User Manual
Advanced Console Server & RIM Gateway User Manual 201
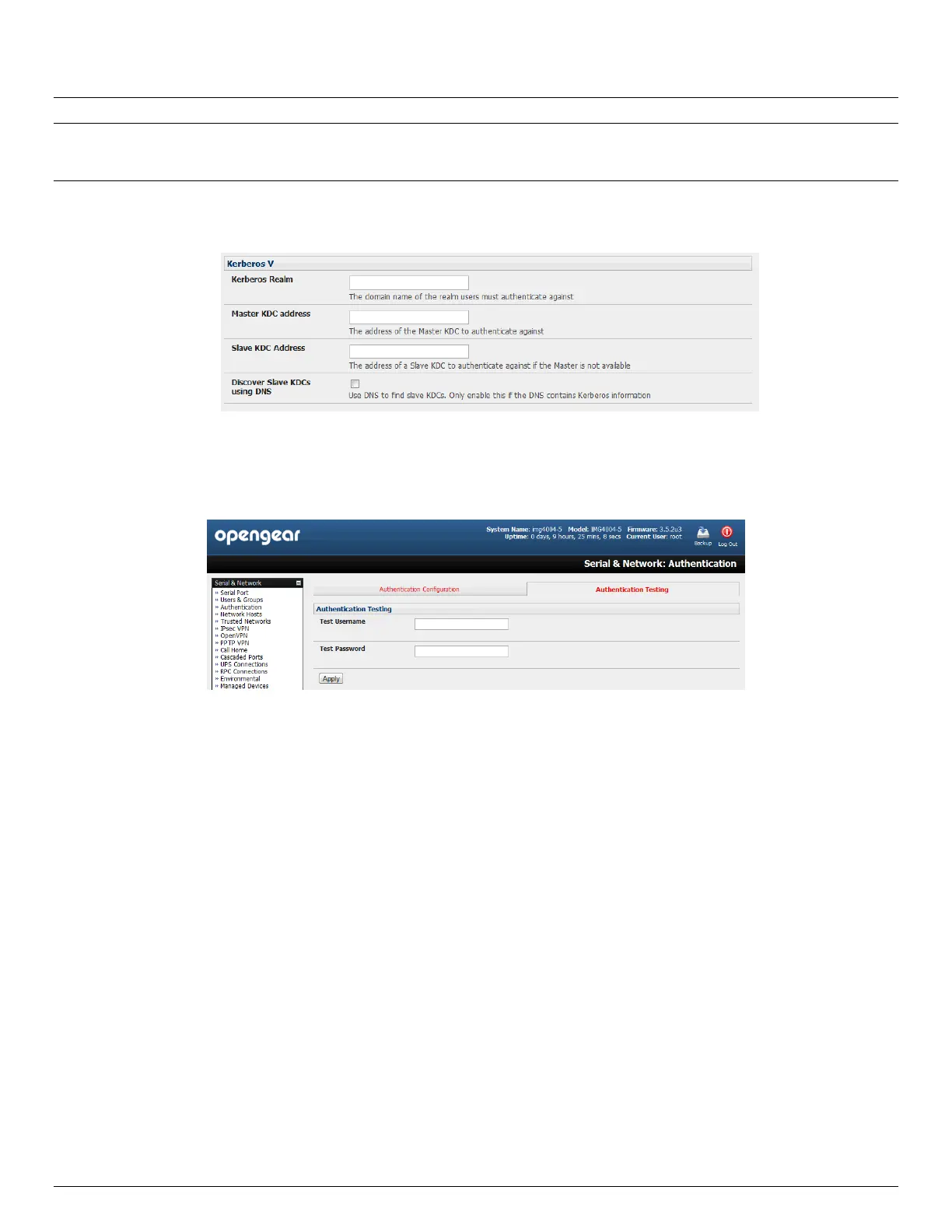
Note: Kerberos is very sensitive to time differences between the Key Distribution Center (KDC) authentication server
and the client device. Please make sure that NTP is enabled, and the time zone is set correctly on the console
server.
When authenticating against Active Directory, the Kerberos Realm will be the domain name, and the Master KDC will be
the address of the primary domain controller.
9.1.11 Authentication testing
The Authentication Testing tab (firmware V3.5.2u3 and later) enables the connection to the remote authentication server
to be tested.
9.2 PAM (Pluggable Authentication Modules)
The console server supports RADIUS, TACACS+ and LDAP for two-factor authentication via PAM (Pluggable
Authentication Modules). PAM is a flexible mechanism for authenticating users. Nowadays a number of new ways of
authenticating users have become popular. The challenge is that each time a new authentication scheme is developed; it
requires all the necessary programs (login, ftpd etc.) to be rewritten to support it.
PAM provides a way to develop programs that are independent of authentication scheme. These programs need
"authentication modules" to be attached to them at run-time in order to work. Which authentication module is to be
attached is dependent upon the local system setup and is at the discretion of the local Administrator.
The console server family supports PAM to which we have added the following modules for remote authentication:
RADIUS - pam_radius_auth (http://www.freeradius.org/pam_radius_auth/)
TACACS+ - pam_tacplus (http://echelon.pl/pubs/pam_tacplus.html)
LDAP - pam_ldap (http://www.padl.com/OSS/pam_ldap.html)
Further modules can be added as required.
Changes may be made to files in /etc/config/pam.d/ which will persist, even if the authentication configurator is run.
Users added on demand:

 Loading...
Loading...