355
Usage guidelines
This command displays the configuration information about all IKE proposals in descending order of
proposal priorities. If no IKE proposal is configured, the command displays the default IKE proposal.
Examples
# Display the configuration information about all IKE proposals.
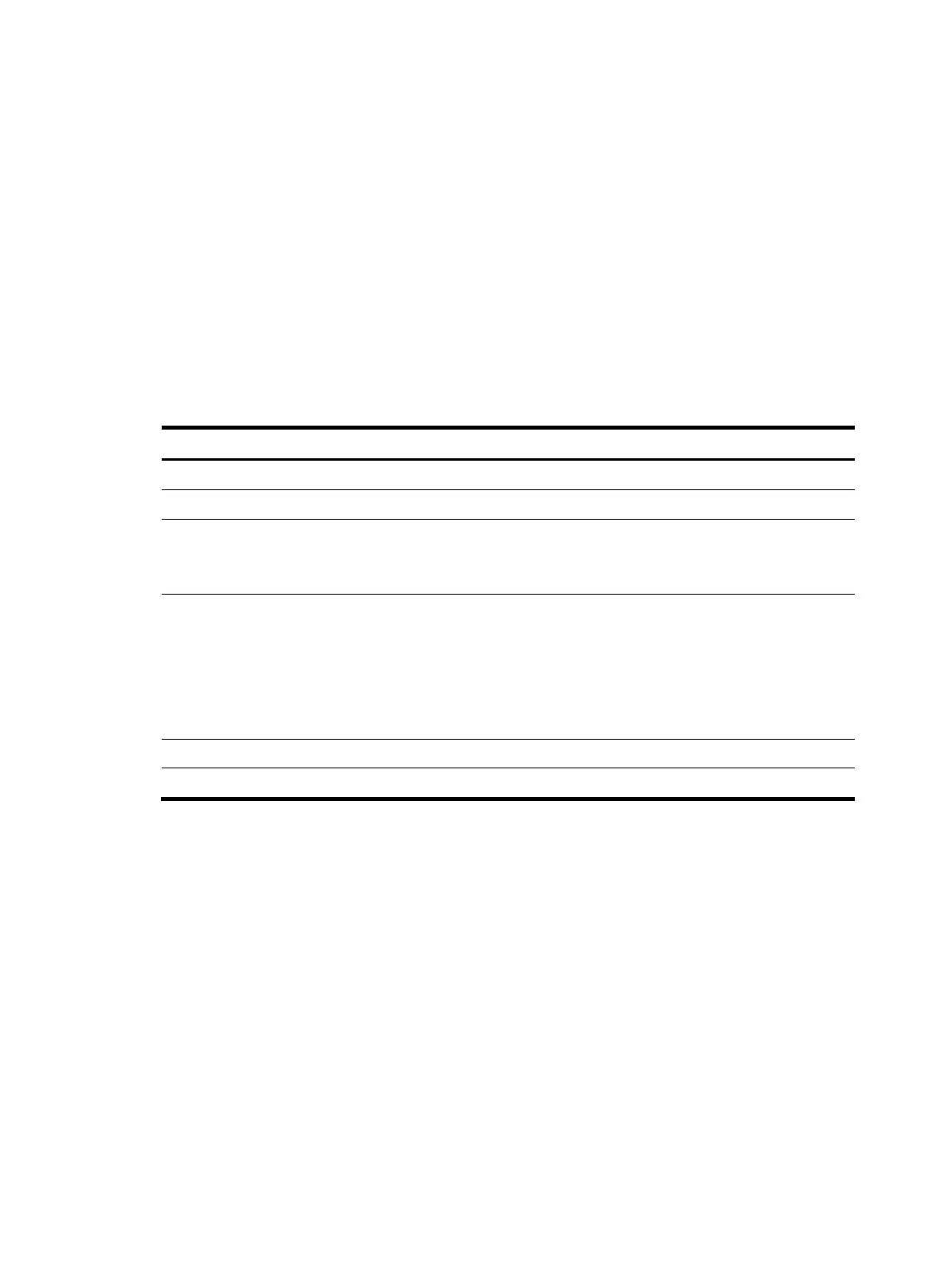
<Sysname> display ike proposal
Priority Authentication Authentication Encryption Diffie-Hellman Duration
method algorithm algorithm group (seconds)
----------------------------------------------------------------------------
1 RSA-SIG SHA1 DES-CBC Group 1 5000
11 PRE-SHARED-KEY SHA1 DES-CBC Group 1 50000
default PRE-SHARED-KEY SHA1 DES-CBC Group 1 86400
Table 45 Command output
Field Description
Priority Priority of the IKE proposal
Authentication method Authentication method used by the IKE proposal.
Authentication algorithm
Authentication algorithm used in the IKE proposal:
• MD5—HMAC-MD5 algorithm.
• SHA1—HMAC-SHA1 algorithm.
Encryption algorithm
Encryption algorithm used by the IKE proposal:
• 3DES-CBC—168-bit 3DES algorithm in CBC mode.
• AES-CBC-128—128-bit AES algorithm in CBC mode.
• AES-CBC-192—192-bit AES algorithm in CBC mode.
• AES-CBC-256—256-bit AES algorithm in CBC mode.
• DES-CBC—56-bit DES algorithm in CBC mode.
Diffie-Hellman group DH group used in IKE negotiation phase 1.
Duration (seconds) IKE SA lifetime (in seconds) of the IKE proposal
Related commands
ike proposal
display ike sa
Use display ike sa to display information about the current IKE SAs.
Syntax
display ike sa [ verbose [ connection-id connection-id | remote-address [ ipv6 ] remote-address
[ vpn-instance vpn-name ] ] ]
Views
Any view
Predefined user roles
network-admin
 Loading...
Loading...