the OCSP server for revocation information whenever a peer certificate is received (IPSec,
TLS client mode, or TLS server mode with mutual authentication).
To configure OCSP:
1. Open the General Security Settings page (Configuration tab > VoIP menu >
Security > General Security Settings).
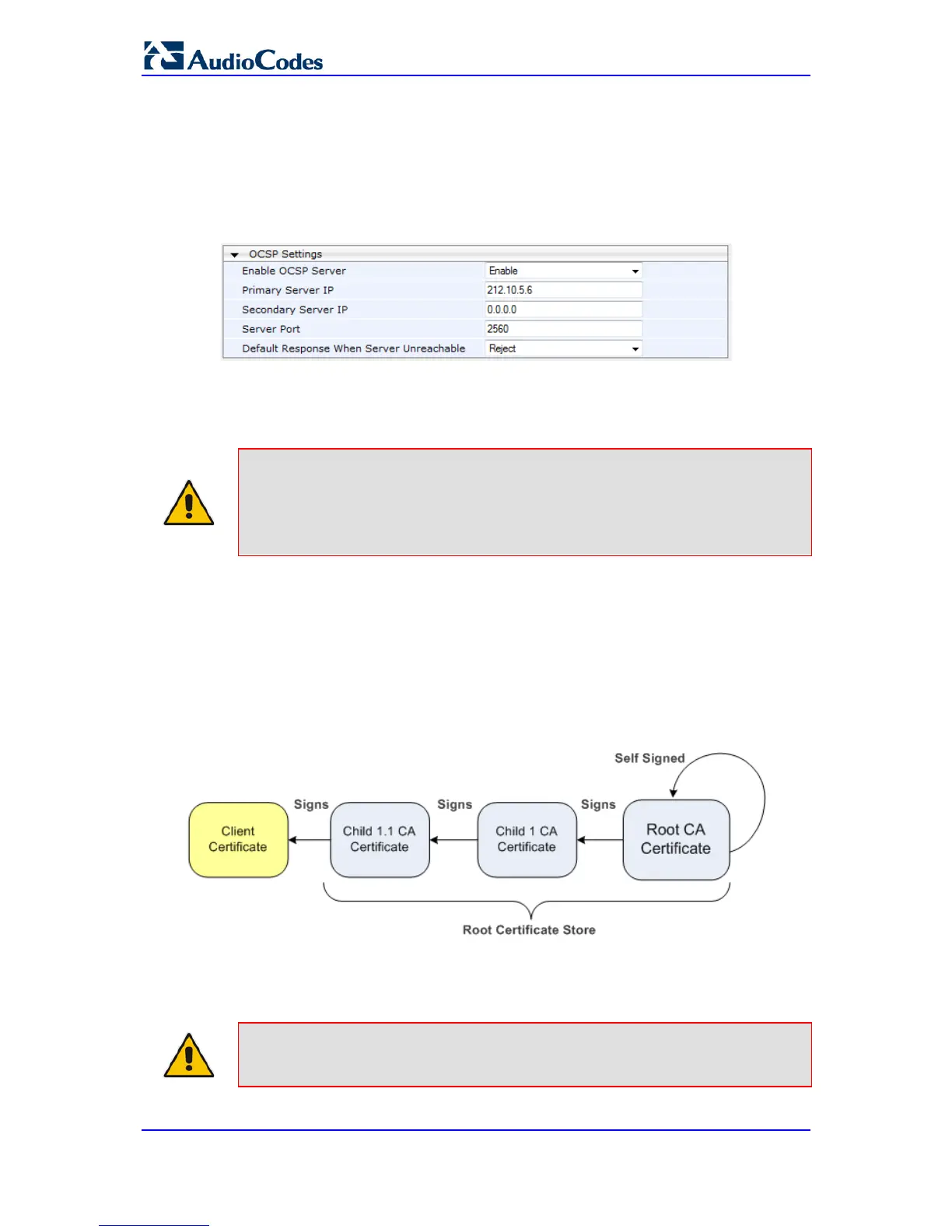
Figure 9-5: OCSP Parameters
2. Configure the OCSP parameters as required. For a description of these parameters,
see OCSP Parameters on page 456.
3. Click Submit.
Notes:
• The device does not query OCSP for its own certificate.
• Some PKIs do not support OCSP but generate Certificate Revocation
Lists (CRLs). For such cases, set up an OCSP server such as OCSPD.
9.7 Loading Certificate Chain for Trusted Root
A certificate chain is a sequence of certificates where each certificate in the chain is signed
by the subsequent certificate. The last certificate in the list of certificates is the Root CA
certificate, which is self-signed. The purpose of a certificate chain is to establish a chain of
trust from a child certificate to the trusted root CA certificate. The CA vouches for the
identity of the child certificate by signing it. A client certificate is considered trusted if one of
the CA certificates up the certificate chain is found in the server certificate directory.
Figure 9-6: Certificate Chain Hierarchy
For the device to trust a whole chain of certificates, you need to combine the certificates
into one text file (using a text editor). Once done, upload the file using the 'Trusted Root
Certificate Store' field in the Certificates page.
Notes:

 Loading...
Loading...











