Configuration Guide Configuring DHCP Snooping
Limit the rates of DHCP packets from the untrusted ports.
Enable DHCP Snooping correlation with ARP, and detect whether the user is online.
8.2.3 Guarding Against Forged DHCP Packets
Scenario
Potential malicious clients in a network may forge DHCP request packets, consuming applicable IP addresses from the
servers and probably preempting legal users' IP addresses. Therefore, it is necessary to filter out illegal DHCP packets.
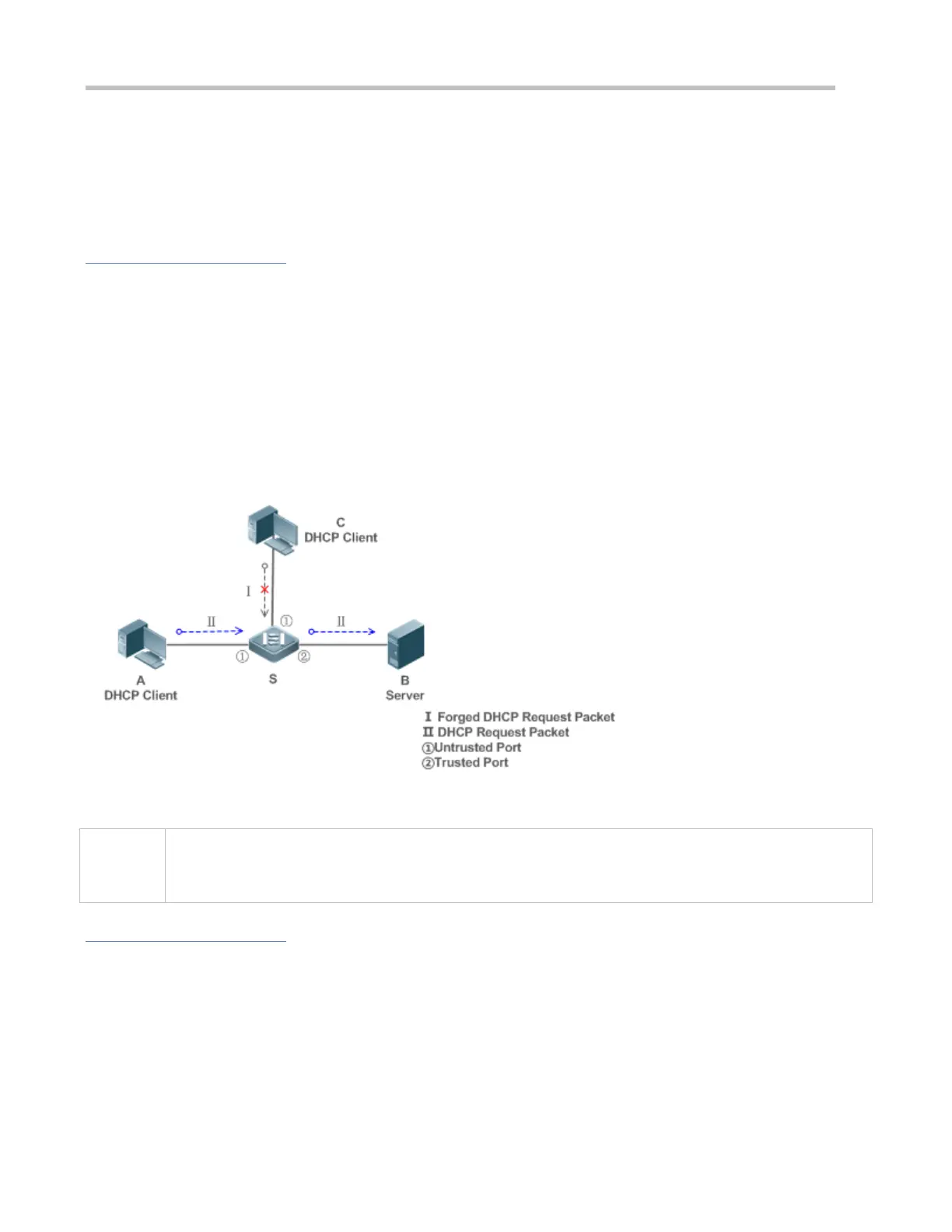
For example, as shown in the figure below, the DHCP request packets sent from DHCP clients will be checked.
The source MAC address fields of the request packets from DHCP clients must match the chaddr fields of DHCP
packets.
The Release packets and Decline packets from clients must match the entries in the DHCP Snooping binding database.
Figure 8-2
S is an access device.
A and C are user PCs.
B is a DHCP server within the controlled area.
Deployment
Enable DHCP Snooping on S to realize DHCP monitoring.
Set the port on S connecting to B as trusted to transfer response packets.
Set the rest of ports on S as untrusted to filter response packets.
Enable DHCP Snooping Source MAC Verification on untrusted ports of S to filter out illegal packets.

 Loading...
Loading...











