35-5
Catalyst 3750-E and 3560-E Switch Software Configuration Guide
OL-9775-08
Chapter 35 Configuring Network Security with ACLs
Understanding ACLs
As with port ACLs, the switch examines ACLs associated with features configured on a given interface.
However, router ACLs are supported in both directions. As packets enter the switch on an interface,
ACLs associated with all inbound features configured on that interface are examined. After packets are
routed and before they are forwarded to the next hop, all ACLs associated with outbound features
configured on the egress interface are examined.
ACLs permit or deny packet forwarding based on how the packet matches the entries in the ACL, and
ca
n be used to control access to a network or to part of a network. In Figure 35-1, ACLs applied at the
router input allow Host A to access the Human Resources network, but prevent Host B from accessing
th
e same network.
VLAN Maps
Use VLAN ACLs or VLAN maps to access-control all traffic. You can apply VLAN maps to all packets
that are routed into or out of a VLAN or are bridged within a VLAN in the switch or switch stack.
Use VLAN maps for security packet filtering. VLAN maps are not defined by direction (input or output).
You can configure VLAN maps to match Layer 3 addresses for IPv4 traffic.
All non-IP protocols are access-controlled through MAC addresses and Ethertype using MAC VLAN
ma
ps. (IP traffic is not access controlled by MAC VLAN maps.) You can enforce VLAN maps only on
packets going through the switch; you cannot enforce VLAN maps on traffic between hosts on a hub or
on another switch connected to this switch.
With VLAN maps, forwarding of packets is permitted or denied, based on the action specified in the
ma
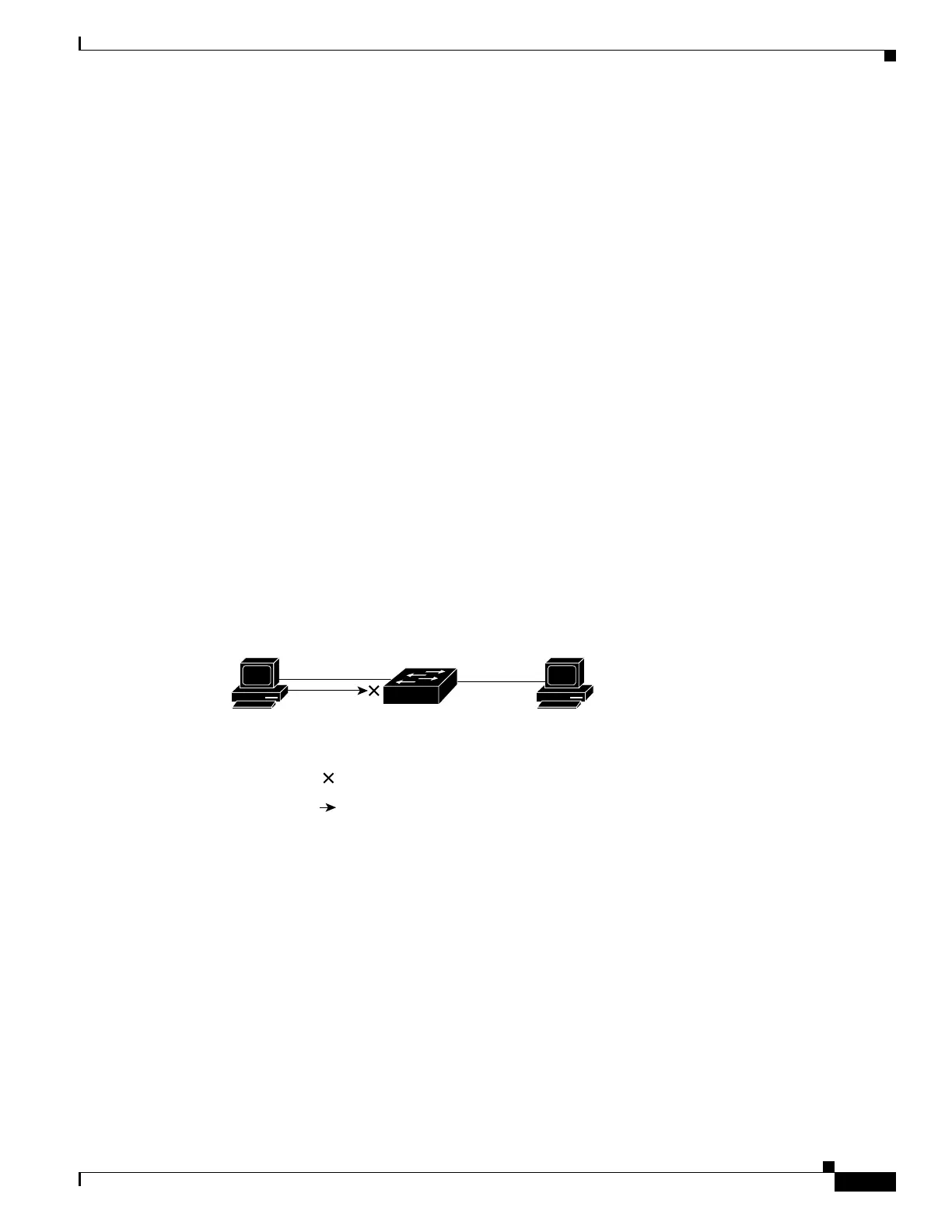
p. Figure 35-2 shows how a VLAN map is applied to prevent a specific type of traffic from Host A in
VLAN 10 from being forwarded. You can apply only one VLAN map to a VLAN.
Figure 35-2 Using VLAN Maps to Control Traffic
Handling Fragmented and Unfragmented Traffic
IP packets can be fragmented as they cross the network. When this happens, only the fragment
containing the beginning of the packet contains the Layer 4 information, such as TCP or UDP port
numbers, ICMP type and code, and so on. All other fragments are missing this information.
Some ACEs do not check Layer 4 information and therefore can be applied to all packet fragments. ACEs
th
at do test Layer 4 information cannot be applied in the standard manner to most of the fragments in a
fragmented IP packet. When the fragment contains no Layer 4 information and the ACE tests some
Layer 4 information, the matching rules are modified:
• Permit ACEs that check the Layer 3 information in the fragment (including protocol type, such as
TCP, UDP, and so on) are considered to match the fragment regardless of what the missing Layer 4
information might have been.
Host B
(VLAN 10)
Host A
(VLAN 10)
92919
= VLAN map denying specific type
of traffic from Host A
= Packet
 Loading...
Loading...











