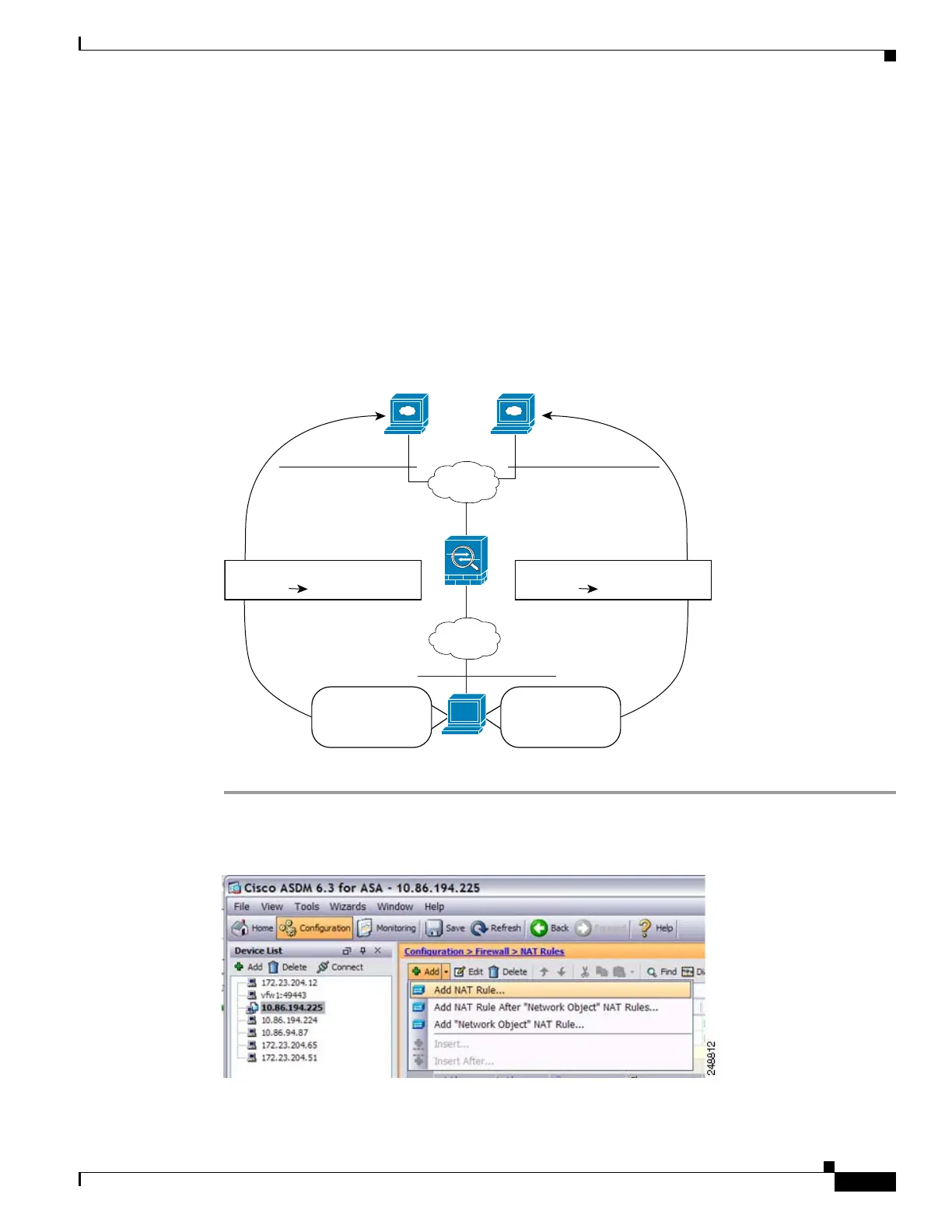
Different Translation Depending on the Destination (Dynamic PAT)
Figure 28-29 shows a host on the 10.1.2.0/24 network accessing two different servers. When the host
accesses the server at 209.165.201.11, the real address is translated to 209.165.202.129:port. When the
host accesses the server at 209.165.200.225, the real address is translated to 209.165.202.130:port.
Figure 28-29 Twice NAT with Different Destination Addresses
Step 1 Add a NAT rule for traffic from the inside network to DMZ network 1:
Figure 28-30 Adding a NAT Rule
Server 1
209.165.201.11
Server 2
209.165.200.225
DMZ
Inside
10.1.2.27
10.1.2.0/24
130039
209.165.201.0/27 209.165.200.224/27
Translation
209.165.202.12910.1.2.27
Translation
209.165.202.13010.1.2.27
Packet
Dest. Address:
209.165.201.11
Packet
Dest. Address:
209.165.200.225

 Loading...
Loading...