Configuration Guide Configuring 802.1X
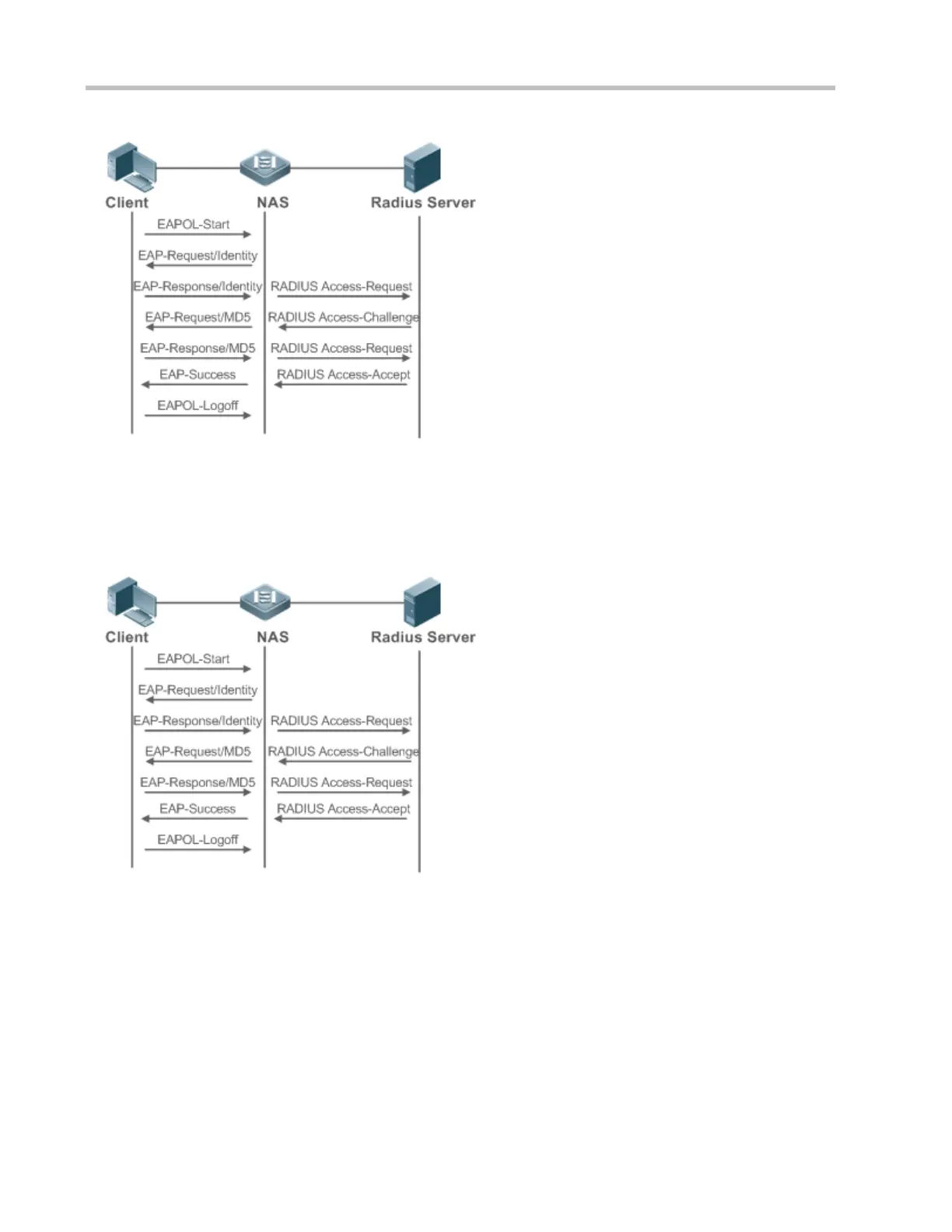
This is a typical authentication process initiated by a user. In special cases, the NAS, may take place of the user to initiate an
authentication request.
Figure 4-4 shows the typical authentication process of an STA.
Authenticating User Status
802.1X determines whether a user on a port can access the network based on the authentication status of the port. Ruijie
products extend the 802.1X and realizes access control based on users (identify a wired user by the MAC address) by
default.
All users on an uncontrolled port can access network resources, while users on a controlled port can access network
resources only after authorized. When a user initiates authentication, its status remains unauthorized and cannot access the
network yet. After it passes authentication, its status changes to authorized and can access network resources.

 Loading...
Loading...











