AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 103
Profiles > IDS > Impersonation
Perform these steps to create IDS Impersonation profiles.
1. Click
Profiles > IDS > Impersonation in the Aruba Navigation pane.
2. Click the
Add button to create a new Impersonation profile, or click the pencil icon next to an existing
profile to edit. The
Details page appears. Complete the settings as described in Table 35:
3. Click
Add or Save. The added or edited Impersonation profile appears on the Profiles > IDS >
Impersonation
page.
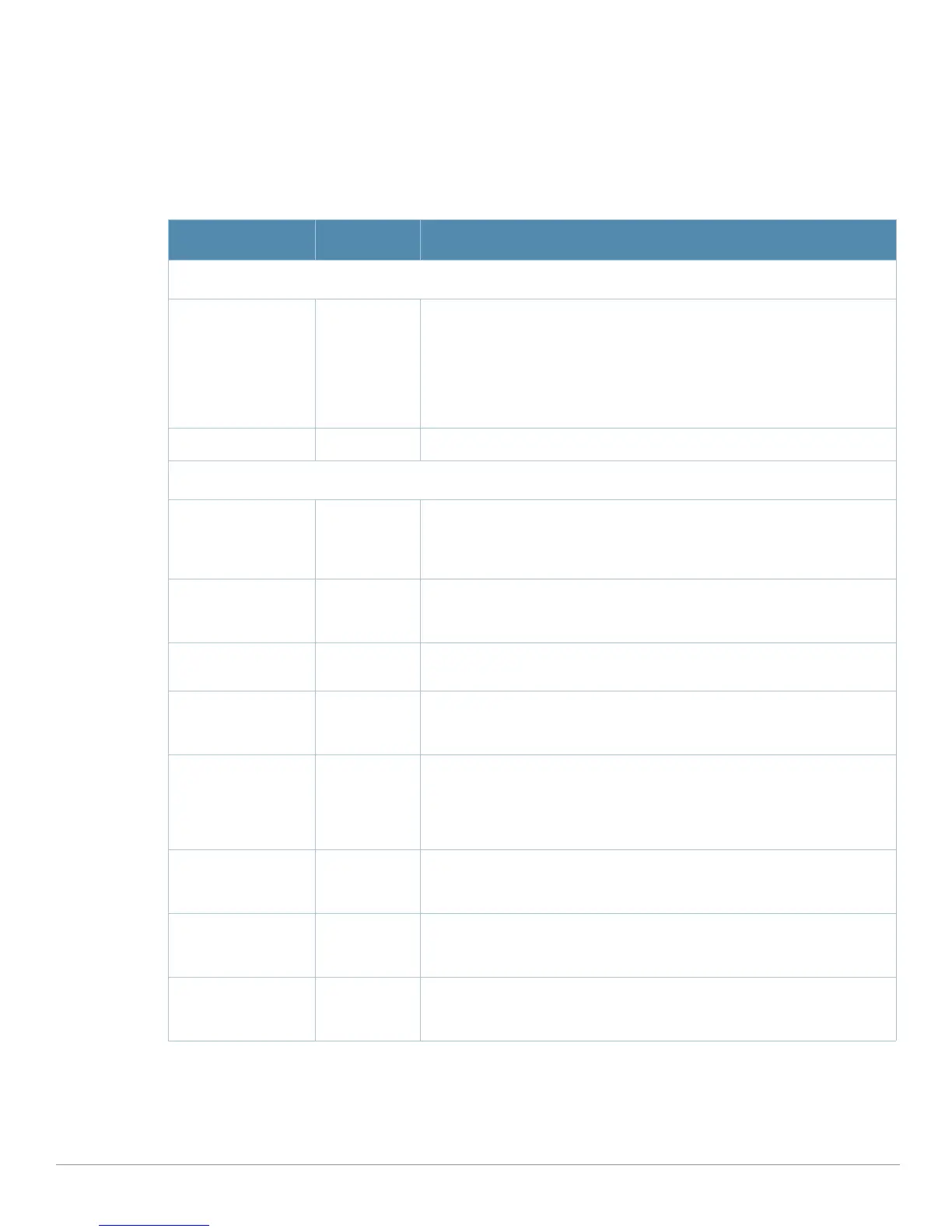
Table 35 Aruba Configuration > Profiles > IDS > Impersonation Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the impersonation profile.
Other Settings
Detect AP
Impersonation
Yes Enable or disable detection of AP impersonation. In AP impersonation
attacks, the attacker sets up an AP that assumes the BSSID and ESSID of
a valid AP. AP impersonation attacks can be done for man-in-the-middle
attacks, a rogue AP attempting to bypass detection, or a honeypot attack.
Protect from AP
Impersonation
No When AP impersonation is detected, use this control to set both the
legitimate and impersonating AP to be disabled using a denial of service
attack.
Beacon Diff
Threshold (0-100%)
50 Set the percentage increase in beacon rate that triggers an AP
impersonation event.
Beacon Increase
Wait Time
(0-360000 sec)
3 Set the time, in seconds, after the Beacon Diff Threshold is crossed before
an AP impersonation event is generated.
Detect Sequence
Anomaly
No Enable or disable detection of anomalies between sequence numbers
seen in 802.11 frames. During an impersonation attack, the attacker may
spoof the MAC address of a client or AP — if two devices are active on the
network with the same MAC address, the sequence numbers in the frames
will not match since the sequence number is generated by NIC firmware.
Sequence Number
of Difference
(0-100000)
300 Set the maximum allowable tolerance between sequence numbers within
the Sequence Number Time Tolerance period.
Sequence Number
Time Tolerance
(0-360000 sec)
300 Time, in seconds, during which sequence numbers must exceed the
Sequence Number Difference value for an alarm to be triggered.
Sequence Number
Quiet Time
(60-360000 sec)
900 After an alarm has been triggered, the time (in seconds) that must elapse
before another identical alarm may be triggered.

 Loading...
Loading...