5: Monitoring & Filtering
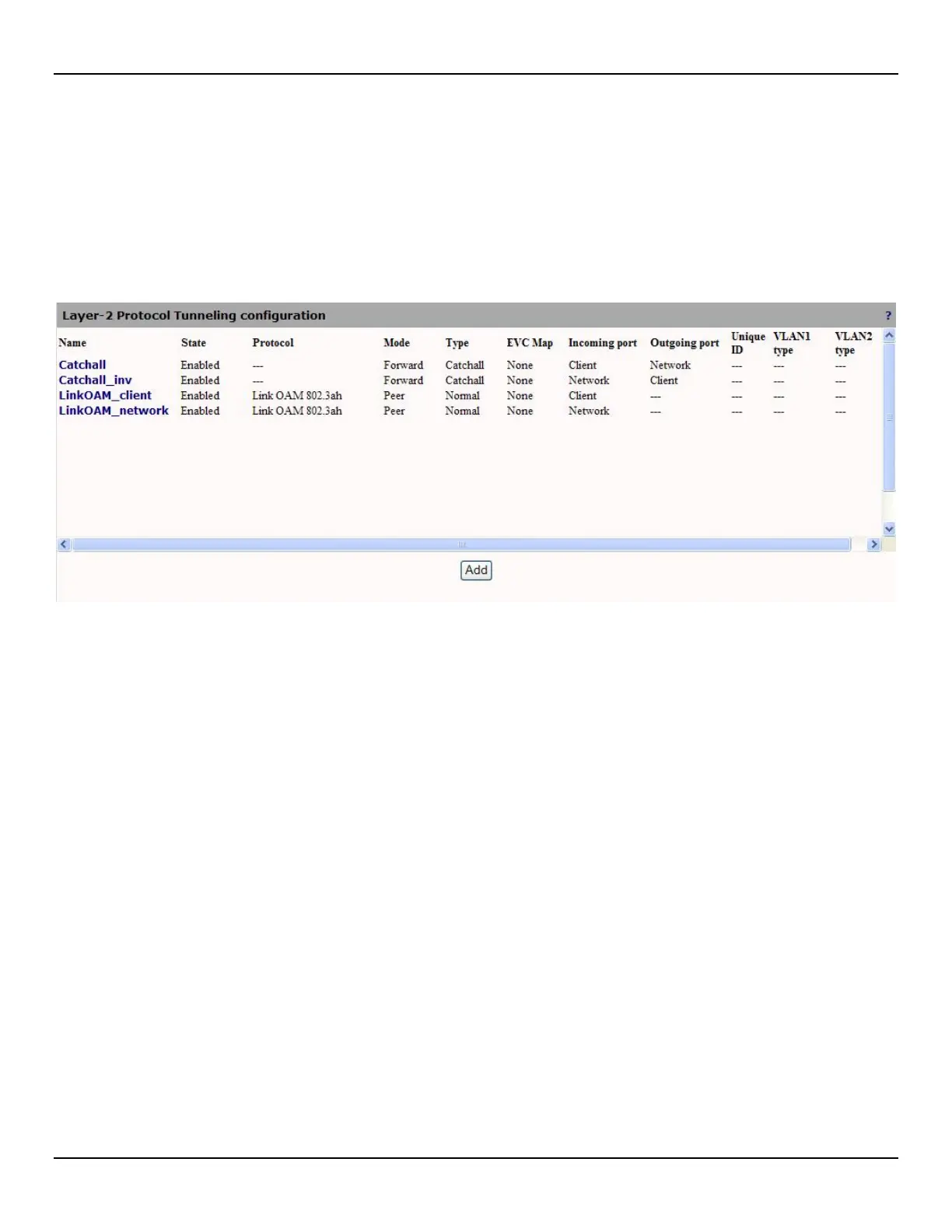
Layer-2 Protocol Tunneling
The Layer-2 Protocol Tunneling feature allows the customer's layer-2 control protocol (L2CP) frames to be transparently
transported across an EVC without interfering with the carrier/operator network and equipment. The protocol tunneling
operates by replacing the protocol's specific destination MAC address with a multicast address that is transparently
transported by the transit equipment, and reinserting the original destination MAC when the traffic reaches the destination
equipment. A total of 64 L2PT rules can be defined.
Name
Unique name assigned to the rule.
State
The state of the rule, enabled or disabled.
Protocol
The Layer-2 Control Protocol to be processed by the rule.
Mode
The current mode of operation of the rule. Four modes of operation are available:
Drop: frames matching the specific rule are dropped.
Forwarding: frames are sent unaltered from the incoming to the outgoing port. Optionally, EVC mapping can be enabled
on forwarding rules (see below).
Tunneling: frames matching the specific rule get their destination MAC address replaced by the MAC specified in the
rule's parameters when ingressing the specified client port. Frames matching the specific rule get their original
destination MAC address put back when ingressing the specified network port.
Peering: the frames are sent to software layers for further processing.
Type
The type of the rule, normal or catchall.
 Loading...
Loading...