Device Configuration 5 - 289
9. Click the Next button to go to the next configuration screen. Use the Back button to go to the previous step.
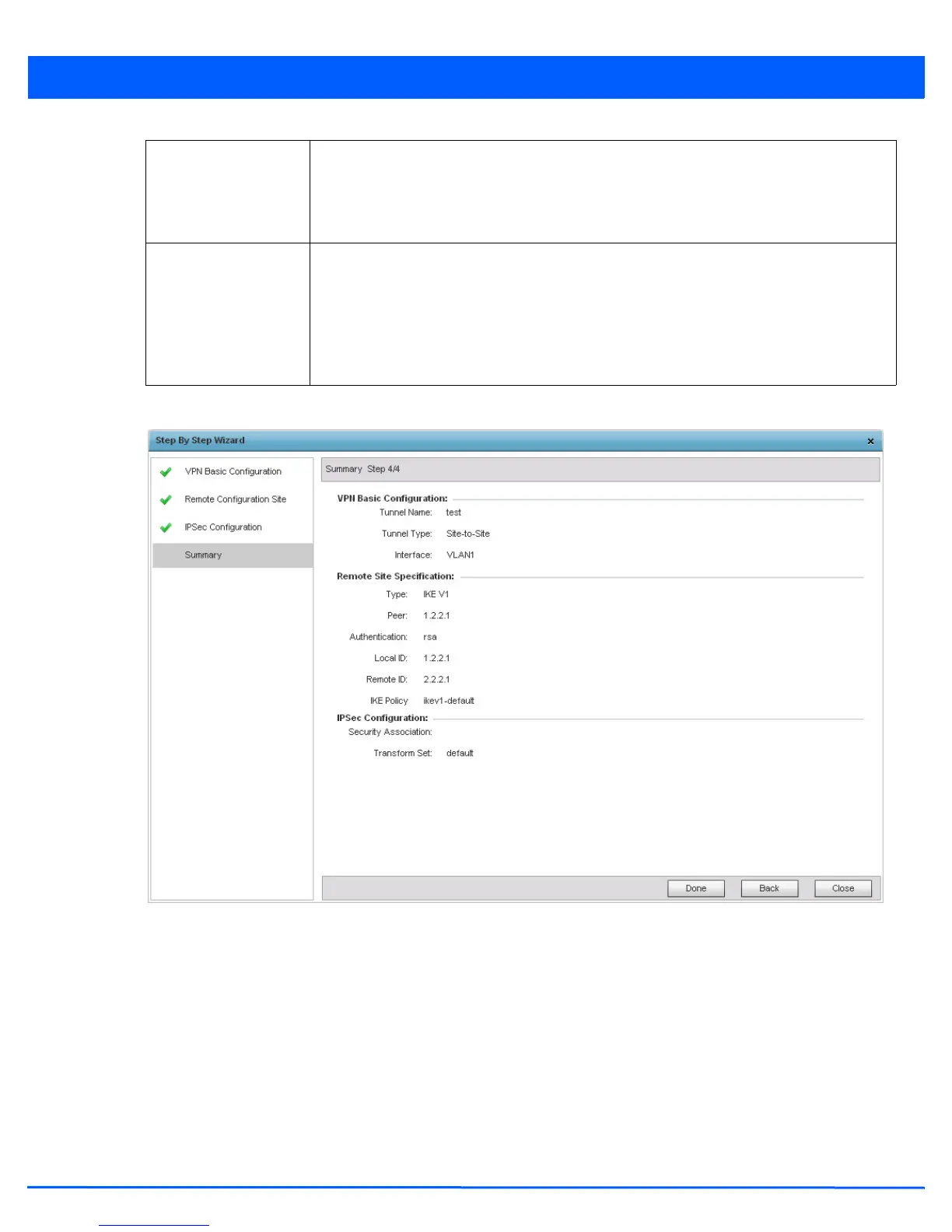
Figure 5-182 VPN Step-By-Step Wizard - Step 4
10. Review the configuration and click the Done button to create the VPN tunnel. Use the Back button to go back to previous
screen for making modifications to the configuration. Click Close to close the wizard without creating a VPN Tunnel.
5.4.5.5.4 Overriding Auto IPSec Tunnel Settings
Overriding a Security Configuration
IPSec tunnels are established to secure traffic, data and management traffic, from access points to remote wireless controllers.
Secure tunnels must be established between access points and the wireless controller with minimum configuration pushed
through DHCP option settings.
1. Select Devices from the Configuration tab.
2. Select Device Overrides from the Device menu to expand it into sub menu options.
Mode This field is enabled when Create New Policy is selected in Transform Set field. The mode
indicates how packets are transported through the tunnel.
• Tunnel – Use this mode when the tunnel is between two routers or servers.
• Transport – Use this mode when the tunnel is created between a client and a server.
Security Association Configures the lifetime of a security association (SA). Keys and SAs should be periodically
renewed to maintain security of the tunnel.
• Lifetime – Duration in seconds after which the keys should be changed. Set a value in from
500 - 2,147,413,646 seconds.
• Data – The key is changed after this quantity of data has be encrypted/decrypted. Set a
value from 500 - 2,147,413,646 KBs.

 Loading...
Loading...











