Protocol decoders Intrusion Protection
FortiGate Version 4.0 MR1 Administration Guide
536 01-410-89802-20090903
http://docs.fortinet.com/ • Feedback
To create a custom signature, go to UTM > Intrusion Protection > Custom.
Figure 316: Edit Custom Signature
Protocol decoders
The FortiGate Intrusion Protection system uses protocol decoders to identify the abnormal
traffic patterns that do not meet the protocol requirements and standards. For example,
the HTTP decoder monitors traffic to identify any HTTP packets that do not meet the
HTTP protocol standards.
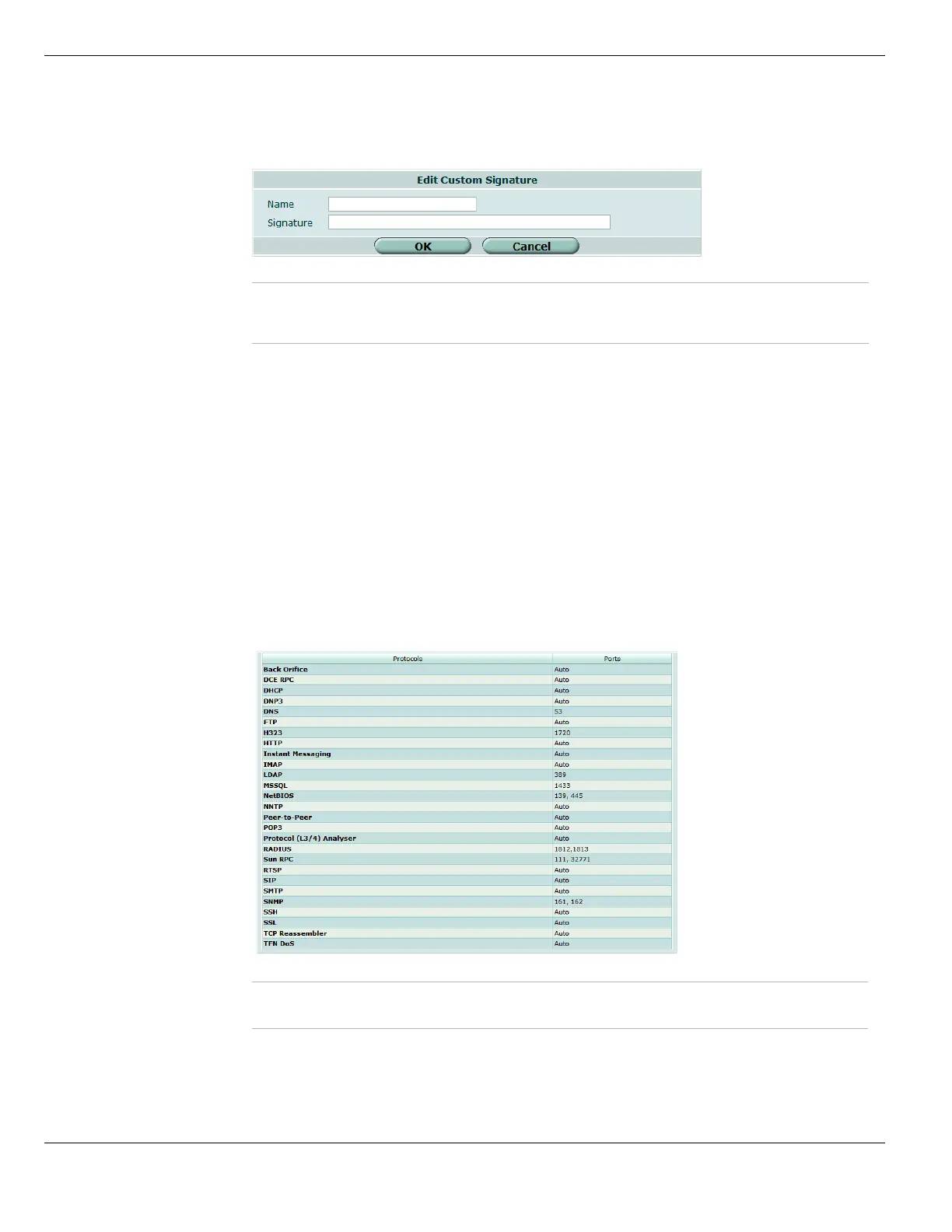
Viewing the protocol decoder list
To view the decoders and the port numbers that the protocol decoders monitor, go to
UTM > Intrusion Protection > Protocol Decoder. The decoder list is provided for your
reference and can be configured using the CLI. For more information, see the FortiGate
CLI Reference.
Figure 317: The protocol decoder list
Name Enter a name for the custom signature.
Signature Enter the custom signature, using the appropriate syntax. For more information,
see the FortiGate UTM User Guide.
Protocols The protocol decoder name.
Ports The port number or numbers that the decoder monitors.

 Loading...
Loading...











