C
HAPTER
4
| Configuring the Switch
Configuring Security
– 108 –
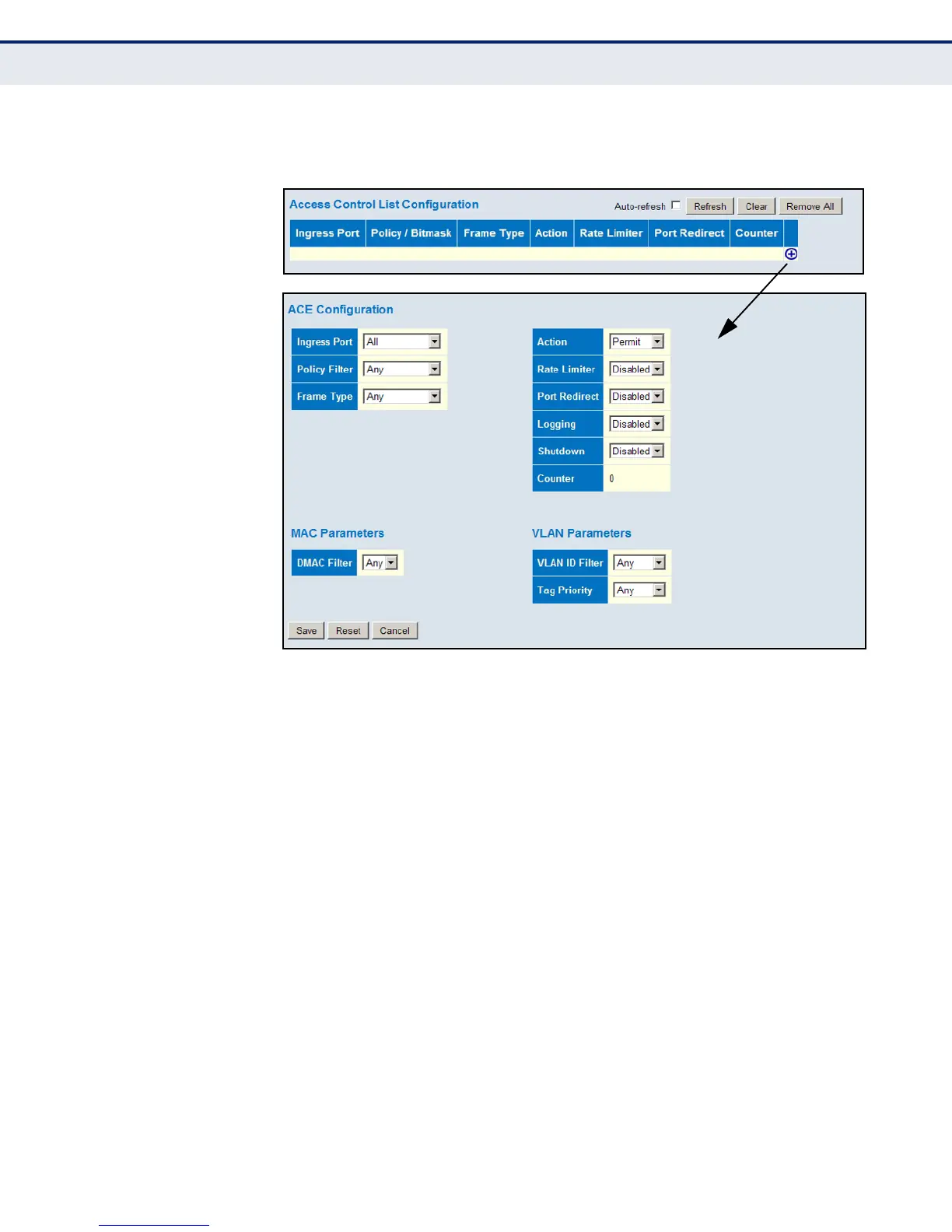
4. Click Save.
Figure 34: Access Control List Configuration
CONFIGURING DHCP
SNOOPING
Use the DHCP Snooping Configuration page to filter IP traffic on insecure
ports for which the source address cannot be identified via DHCP snooping.
The addresses assigned to DHCP clients on insecure ports can be carefully
controlled using the dynamic bindings registered with DHCP Snooping (or
using the static bindings configured with IP Source Guard). DHCP snooping
allows a switch to protect a network from rogue DHCP servers or other
devices which send port-related information to a DHCP server. This
information can be useful in tracking an IP address back to a physical port.
PATH
Advanced Configuration, Security, Network, DHCP, Snooping
COMMAND USAGE
DHCP Snooping Process
◆ Network traffic may be disrupted when malicious DHCP messages are
received from an outside source. DHCP snooping is used to filter DHCP
messages received on a non-secure interface from outside the network
or fire wall. When DHCP snooping is enabled globally and enabled on a
VLAN interface, DHCP messages received on an untrusted interface
from a device not listed in the DHCP snooping table will be dropped.

 Loading...
Loading...











