10.3 Step by Step Setup Instructions
In Figure 10-1, three servers are located in the local network. Their IP addresses are as follows:
HTTP Server: 192.168.100.11
FTP Server: 192.168.100.22
TELNET Server: 192.168.100.33
Note: This is a sample setup only. Your setup will have IP addresses relevant to your own situation.
Traffic rules on the WAN Interfaces of the Loop-IP6610 are as follows:
1. The HTTP server is accessible by all PCs (also known as hosts) in the network.
2. TELNET Server access (IP: 192.168.100.33) is available only to the client’s designated Remote User
(IP: 140.100.5.5 ). No other devices, including those at the client’s head office or branch office, can
reach that server.
3. IP: 100.3.0.0 is the network for another branch of the client’s company, so all traffic from that site is
permitted.
4. Because FTP Server Access is provided only for the client (IP: 140.1.x.x, where x is 0-255.) and the
client’s branch office, the IP6610 shall permit ftp packets from those sites.
By keying in the appropriate commands and IP addresses the rules can be set as follows:
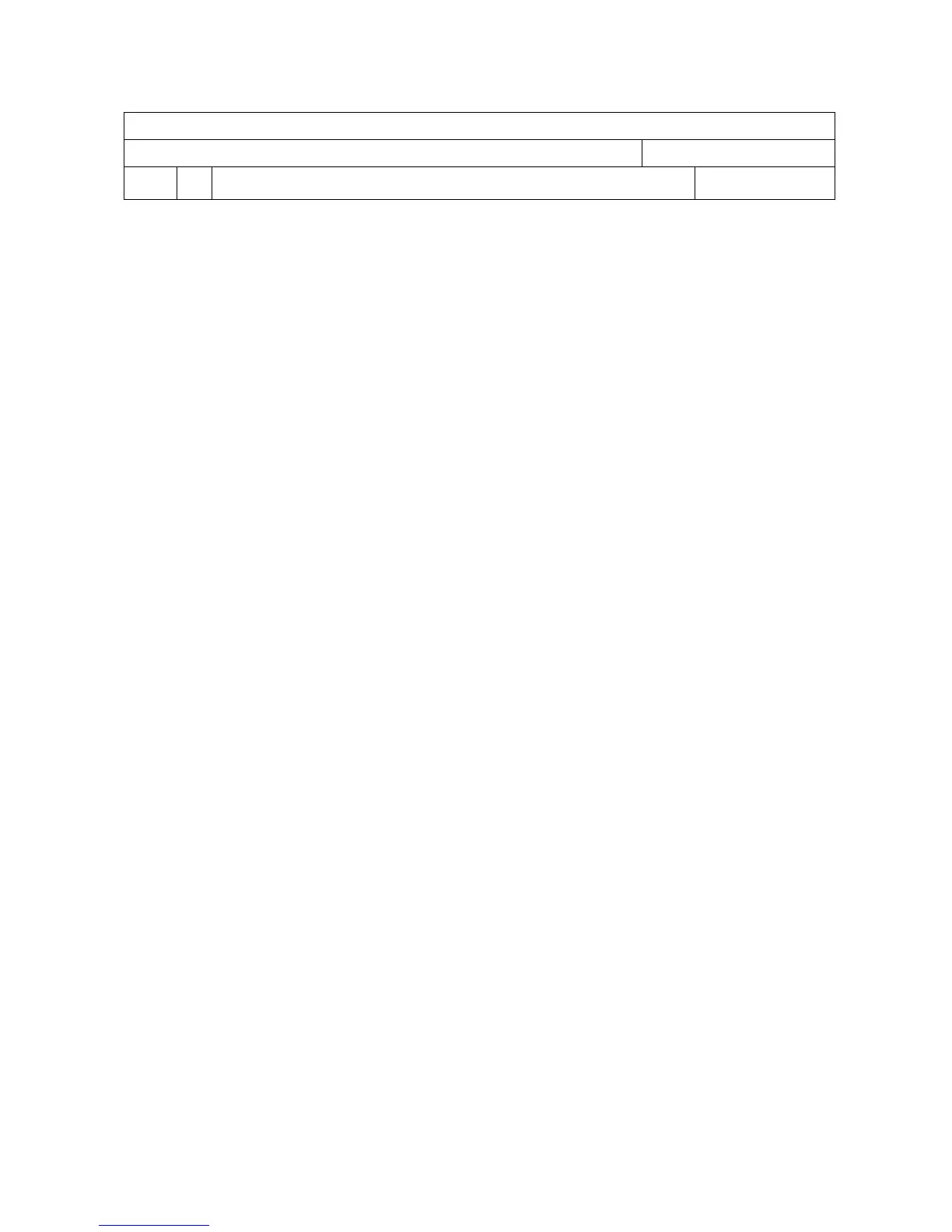
>add filter list-1 permit tcp any 192.168.100.11 32 80
>add filter list-1 permit tcp 140.100.5.5 32 192.168.100.33 32 23
>add filter list-1 deny tcp any any 23
>add filter list-1 permit any 100.3.0.0 16 any
>add filter list-1 permit tcp 140.1.0.0 16 192.168.100.22 32 69
>add filter list-1 deny any any any
The last line can be omitted because if a packet can not match any rules, the packet will be dropped.
If we want to check all the packets received at the WAN1 interface with list-1 policy, then we would issue
the following command: >set filter wan1 inbound list-1
Note: The IP addresses in the above commands are each followed by a subnet mask listed in binary
Code (base two). This subnet mask binary code listing is called a prefix length. If you are
unfamiliar with determining subnet prefix lengths, refer to Chapter 18 Appendix B Converting a
Subnet Mask to Binary Code.
 Loading...
Loading...