Configuration Guide AAA Configuration
Although the AAA is the primary access control method, our product also provides simple
control accesses out of the range of AAA, such as the local username authentication, line
password authentication and more. The difference lies in the degree of their network
protection, and the AAA provides the security protection of a higher level.
The AAA has the following advantages:
Powerful flexibility and controllability
Expandability
Standardized authentication
Multiple backup systems
Basic AAA Principles
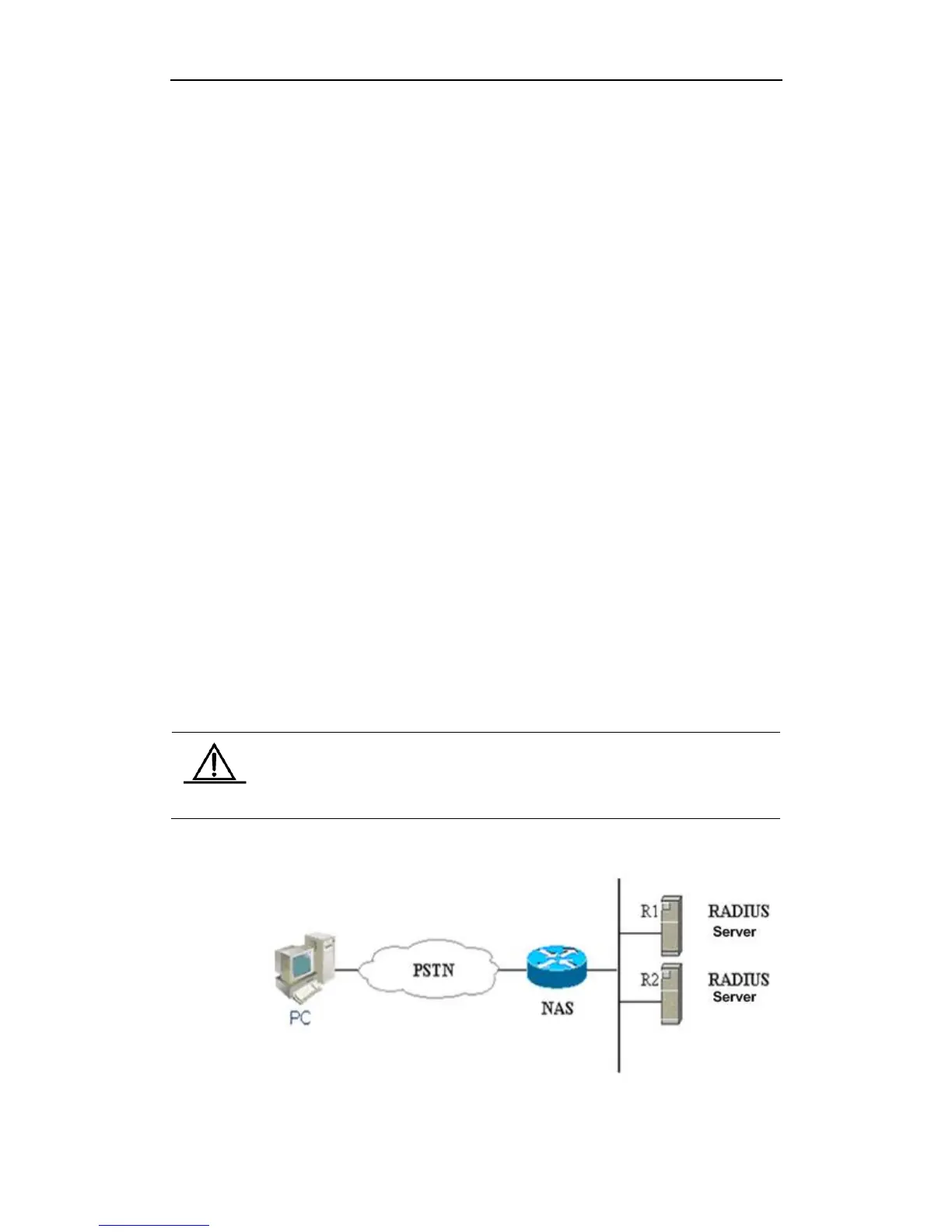
The AAA can configure dynamically authentication, authorization and accounting for a single
user (line) or server. It defines the authentication, authorization and accounting by means of
creating method lists and then applies them on specific services or interfaces.
Method List
Since the authentication for users can be implemented in a variety of ways, you need to use
the method list to define the sequence of using different method to perform authentication for
the users. The method list can define one or more security protocols for authentication, so that
there are backup systems available for the authentication in case of the failure of the first
method. Our product works with the first method in the method list for user authentication, and
then selects the next method in the method list in case of no reply from that method. This
process goes on till an authentication method listed successfully allows communication or all
methods listed are used up. If all methods listed are used up but the communication is not
allowed, it declares failure of authentication.
Only when there is no reply from a method, our product will attempt the next
method. During the authentication, if the user access is refused by a method,
the authentication process ends and no other methods will be attempted.

 Loading...
Loading...









