Monitoring System Access and Performance
462
ProSecure Unified Threat Management (UTM) Appliance
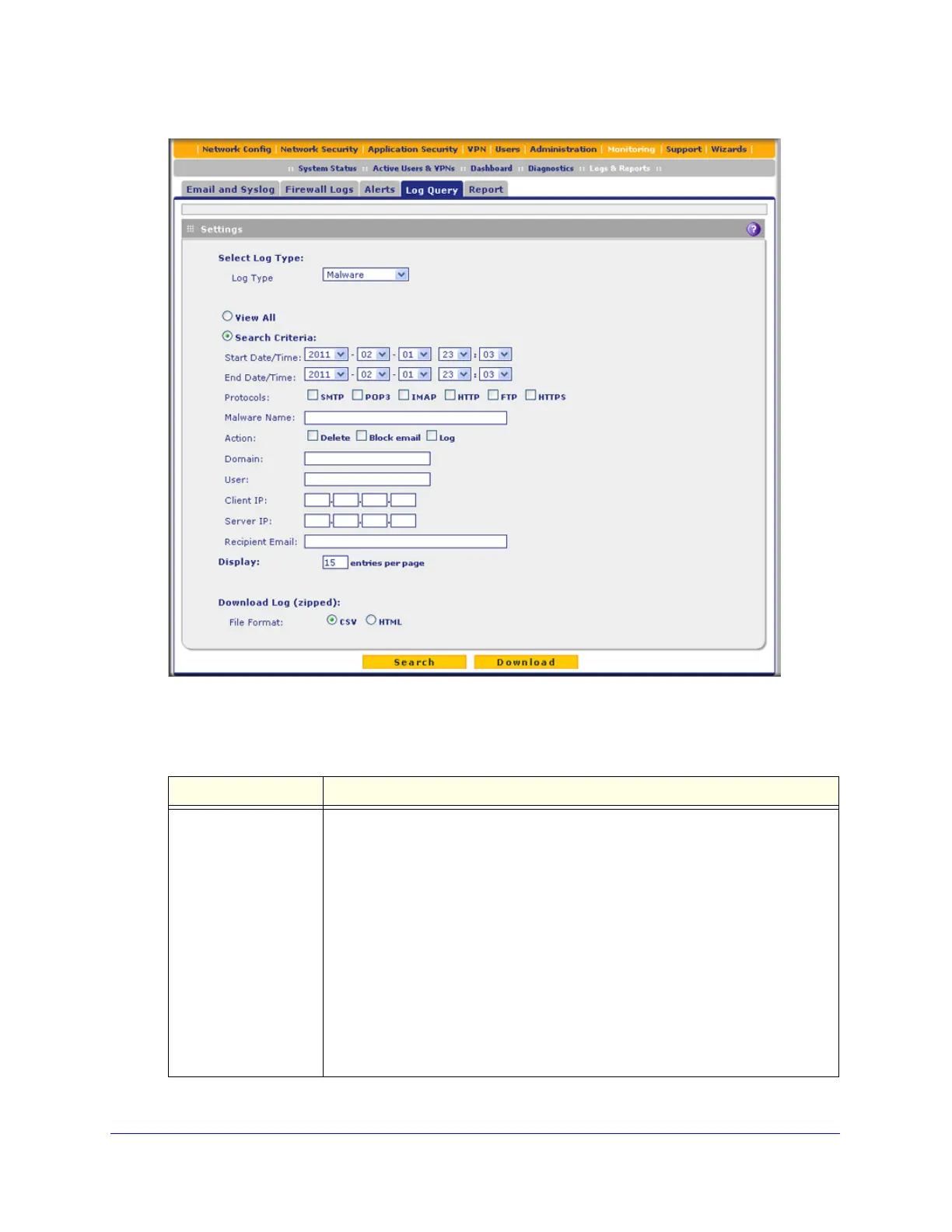
Figure 278.
2. Enter the settings as explained in the following table:
Table 123. Logs Query screen settings
Setting Description
Log Type Select one of the following log types from the drop-down list:
• Traffic. All scanned incoming and outgoing traffic.
• Spam. All intercepted spam.
• System. The system event logs that you have specified on the Email and
Syslog screen (see Configure and Activate System, Email, and Syslog Logs on
page 423). However, by default, many more types of events are logged in the
system logs. Note that you cannot specify further search criteria on the Log
Query screen, that is, when you select System from the drop-down list, the
System Logs screen displays.
• Service Logs. All events that are related to the status of scanning and filtering
services that you access from the Application Security main navigation menu.
These events include update success messages, update failed messages,
network connection errors, and so on.
• Malware. All intercepted viruses, spyware, and other malware threats.

 Loading...
Loading...















