How list order affects policy matching Firewall Policy
FortiGate Version 4.0 MR1 Administration Guide
388 01-410-89802-20090903
http://docs.fortinet.com/ • Feedback
• source and destination firewall addresses
• services
• time/schedule.
If no policy matches, the connection is dropped.
As a general rule, you should order the firewall policy list from most specific to most
general because of the order in which policies are evaluated for a match, and because
only the first matching firewall policy is applied to a connection. Subsequent possible
matches are not considered or applied. Ordering policies from most specific to most
general prevents policies that match a wide range of traffic from superseding and
effectively masking policies that match exceptions.
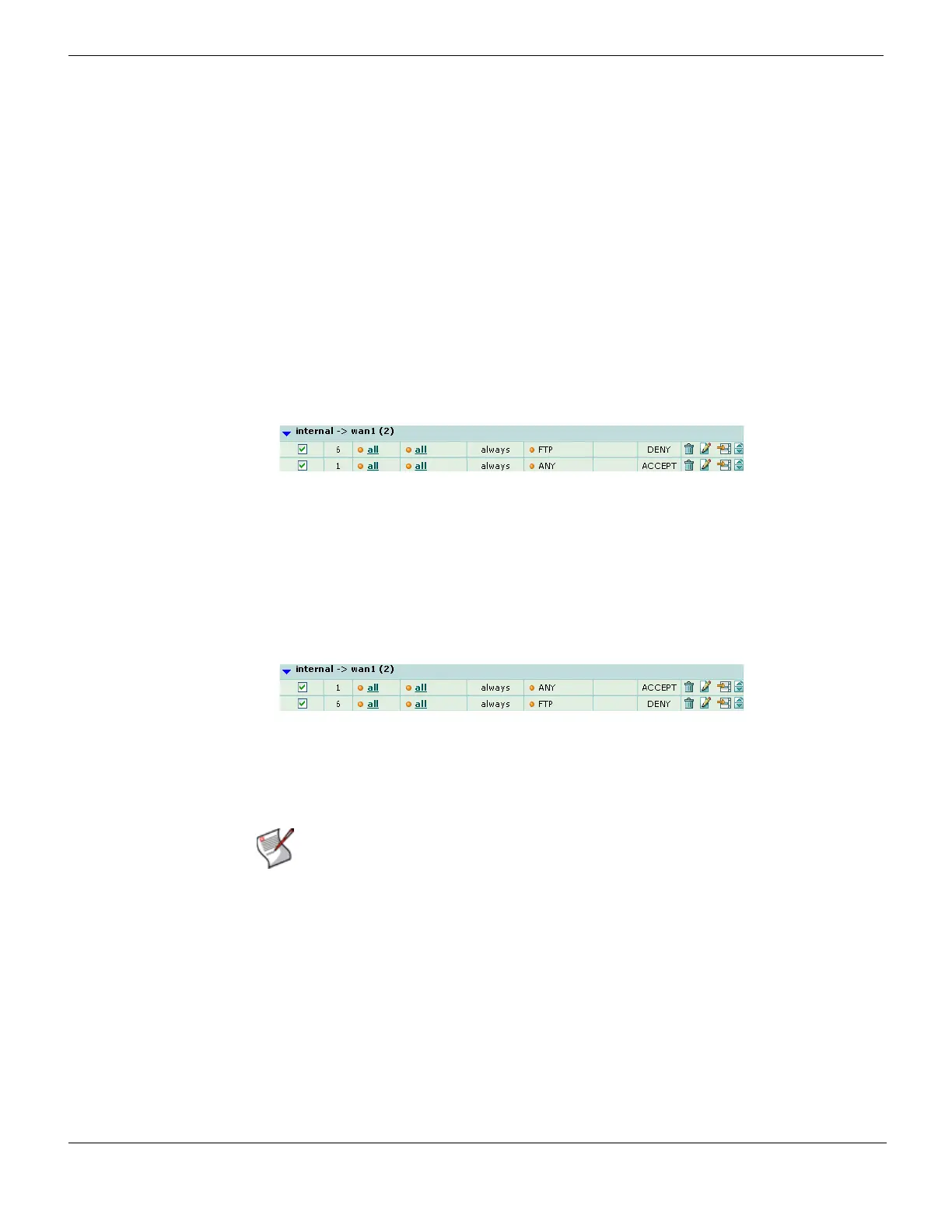
For example, you might have a general policy that allows all connections from the internal
network to the Internet, but want to make an exception that blocks FTP. In this case, you
would add a policy that denies FTP connections above the general policy.
Figure 205: Example: Blocking FTP — Correct policy order
FTP connections would immediately match the deny policy, blocking the connection.
Other kinds of services do not match the FTP policy, and so policy evaluation would
continue until reaching the matching general policy. This policy order has the intended
effect. But if you reversed the order of the two policies, positioning the general policy
before the policy to block FTP, all connections, including FTP, would immediately match
the general policy, and the policy to block FTP would never be applied. This policy order
would not have the intended effect.
Figure 206: Example: Blocking FTP — Incorrect policy order
Similarly, if specific traffic requires authentication, IPSec VPN, or SSL VPN, you would
position those policies above other potential matches in the policy list. Otherwise, the
other matching policies could always take precedence, and the required authentication,
IPSec VPN, or SSL VPN might never occur.
Moving a policy to a different position in the policy list
You can arrange the firewall policy list to influence the order in which policies are
evaluated for matches with incoming traffic. When more than one policy has been defined
for the same interface pair, the first matching firewall policy will be applied to the traffic
session. For more information, see “How list order affects policy matching” on page 387.
Moving a policy in the firewall policy list does not change its ID, which only indicates the
order in which the policy was created.
Note: A default firewall policy may exist which accepts all connections. You can move,
disable or delete it. If you move the default policy to the bottom of the firewall policy list and
no other policy matches the packet, the connection will be accepted. If you disable or delete
the default policy and no other policy matches the packet, the connection will be dropped.

 Loading...
Loading...











