Version 6.6 137 MP-11x & MP-124
User's Manual 12. Security
• Key exchange (DH): The DH protocol creates the master key. DH requires both
peers to agree on certain mathematical parameters, known as the "group".
• Authentication: The two peers authenticate one another using a pre-shared key
configured in the IP Security Associations Table or by using certificate-based
authentication.
Quick Mode (creates the encrypted IPSec tunnel once initial security is set up):
• SA negotiation: An IPSec SA is created by negotiating encryption and
authentication capabilities using the same proposal mechanism as in Main mode.
• Key exchange: A symmetrical key is created for encrypting IPSec traffic; the
peers communicate with each other in encrypted form, secured by the previously
negotiated "master" key.
IKE specifications summary:
Authentication methods: pre-shared key or certificate-based authentication
Main mode supported for IKE Phase 1
Encryption algorithms: Data Encryption Standard (DES), Advanced Encryption
Standard (AES), and 3DES
Hash algorithms: SHA1 and MD5
IPSec is responsible for securing the IP traffic. This is accomplished by using the
Encapsulation Security Payload (ESP) protocol to encrypt (and decrypt) the IP payload.
This is configured in the IPSec Security Association table, which defines the IP peers to
which IPSec security is applied.
IPSec specifications summary:
Transport and Tunneling Mode
Encapsulation Security Payload (ESP) only
Encryption algorithms: AES, DES, and 3DES
Hash types: SHA1 and MD5
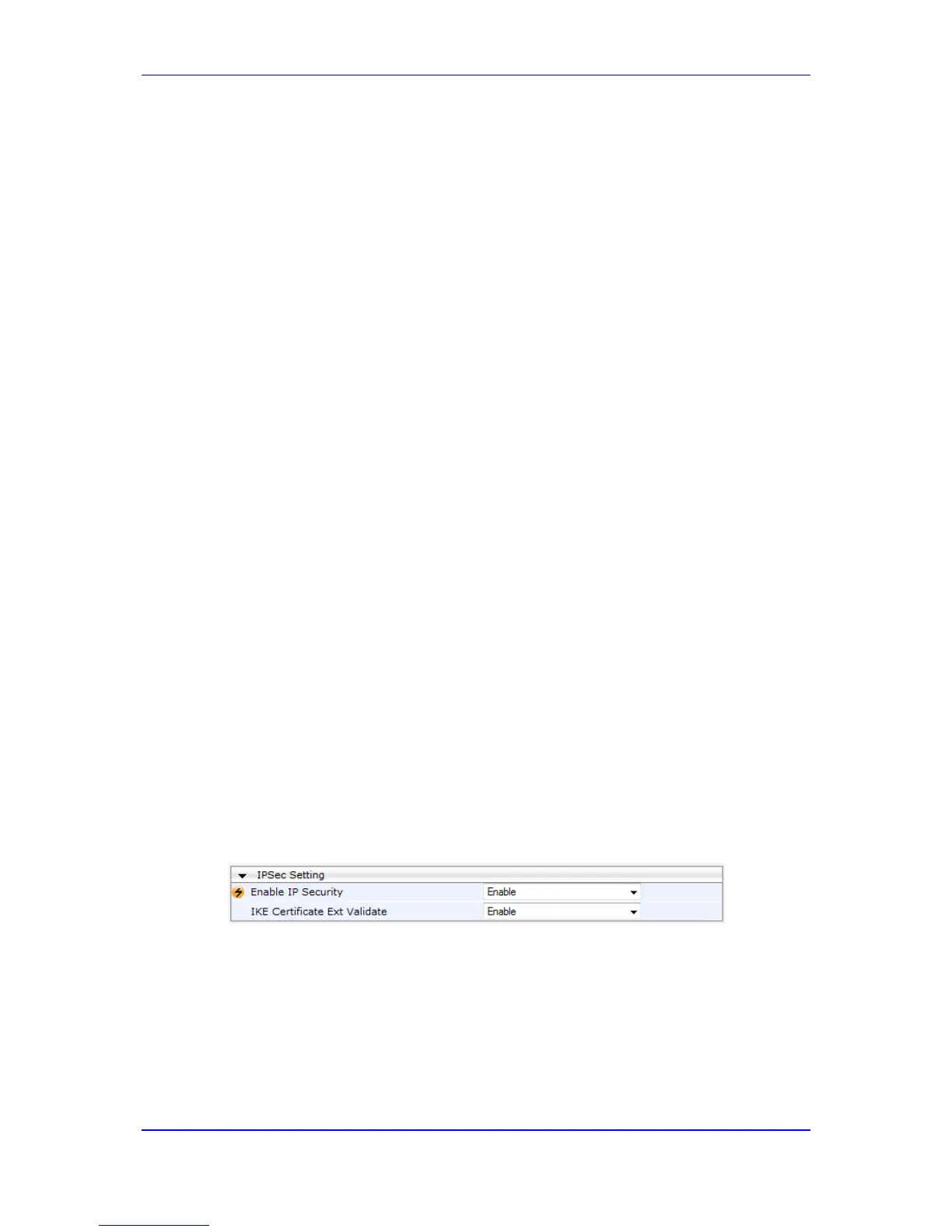
12.4.1 Enabling IPSec
To enable IKE and IPSec processing, you must enable the IPSec feature, as described
below.
To enable IPSec:
1. Open the General Security Settings page (Configuration tab > VoIP menu >
Security > General Security Settings).
Figure 12-3: Enabling IPSec
2. Set the 'Enable IP Security' parameter to Enable.
3. Click Submit, and then reset the device with a flash burn.
12.4.2 Configuring IP Security Proposal Table
The IP Security Proposal Table page is used to configure Internet Key Exchange (IKE) with
up to four proposal settings. Each proposal defines an encryption algorithm, an
authentication algorithm, and a Diffie-Hellman group identifier. The same set of proposals
applies to both Main mode and Quick mode.

 Loading...
Loading...











