Firewall Protection
146
ProSecure Unified Threat Management (UTM) Appliance
To delete or disable one or more VLAN rules:
1. Select the check box to the left of each VLAN rule that you want to delete or disable, or
click the Select All table button to select all VLAN rules.
2. Click one of the following table buttons:
• Disable. Disables the selected VLAN rule or rules. The ! status icon changes from a
green circle to a gray circle, indicating that the selected VLAN rule is or rules are
disabled. (By default, when a VLAN rule is added to the table, it is automatically
enabled.)
• Delete. Deletes the selected VLAN rule or rules.
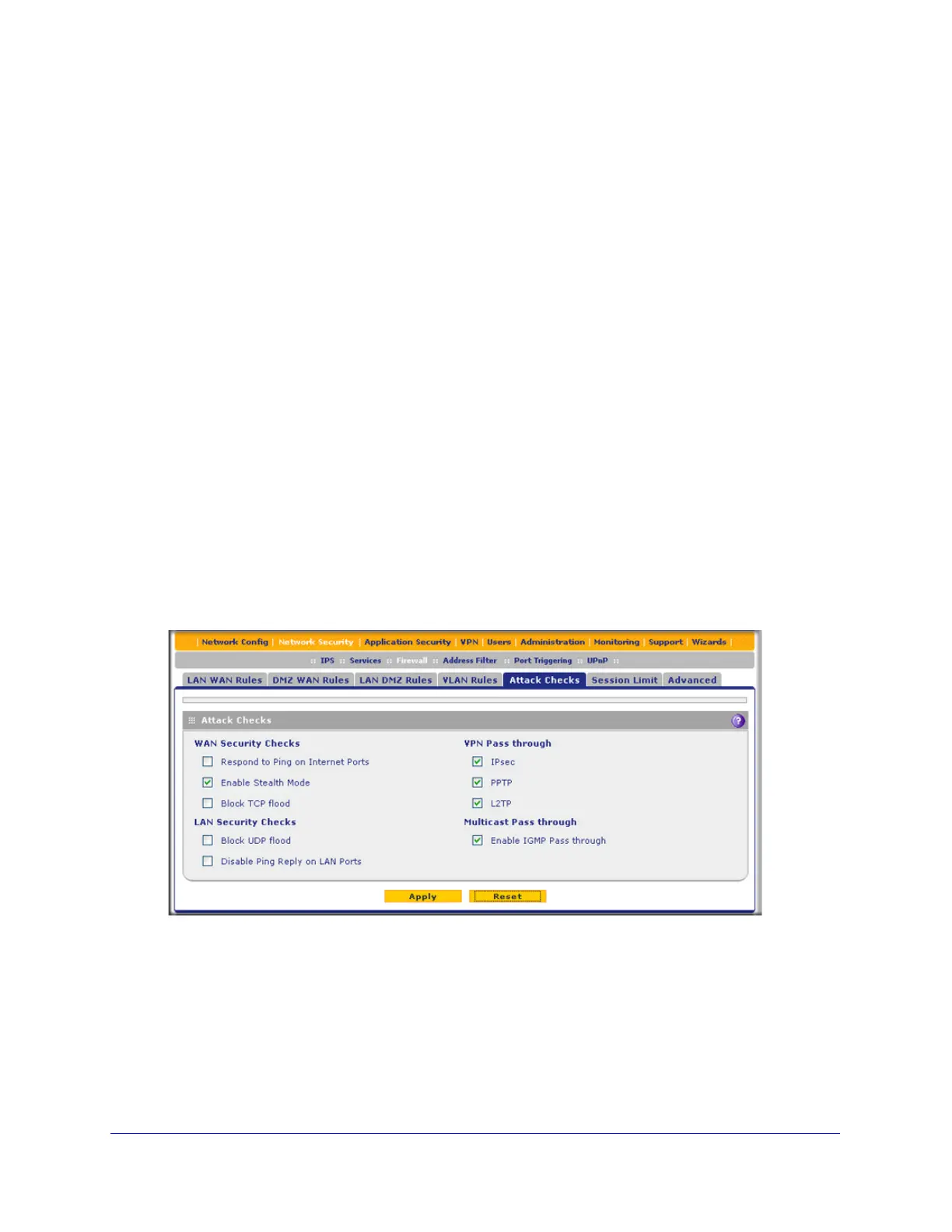
Attack Checks, VPN Pass-through, and Multicast Pass-through
The Attack Checks screen allows you to specify whether or not the UTM should be protected
against common attacks in the DMZ, LAN, and WAN networks, and lets you configure VPN
pass-through and multicast pass-through. The various types of attack checks are listed on
the Attack Checks screen and defined in Table 30 on page 147. The configuration of
multicast pass-through for the UTM9S is different from the other UTM models; see Configure
Multicast Pass-through (UTM9S Only) on page 148.
To enable the appropriate attack checks for your network environment:
1. Select Network Security > Firewall > Attack Checks. The Attack Checks screen
displays:
Figure 81.

 Loading...
Loading...















