Version 7.0 131 Mediant 3000
User's Manual 11. Configuring SSL/TLS Certificates
11.5 Creating Self-Signed Certificates for TLS Contexts
The following procedure describes how to assign a certificate that is digitally signed by the
device itself to a TLS Context. In other words, the device acts as a CA.
To assign a self-signed certificate to a TLS Context:
1. Before you begin, make sure that:
• You have a unique DNS name for the device (e.g.,
dns_name.corp.customer.com). This name is used to access the device and
therefore, must be listed in the server certificate.
• No traffic is running on the device. The certificate generation process is disruptive
to traffic and should be done during maintenance time.
2. Open the TLS Contexts page (Configuration tab > System menu > TLS Contexts).
3. In the table, select the required TLS Context index row, and then click the TLS
Context Certificate button, located below the table; the Context Certificates page
appears.
4. Under the Certificate Signing Request group, in the 'Subject Name [CN]' field, enter
the fully-qualified DNS name (FQDN) as the certificate subject.
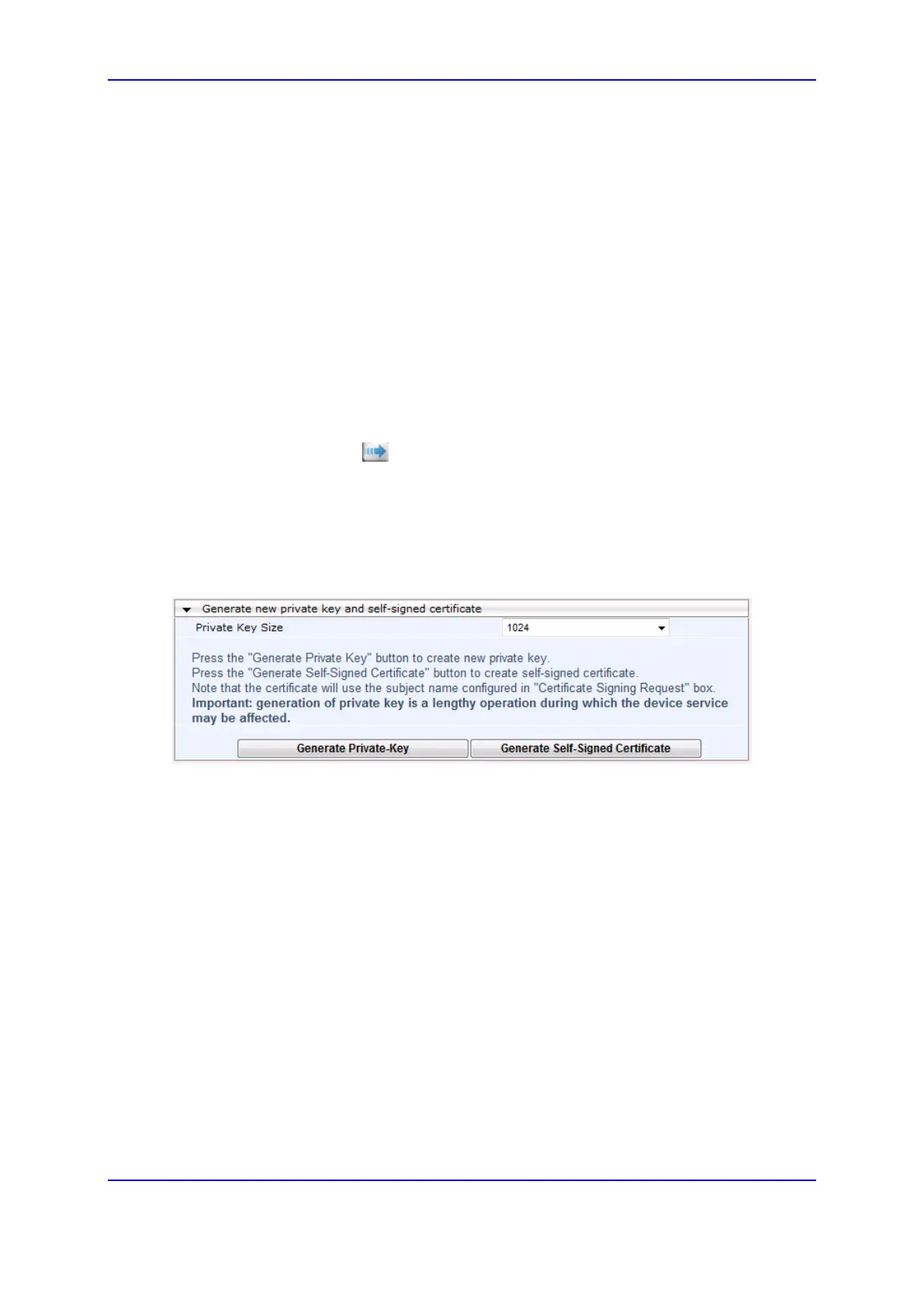
5. Scroll down the page to the Generate new private key and self-signed certificate
group:
Figure 11-7: Generate new private key and self-signed certificate Group
6. Click Generate Self-Signed Certificate; a message appears (after a few seconds)
displaying the new subject name.
7. Save the configuration with a device reset for the new certificate to take effect.

 Loading...
Loading...











