Firewall Protection
169
ProSecure Unified Threat Management (UTM) Appliance
Note these restrictions on port triggering:
• Only one PC can use a port-triggering application at any time.
• After a PC has finished using a port-triggering application, there is a short time-out period
before the application can be used by another PC. This time-out period is required so the
UTM can determine that the application has terminated.
Note: For additional ways of allowing inbound traffic, see Inbound Rules
(Port Forwarding) on page 126.
To add a port-triggering rule:
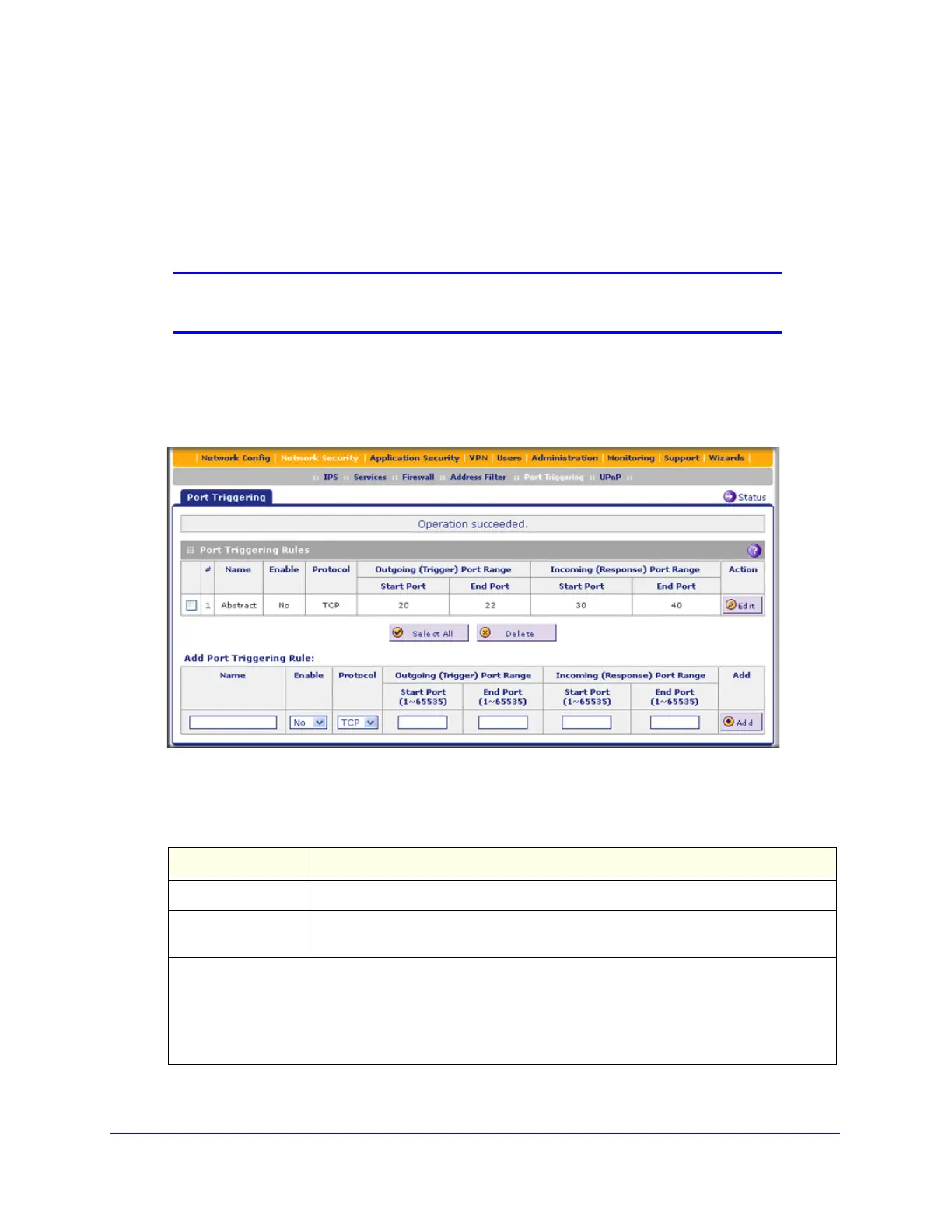
1. Select Network Security > Port Triggering. The Port Triggering screen displays. (The
following figure shows a rule in the Port Triggering Rule table as an example.)
Figure 98.
2. In the Add Port Triggering Rule section, enter the settings as explained in the following table:
Table 36. Port Triggering screen settings
Setting Description
Name A descriptive name of the rule for identification and management purposes.
Enable From the drop-down list, select Yes to enable the rule. (You can define a rule but not
enable it.) The default setting is No.
Protocol From the drop-down list, select the protocol to which the rule applies:
• TCP. The rule applies to an application that uses the Transmission Control
Protocol (TCP).
• UDP. The rule applies to an application that uses the User Datagram Protocol
(UDP).

 Loading...
Loading...















