Device Configuration 5 - 111
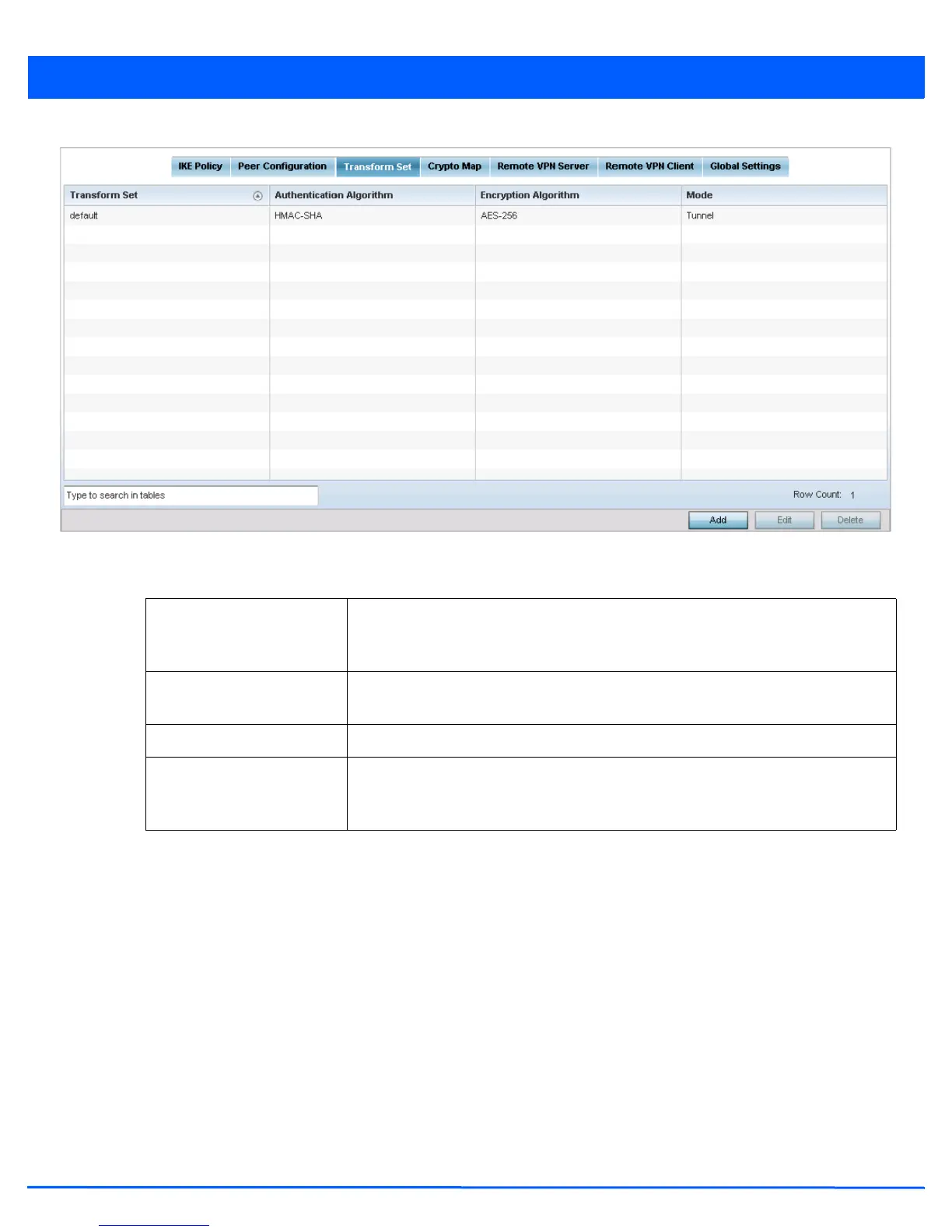
Figure 5-64 Profile Security - VPN Transform Set tab
16. Review the following attributes of an existing Transform Set configurations:
17. Select Add to define a new transform set configuration, Edit to modify an existing configuration or Delete to remove an
existing transform set.
Transform Set Lists the 32 character maximum name assigned to each listed transform set upon
creation. Again, a transform set is a combination of security protocols, algorithms and
other settings applied to IPSec protected traffic.
Authentication Algorithm Lists each transform sets’s authentication scheme used to validate identity credentials.
The authentication scheme is either HMAC-SHA or HMAC-MD5.
Encryption Algorithm Displays each transform set’s encryption method for protecting transmitted traffic.
Mode Displays either Tunnel or Transport as the IPSec tunnel type used with the transform set.
Tunnel is used for site-to-site VPN and Transport should be used for remote VPN
deployments.

 Loading...
Loading...











