Managing Users, Authentication, and VPN Certificates
385
ProSecure Unified Threat Management (UTM) Appliance
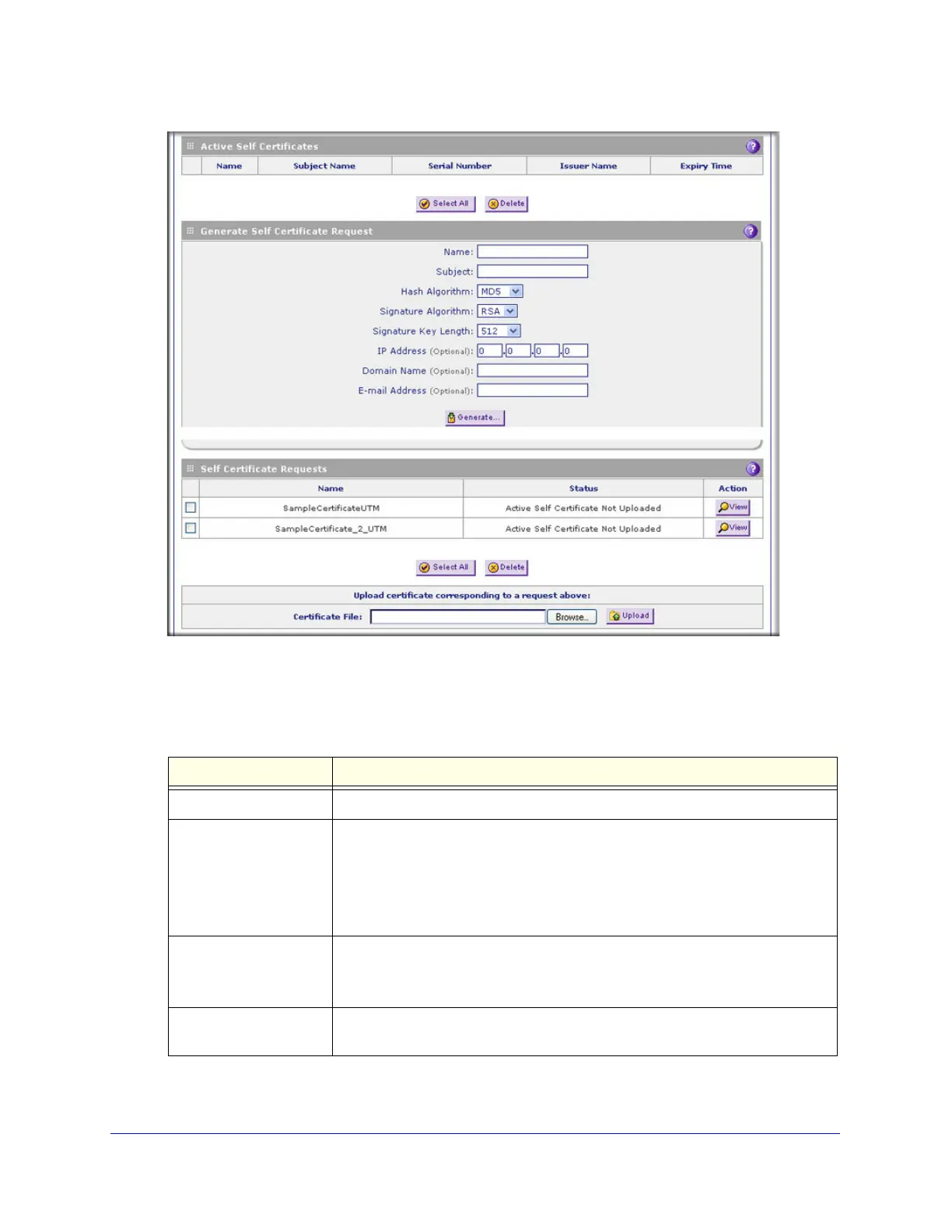
Figure 236. Certificates, screen 2 of 3
2. In the Generate Self Certificate Request section of the screen, enter the settings as
explained in the following table:
Table 98. Generate self-signed certificate request settings
Setting Description
Name A descriptive name of the domain for identification and management purposes.
Subject The name that other organizations see as the holder (owner) of the certificate. In
general, use your registered business name or official company name for this
purpose.
Note: Generally, all of your certificates should have the same value in the
Subject field.
Hash Algorithm From the drop-down list, select one of the following hash algorithms:
• MD5. A 128-bit (16-byte) message digest, slightly faster than SHA-1.
• SHA-1. A 160-bit (20-byte) message digest, slightly stronger than MD5.
Signature Algorithm Although this seems to be a drop-down list, the only possible selection is RSA. In
other words, RSA is the default to generate a CSR.

 Loading...
Loading...















