Configuration Guide Configuring AAA
2.2.1 Configuring AAA in a Single-Domain Environment
Scenario
In the network scenario shown in Figure 2-1, the following application requirements must be satisfied to improve the security
management on the NAS:
3. To facilitate account management and avoid information disclosure, each administrator has an individual account with
different username and password.
4. Users must pass identity authentication before accessing the NAS. The authentication can be in local or centralized
mode. It is recommended to combine the two modes, with centralized mode as active and local mode as standby. As a
result, users must undergo authentication by the RADIUS server first. If the RADIUS server does not respond, it turns to
local authentication.
5. During the authentication process, users can be classified and limited to access different NASs.
6. Permission management: Users managed are classified into Super User and Common User. Super users have the
rights to view and configure the NAS, and common users are only able to view NAS configuration.
7. The AAA records of users are stored on servers and can be viewed and referenced for auditing. (The TACACS+ server
in this example performs the accounting.)
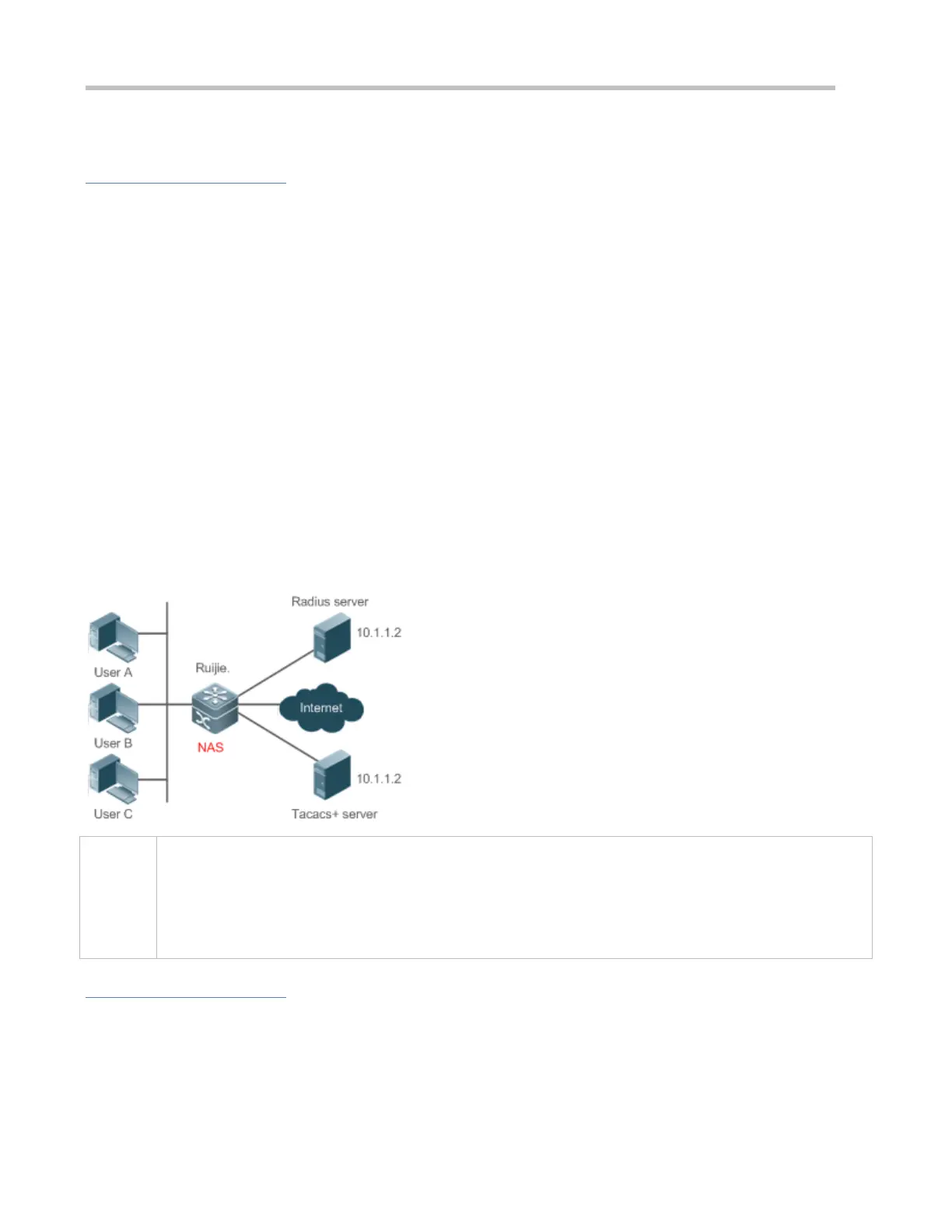
Figure 2-1
User A, User B, and User C are connected to the NAS in wired or wireless way.
The NAS is an access or convergence switch.
The RADIUS server can be the Windows 2000/2003 Server (IAS), UNIX system component, and dedicated
server software provided by a vendor.
The TACACS+ server can be the dedicated server software provided by a vendor.
Deployment
Enable AAA on the NAS.
Configure an security server on the NAS.
Configure local users on the NAS.

 Loading...
Loading...











