214
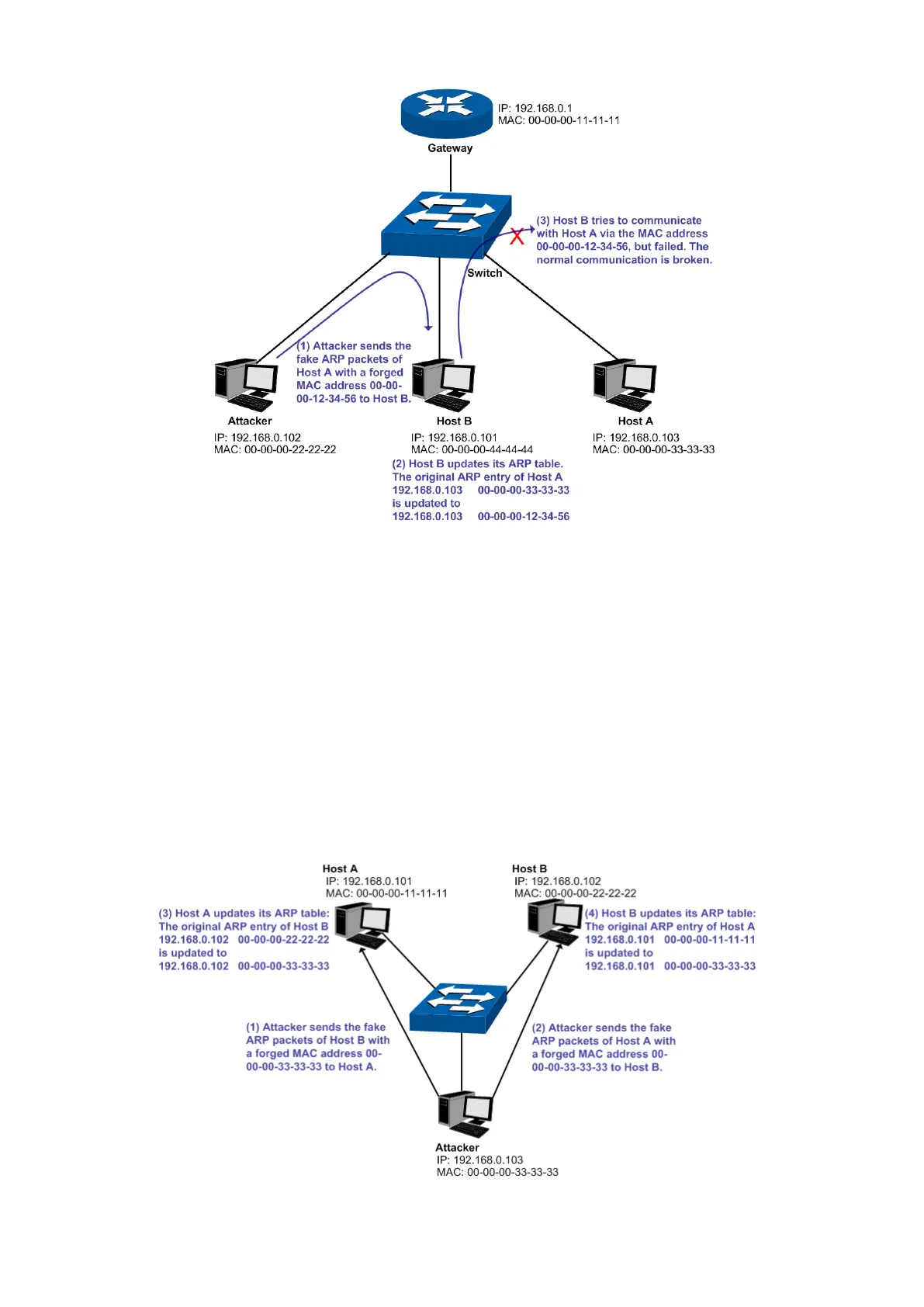
Figure 13-12 ARP Attack – Cheating Terminal Hosts
As the above figure shown, the attacker sends the fake ARP packets of Host A to Host B, and then
Host B will automatically update its ARP table after receiving the ARP packets. When Host B tries
to communicate with Host A, it will encapsulate this false destination MAC address for packets,
which results in a breakdown of the normal communication.
Man-In-The-Middle Attack
The attacker continuously sends the false ARP packets to the Hosts in LAN so as to make the
Hosts maintain the wrong ARP table. When the Hosts in LAN communicate with one another, they
will send the packets to the attacker according to the wrong ARP table. Thus, the attacker can get
and process the packets before forwarding them. During the procedure, the communication
packets information between the two Hosts are stolen in the case that the Hosts were unaware of
the attack. That is called Man-In-The-Middle Attack. The Man-In-The-Middle Attack is illustrated in
the following figure.
Figure 13-13 Man-In-The-Middle Attack
 Loading...
Loading...











