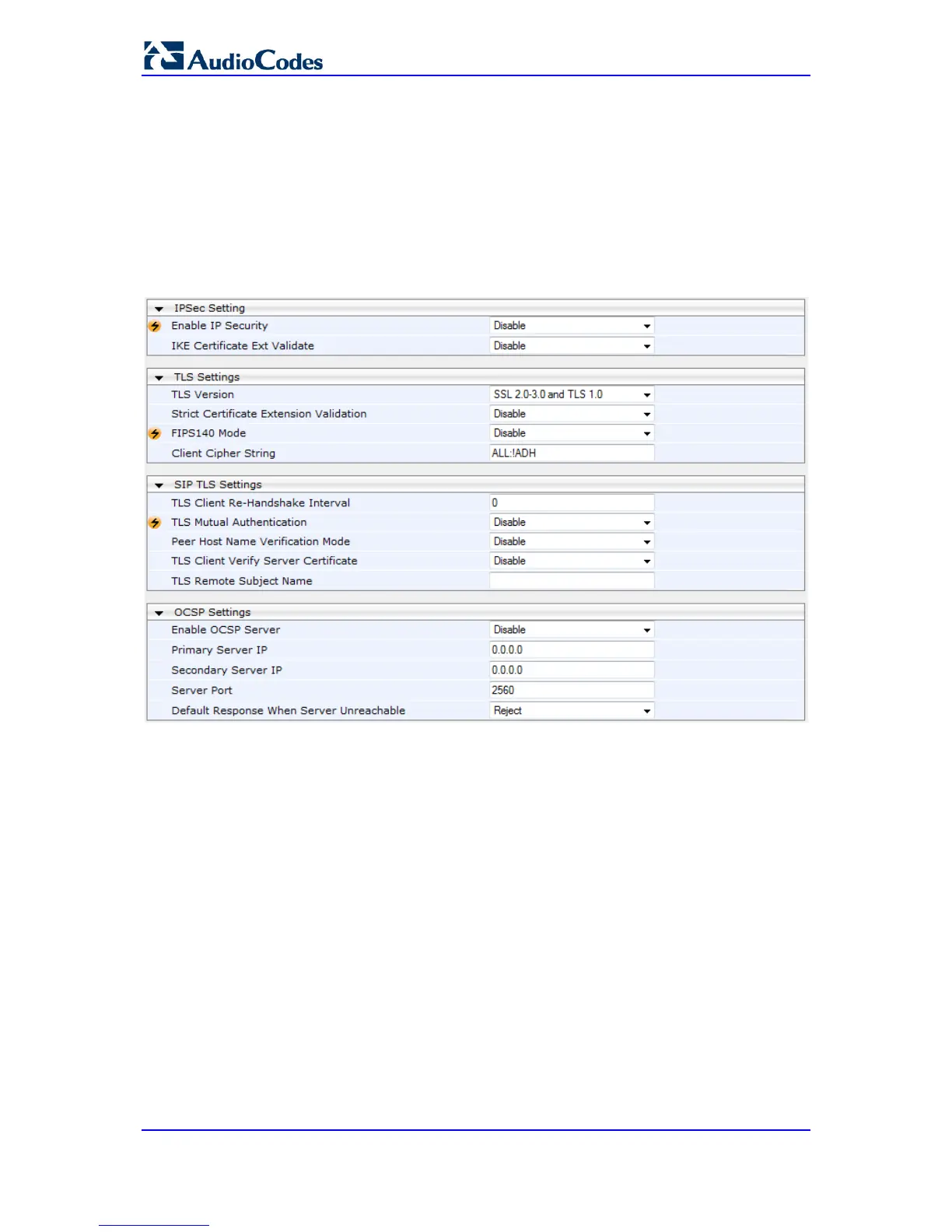
12.3 Configuring General Security Settings
The General Security Settings page is used to configure various security features. For a
description of the parameters appearing on this page, refer 'Configuration Parameters
Reference' on page 421.
To configure the general security parameters:
1. Open the General Security Settings page (Configuration tab > VoIP menu >
Security submenu > General Security Settings).
2. Configure the parameters as required.
3. Click Submit to apply your changes.
4. To save the changes to flash memory, refer to 'Saving Configuration' on page 324.
12.4 IPSec and Internet Key Exchange
IP security (IPSec) and Internet Key Exchange (IKE) protocols are part of the IETF
standards for establishing a secured IP connection between two applications (also referred
to as peers). Providing security services at the IP layer, IPSec and IKE are transparent to
IP applications. IPSec and IKE are used together to provide security for control and
management (e.g., SNMP and Web) protocols, but not for media (i.e., RTP, RTCP and
T.38).
IKE is used to obtain the Security Associations (SA) between peers (the device and the
application it’s trying to contact). The SA contains the encryption keys and profile used by
IPSec to encrypt the IP stream. IKE negotiation comprises the following two phases:
Main Mode (creates a secured channel for the Quick mode by obtaining a "master"
encryption key, without any prior keys, and authenticates the peers to each other):
• SA negotiation: The peers negotiate their capabilities using up to four proposals.
Each proposal includes the Encryption method, Authentication algorithm, and the
Diffie-Hellman (DH) group. The master key’s lifetime is also negotiated.

 Loading...
Loading...











