User's Manual 242 Document #: LTRT-89730
Mediant 3000
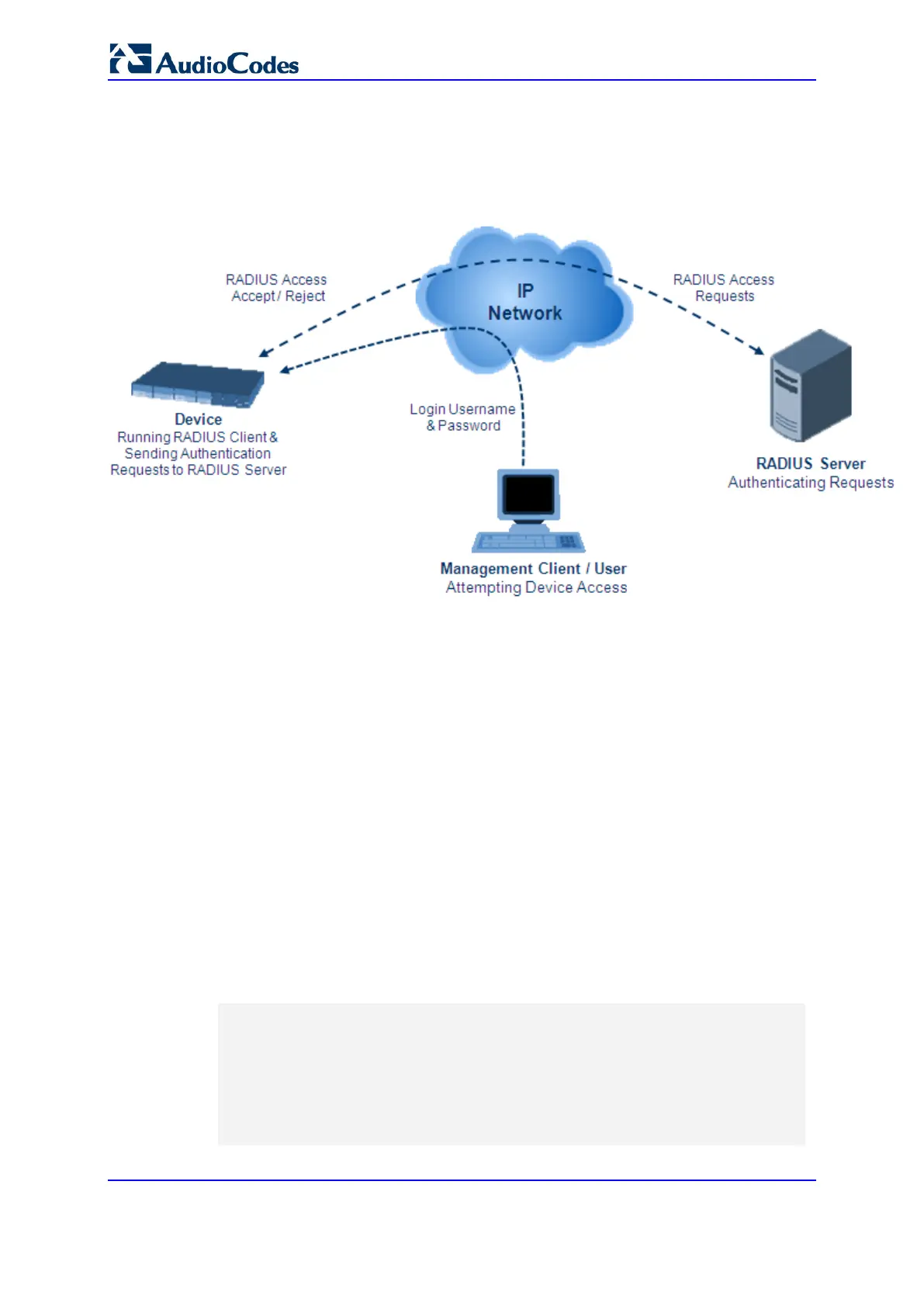
or a rejection notification. During the RADIUS authentication process, the device’s Web
interface is blocked until an acceptance response is received from the RADIUS server.
Note that communication between the device and the RADIUS server is done by using a
shared secret, which is not transmitted over the network.
Figure 16-3: RADIUS Login Authentication for Management
For using RADIUS, you need to do the following:
Set up a RADIUS server (third-party) to communicate with the device - see ''Setting
Up a Third-Party RADIUS Server'' on page
242
Configure the device as a RADIUS client for communication with the RADIUS server -
see ''Configuring RADIUS Authentication'' on page
243
16.2.5.1 Setting Up a Third-Party RADIUS Server
The following procedure provides an example for setting up a third-party RADIUS sever,
FreeRADIUS, which can be downloaded from www.freeradius.org. Follow the instructions
on this Web site for installing and configuring the server. If you use a RADIUS server from
a different vendor, refer to its appropriate documentation.
To set up a third-party RADIUS server (e.g., FreeRADIUS):
1. Define the device as an authorized client of the RADIUS server, with the following:
• Predefined shared secret (password used to secure communication between the
device and the RADIUS server)
• Vendor ID
Below is an example of the clients.conf file (FreeRADIUS client configuration):
#
# clients.conf - client configuration directives
#
client 10.31.4.47 {
secret = FutureRADIUS
shortname = audc_device
}

 Loading...
Loading...











