C
HAPTER
14
| Basic Administration Protocols
Ethernet Ring Protection Switching
– 502 –
ring link in the sub-ring will cause the R-APS channel of the sub-ring
to be segmented, thus preventing R-APS message exchange
between some of the sub-ring’s ring nodes.
No R-APS messages are inserted or extracted by other rings or sub-
rings at the interconnection nodes where a sub-ring is attached.
Hence there is no need for either additional bandwidth or for
different VIDs/Ring IDs for the ring interconnection. Furthermore,
protection switching time for a sub-ring is independent from the
configuration or topology of the interconnected rings. In addition,
this option always ensures that an interconnected network forms a
tree topology regardless of its interconnection configuration. This
means that it is not necessary to take precautions against forming a
loop which is potentially composed of a whole interconnected
network.
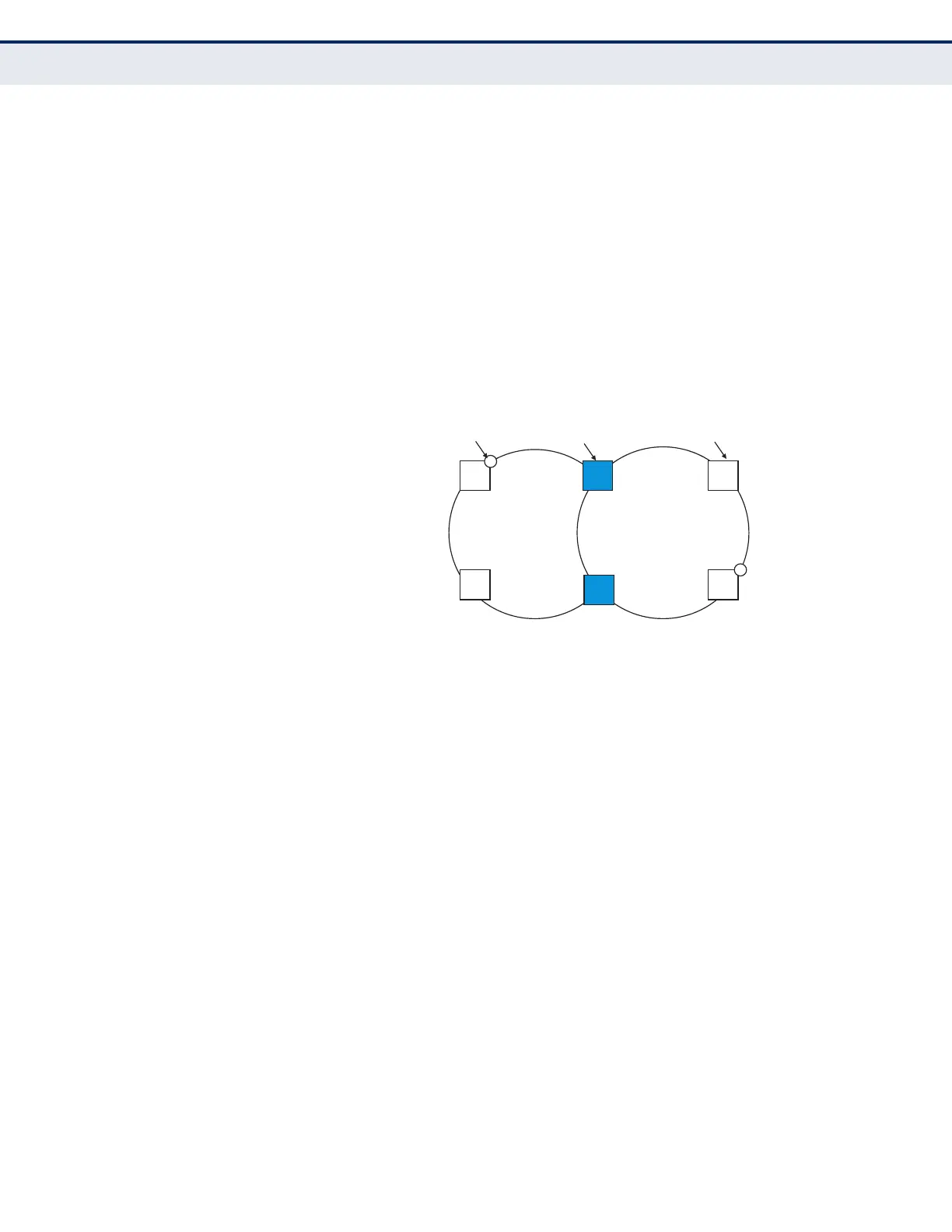
Figure 286: Sub-ring without Virtual Channel
◆ R-APS Def MAC – Sets the switch’s MAC address to be used as the
node identifier in R-APS messages. (Default: Enabled)
When ring nodes running ERPSv1 and ERPSv2 co-exist on the same
ring, the Ring ID of each ring node must be configured as “1”.
If this command is disabled, the following strings are used as the node
identifier:
■
ERPSv1: 01-19-A7-00-00-01
■
ERPSv2: 01-19-A7-00-00-[Ring ID]
◆ Propagate TC – Enables propagation of topology change messages
from a secondary ring to the primary ring. (Default: Disabled)
When a secondary ring detects a topology change, it can pass a
message about this event to the major ring. When the major ring
receives this kind of message from a secondary ring, it can clear the
MAC addresses on its ring ports to help the second ay ring restore its
connections more quickly through protection switching.
When the MAC addresses are cleared, data traffic may flood onto the
major ring. The data traffic will become stable after the MAC addresses
are learned again. The major ring will not be broken, but the bandwidth
of data traffic on the major ring may suffer for a short period of time
due to this flooding behavior.
Sub-ring
with Virtual
Channel
RPL Port
Interconnection Node
Ring Node
Major Ring

 Loading...
Loading...