What’s new in FortiOS Version 4.0 MR1 Two-factor authentication
FortiGate Version 4.0 MR1 Administration Guide
01-410-89802-20090903 43
http://docs.fortinet.com/ • Feedback
config apps
edit <appname_str>
set md5s <md5_str>
end
end
Two-factor authentication
In FortiOS 4.0 MR1, PKI users can be required to authenticate by password in addition to
their certificate authentication, for both administrative and SSL VPN access. This provides
additional security to meet ICSA 4.0 requirements.
To enable two-factor authentication for a PKI user - web-based manager
1 Go to User > PKI.
2 Select the Edit icon for the user.
3 Expand Two-factor authentication.
4 Select Require two-factor authentication and enter the Password for this user.
5 Select OK.
6 Repeat steps 2 through 5 for each user who must use two-factor authentication.
To enable two-factor authentication for a PKI user - CLI
config user peer
edit <peer1_name>
set two-factor enable
set password <password_str>
next
edit <peer2_name>
...
end
To require two-factor authentication in an SSL VPN
conf vpn ssl settings
set force-two-factor-auth enable
end
If this option is enabled, only users with two-factor authentication can log in to the SSL
VPN.
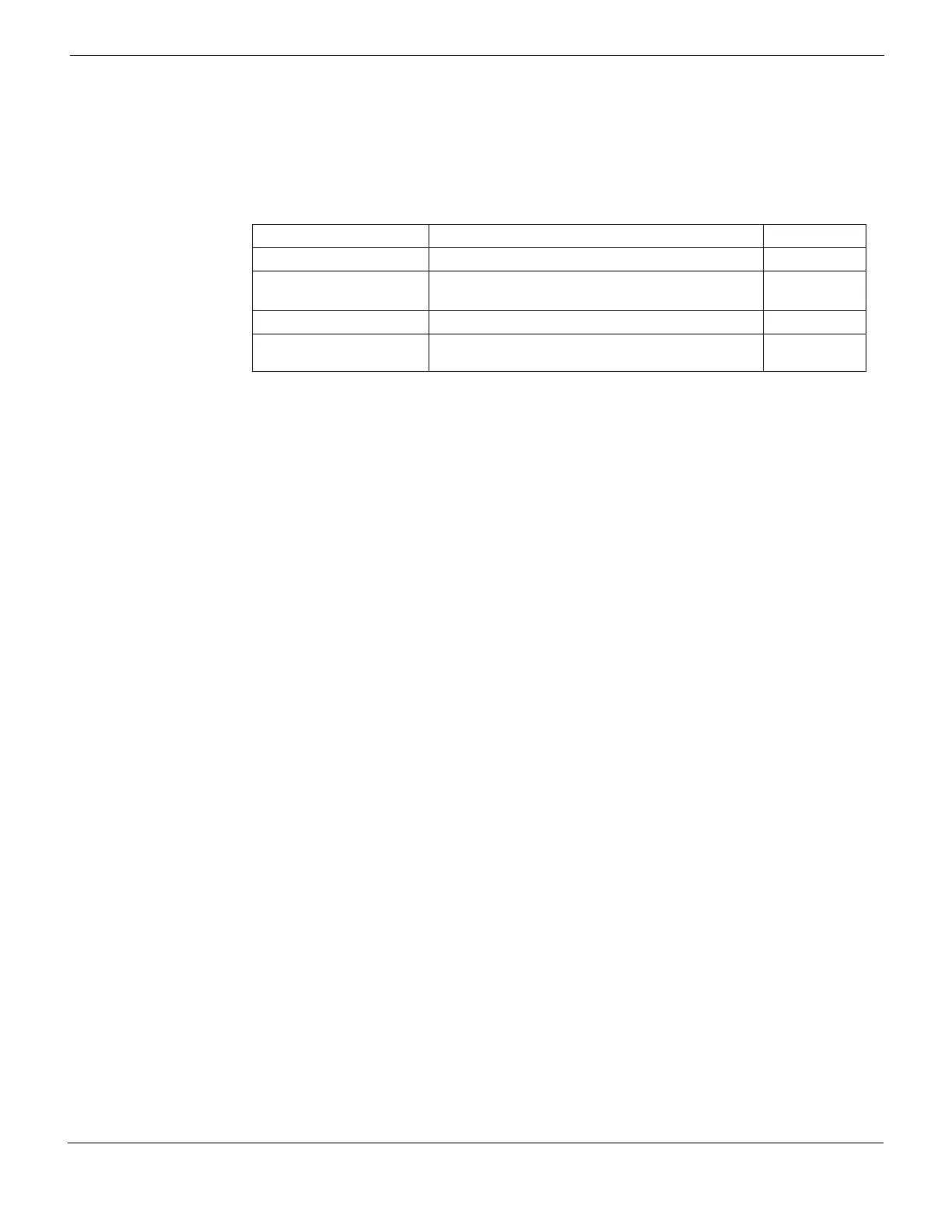
Variable Description Default
<applist_name> Enter a name for the application control list. No default.
action
{allow | block}
allow — Allow only the applications on this list
block — Block these applications, allow all others
allow
<appname_str> Enter a name for the application. No default.
md5s <md5_str> Enter one or more MD5 checksums, separated by
spaces.
No default.
 Loading...
Loading...











