User's Manual
270
Threshold
Drag to adjust threshold.
Once the detected percentage (the percentage of target to detection
zone) is equivalent to or larger than the specified threshold, system
triggers alarm. For example, the threshold is 10. Once the detected
target occupies the 10% of the detection zone, system triggers an alarm.
Step 7 Click Deployment Time to select schedule from the drop-down list.
After setting deployment period, system triggers corresponding operations when there is
a motion detection alarm in the specified period.
●
Click
View Schedule to view detailed schedule settings.
●
If the schedule is not added or the added schedule does not meet actual needs, click
Add Schedule. See "8.8.4 Schedule" for detailed information.
Step 8 Click Actions to set alarm actions. See "8.4.1 Alarm Actions" for detailed information.
Step 9 Click Save.
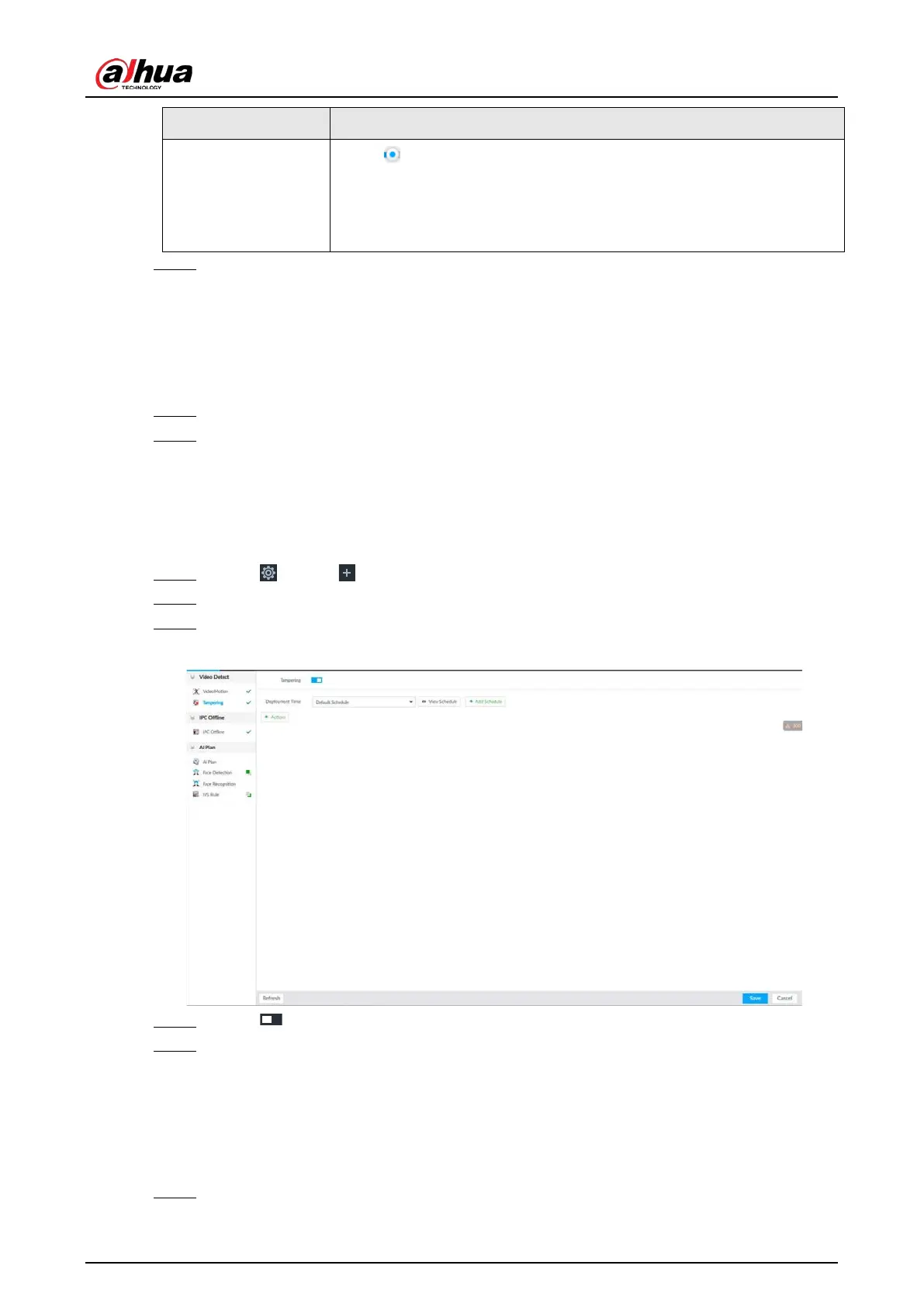
8.4.3.1.2 Tampering
Once something tampers the surveillance video, and the output video is in one color, the system can
generate an alarm.
Step 1 Click , or click on the configuration page, and then select
EVENT.
Step 2 Select remote device in the device tree on the left.
Step 3 Select Video Detect > Tampering.
Figure 8-62 Tampering
Step 4 Click to enable tampering alarm.
Step 5 Click Deployment Time to select schedule from the drop-down list.
After setting deployment period, system triggers corresponding operations when there is
a motion detection alarm in the specified period.
●
Click
View Schedule to view detailed schedule settings.
●
If the schedule is not added or the added schedule does not meet actual needs, click
Add Schedule. See "8.8.4 Schedule" for detailed information.
Step 6 Click Actions to set alarm actions. See "8.4.1 Alarm Actions" for detailed information.
 Loading...
Loading...











