AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 105
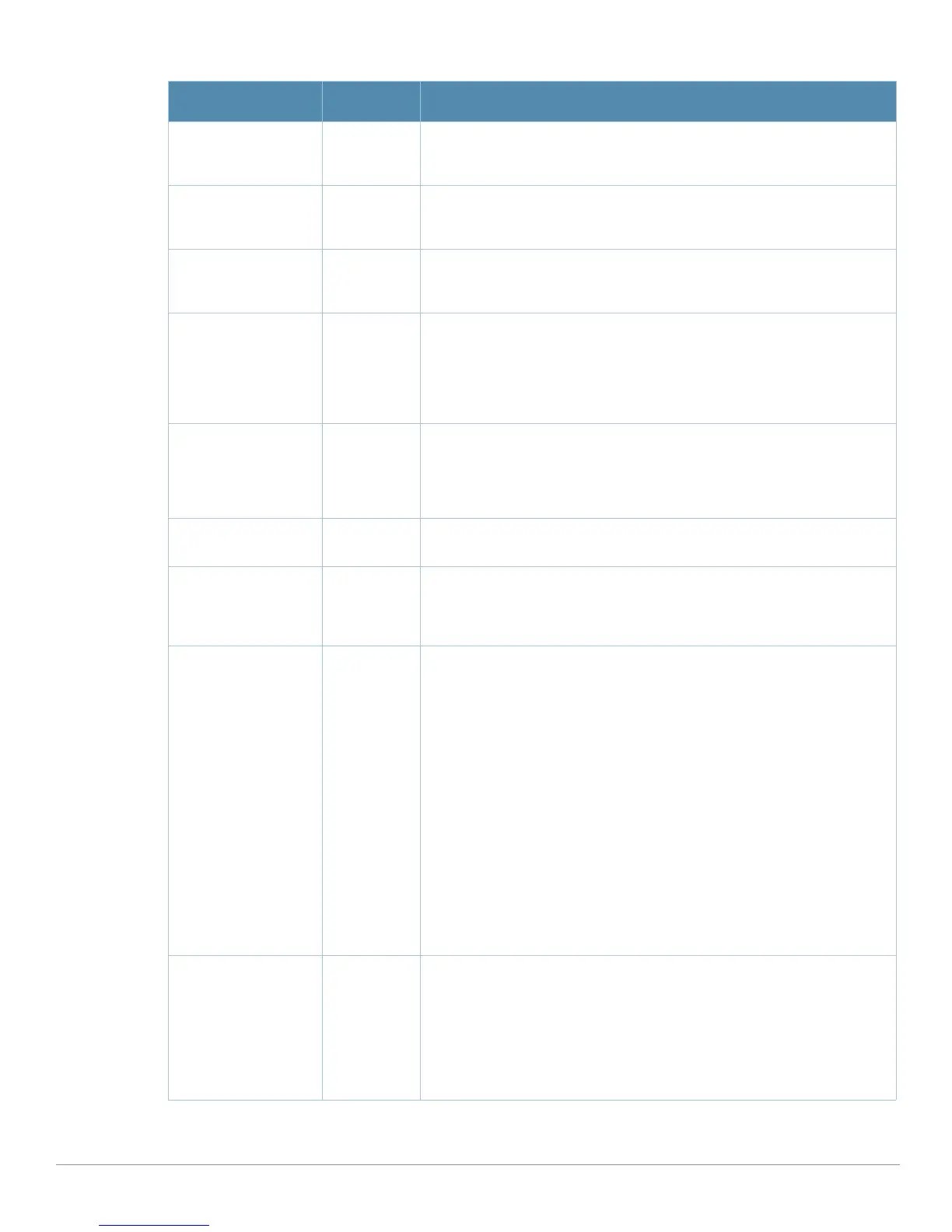
MAC OUI Detection
Quiet Time
(60-360000 sec)
900 Set the time, in seconds, that must elapse after an invalid MAC OUI alarm
has been triggered before another identical alarm may be triggered.
Adhoc Network
Detection Quiet Time
(60-360000 sec)
900 Set the time, in seconds, that must elapse after an adhoc network
detection alarm has been triggered before another identical alarm may be
triggered.
Wireless Bridge
Detection Quiet Time
(60-360000 sec)
900 Set the time, in seconds, that must elapse after a wired bridging alarm has
been triggered before another identical alarm may be triggered.
Rogue AP
Classification
Yes Enable or disable rogue AP classification. A rogue AP is one that is
unauthorized and plugged into the wired side of the network. Any other AP
seen in the RF environment that is not part of the valid enterprise network
is considered to be “interfering” — it has the potential to cause RF
interference but it is not connected to the wired network and thus does not
represent a direct threat.
Overlay Rogue AP
Classification
Yes Set Overlay Rogue Classification, which is classification through valid/
rogue APs. A controller uses the wired-mac table of other valid and rogue
APs as equivalents of the wired MACs that it sees on our network. When
this match is triggered, it makes a note of the AP that helped in this
process, and this info will be displayed as the Helper-AP.
Valid Wired MACs Blank Text
Field
Set a list of MAC addresses of wired devices in the network, typically
gateways or servers.
Rogue Containment No By default, rogue APs are only detected but are not automatically disabled.
This option automatically shuts down rogue APs. When this option is
enabled, clients attempting to associate to a rogue AP will be
disconnected from the rogue AP through a denial of service attack.
Allow Well Known
MAC
N/A Allow devices with known MAC addresses to classify rogues APs.
Depending on your network, configure one or more of the following
options for classifying rogue APs:
z hsrp—Routers configured for HSRP, a Cisco-proprietary redundancy
protocol, with the HSRP MAC OUI 00:00:0c.
z iana—Routers using the IANA MAC OUI 00:00:5e.
z local-mac—Devices with locally administered MAC addresses starting
with 02.
z vmware—Devices with any of the following VMWare OUIs: 00:0c:29,
00:05:69, or 00:50:56
z vmware1—Devices with VMWare OUI 00:0c:29.
z vmware2—Devices with VMWare OUI 00:05:69.
z vmware3—Devices with VMWare OUI 00:50:56.
If you modify an existing configuration, the new configuration overrides the
original configuration. For example, if you configure allow-well-
known-mac hsrp and then configure allow-well-known-mac iana,
the original configuration is lost.
Suspected Rogue
Containment
No Use this setting to treat suspected rogue APs as interfering APs; thereby
the controller attempts to reclassify them as rogue APs. By default,
suspected rogue APs are not automatically contained.
In combination with the suspected rogue containment confidence level,
this option automatically shuts down suspected rogue APs. When this
option is enabled, clients attempting to associate to a suspected rogue AP
will be disconnected from the suspected rogue AP through a denial of
service attack.
Table 36 Aruba Configuration > Profiles > IDS > Unauthorized Devices Profile Settings (Continued)
Field Default Description

 Loading...
Loading...