User's Manual 260 Document #: LTRT-89730
Mediant 3000
The following procedure describes how to configure the device's LDAP cache through the
Web interface. For a full description of the cache parameters, see ''LDAP Parameters'' on
page 1056.
To enable and configure the LDAP cache:
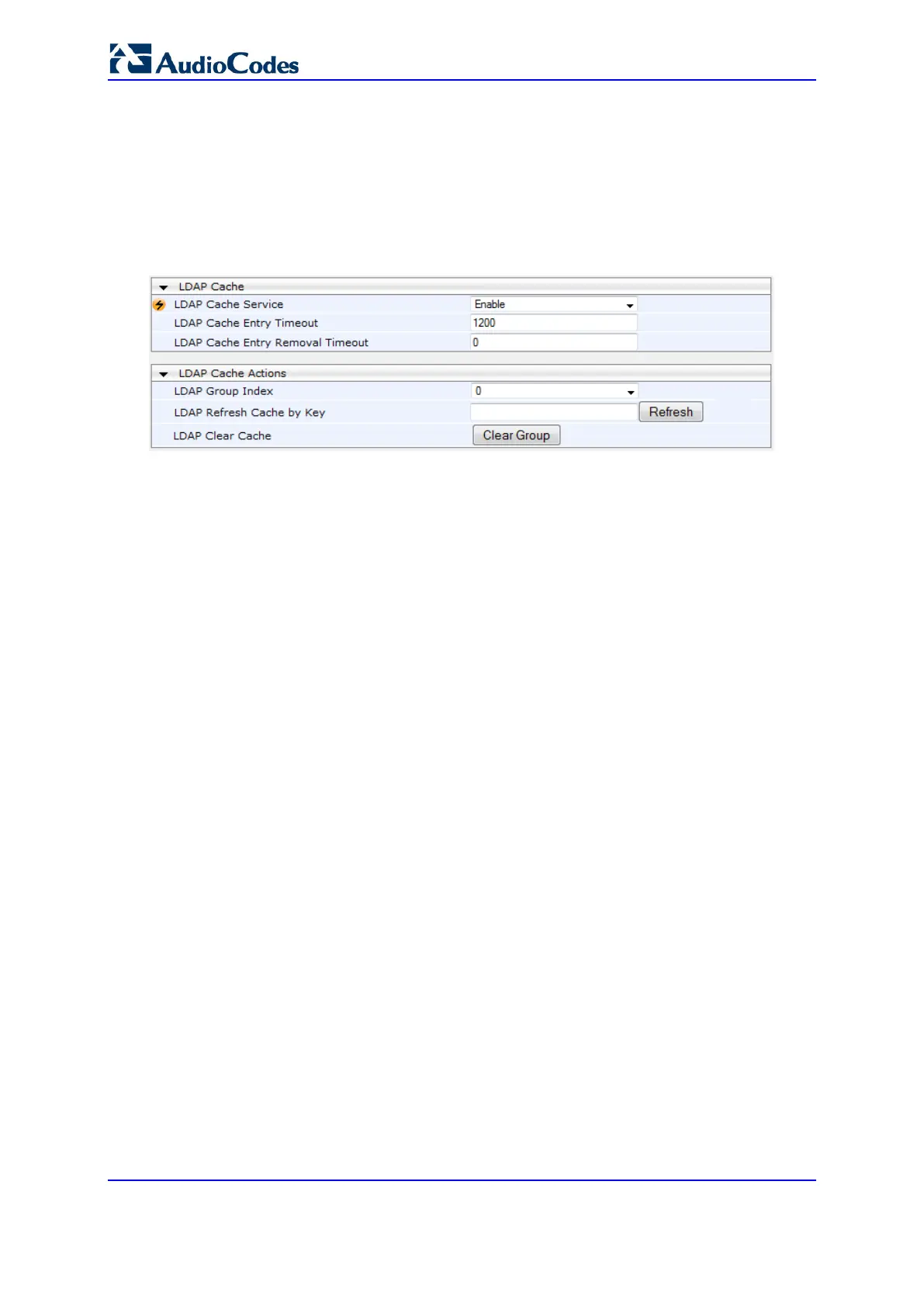
1. Open the LDAP Settings page (Configuration tab > VoIP menu > Services > LDAP
> LDAP Settings).
Figure 16-13: LDAP Settings Page - Cache Parameters
2. Under LDAP Cache, do the following:
a. From the 'LDAP Cache Service' drop-down list, select Enable to enable LDAP
cache.
b. In the 'LDAP Cache Entry Timeout' field, enter the duration (in minutes) for which
an entry in the LDAP cache is valid.
c. In the 'LDAP Cache Entry Removal Timeout' field, enter the duration (in hours)
after which the device removes the LDAP entry from the cache.
3. Click Submit, and then reset the device with a burn-to-flash for your settings to take
effect.
The LDAP Settings page also lets you refresh or clear the LDAP cache per LDAP Server
Group.
To refresh or clear the LDAP cache per LDAP Server Group:
1. From the 'LDAP Group Index' drop-down list, select the required LDAP Server Group.
2. To refresh a saved LDAP entry response in the cache of a specified LDAP search key:
a. In the 'LDAP Refresh Cache by Key' field, enter the LDAP search key that you
want to refresh.
b. Click Refresh; if a request with the specified key exists in the cache, the request
is resent to the LDAP server.
3. To remove all LDAP entries in the cache, click Clear Group.
16.3.9 Configuring Local Database for Management User
Authentication
You can configure the device to use its local database (Web Users table) to authenticate
management users based on the username-password combination. You can configure the
device to use the Web Users table upon the following scenarios:
LDAP or RADIUS server is not configured (or broken connection), or always use the
Web Users table and only if the user is not found, to use the server.
Connection with the LDAP or RADIUS server fails due to a timeout. In such a
scenario, the device can deny access or verify the user's credentials (username-
password) locally in the Web Users table.
If user authentication using the Web Users table succeeds, the device grants management
access to the user; otherwise access is denied. The access level assigned to the user is

 Loading...
Loading...











