5486OpS.fm Draft Document for Review October 18, 2004
518 IBM Eserver i5 and iSeries System Handbook
systems and distributed systems that operate within a network controlled by a
host system or by another iSeries server.
Network management functions available for the iSeries server include:
Systems management in TCP/IP networks
Alerts support to NetView®, System/36, System/38, iSeries
Distributed System Node Executive (DSNX)
Security
The many levels of security available with i5/OS and OS/400 ease the job of
system security management. The five levels of security range from minimal to
an enhanced level that enables the iSeries servers to operate at the C2 level of
trust as defined by the United States Government. Security foundation offered
with i5/OS and OS/400 includes system integrity with digital signature and object
signing, a Digital Certificate Manager, and password protection.
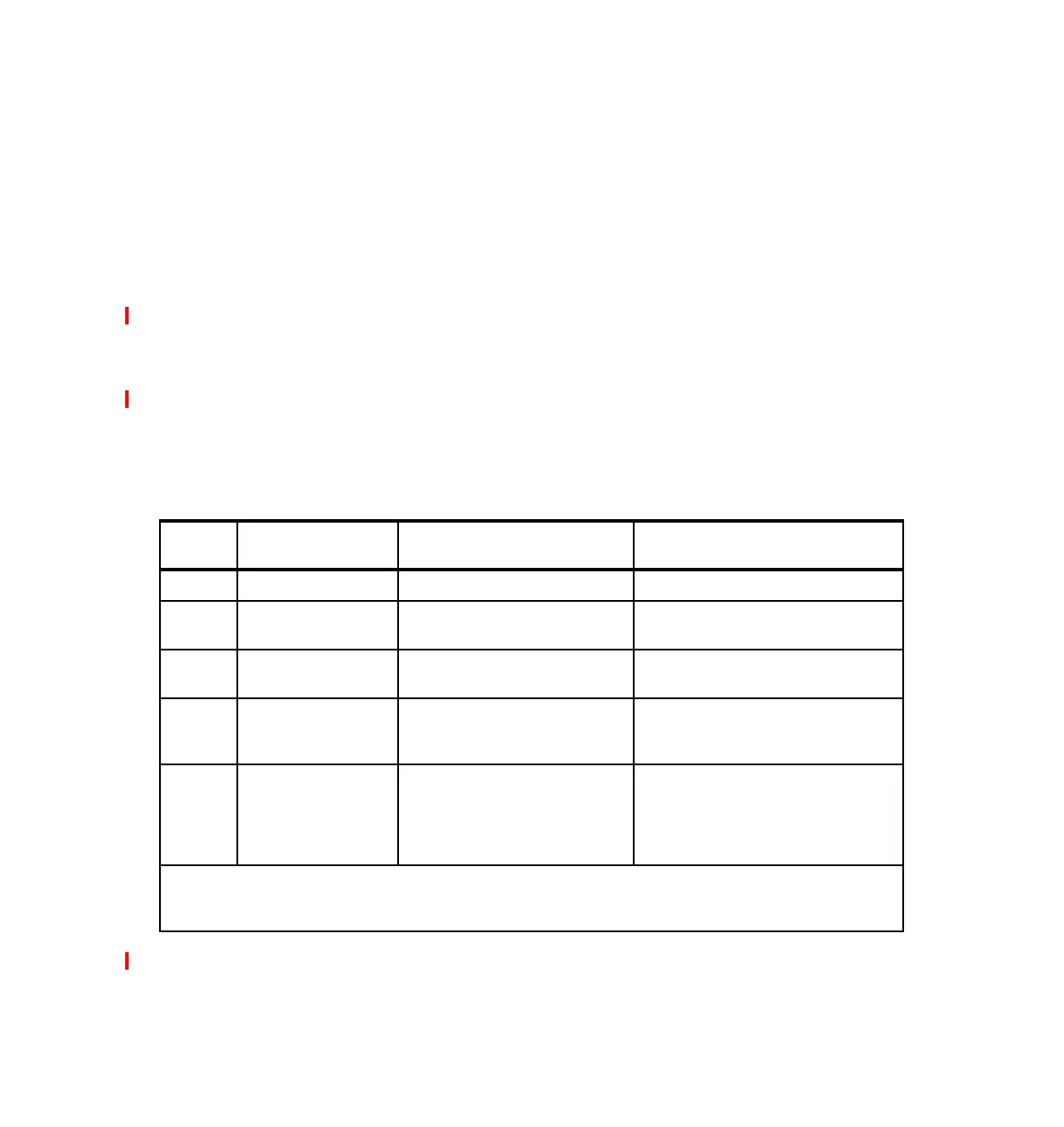
The base level of security is set simply by using a system value, as shown in the
following table.
i5/OS and OS/400 is distributed with the security level set to 40.
Security
level
Description Use of this level Considerations
10 Minimal security No passwords are used. Any user can perform any function.
20 Password security Passwords are used to provide
access to the system.
Any user can perform any function once
they are signed on.
30 Resource security Passwords are required and object
usage can be controlled.
Users can be restricted to specific
functions.
40 Resource security and
operating system
integrity
Passwords are required and object
usage can be controlled. Users can
be restricted to specific functions.
Using unsupported interfaces is
restricted.
50 Enhanced resource
security and operating
system integrity
*
Passwords are required and object
usage can be controlled. Users can
be restricted to specific functions.
Using unsupported interfaces is
restricted.
Parameter validation into the operating
system and restrictions on use of user
domain objects. A security journal is
provided that logs all security violations.
* Enables iSeries servers to operate at the C2 level of trust as defined by the U.S. Government. Refer to publication
DOD 5200.28-STD, “Department of Defense Trusted Computer System Evaluation Criteria” (Orange Book), for
details about the U.S. Government definition of C2 trust level.
 Loading...
Loading...











