Configuration Guide Dynamic ARP Inspection Configuration
Dynamic ARP Inspection
Configuration
Overview
DAI, an acronym of Dynamic ARP Inspection, refers to inspect the validity of
received ARP packets. Illegal ARP packets will be discarded.
ARP Spoofing Attack
ARP itself does not check the validity of incoming ARP packets, a drawback of
ARP. In this way, attackers can launch ARP spoofing attacks easily by exploiting
the drawback of the protocol. The most typical one is the man in the middle
attack, which is described as follows:
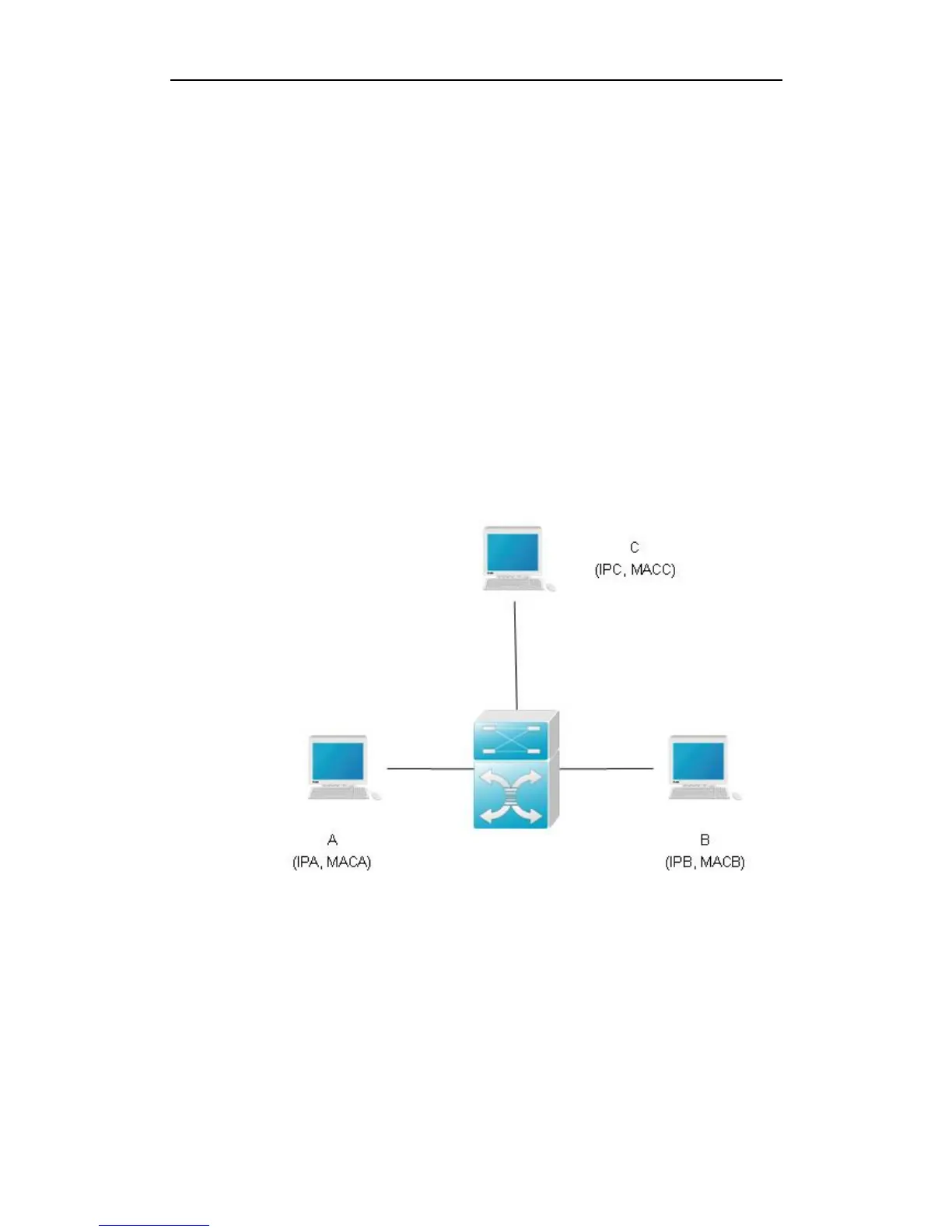
As shown in the diagram, devices A, B and C are connected to Ruijie device
and located in the same subnet. Their IP and MAC addresses are respectively
represented by (IPA, MACA), (IPB, MACB) and (IPC, MACC). When device A
needs to communicate with device B in the network layer, device A broadcasts
an ARP request in the subnet to query the MAC value of device B. Upon
receiving this ARP request packet, device B updates its ARP buffer using IPA
and MACA, and sends an ARP response. Upon receiving this response, device
A updates its ARP buffer using IPB and MACB.

 Loading...
Loading...









