Administrator’s Guide for SIP-T5 Series Smart Media Phones
696
y000000000058.cfg file, account_Security.enc for account.cfg). This tool generates another new
file named as Aeskey.txt to store the plaintext 16-character symmetric keys for each
configuration file.
For a Microsoft Windows platform, you can use a Yealink-supplied encryption tool
“Config_Encrypt_Tool.exe” to encrypt the configuration files respectively.
Note
For security reasons, administrator should upload encrypted configuration files,
<xx_Security>.enc files to the root directory of the provisioning server. During auto provisioning,
the IP phone requests to download the boot file first and then download the referenced
configuration files. For more information on boot file, refer to Boot Files on page 109. For
example, the IP phone downloads account.cfg file and it is encrypted. The IP phone will request
to download <account_Security>.enc file (if enabled) and decrypt it into the the plaintext key
(e.g., key2) using the built-in key (e.g., key1). Then the IP phone decrypts account.cfg file using
key2. After decryption, the IP phone resolves configuration files and updates configuration
settings onto the IP phone system.
The way the IP phone processes other configuration files is the same to that of the account.cfg
file.
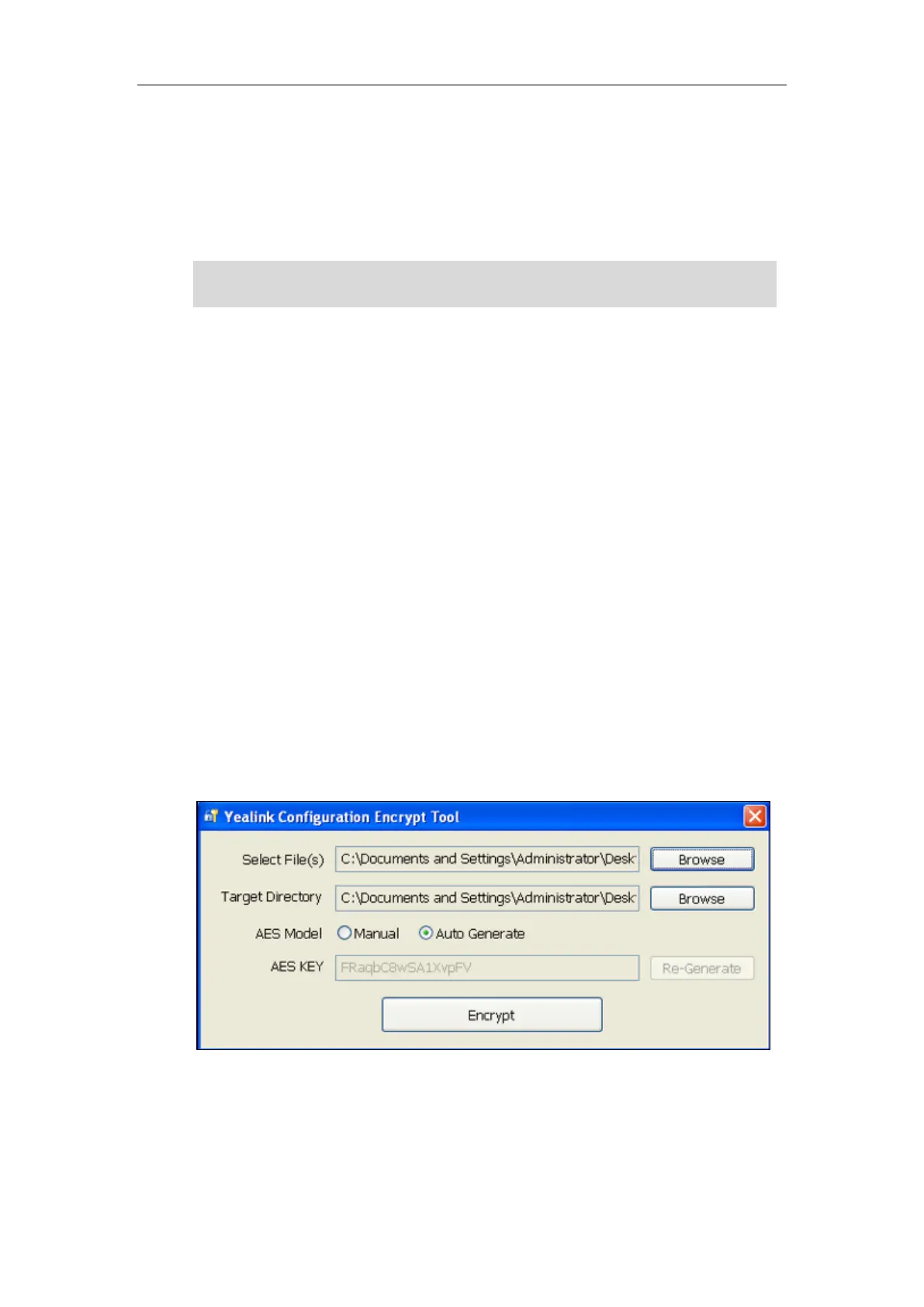
Procedure to Encrypt Configuration Files
To encrypt the <y0000000000xx>.cfg file:
1. Double click “Config_Encrypt_Tool.exe” to start the application tool.
The screenshot of the main page is shown as below:
When you start the application tool, a file folder named “Encrypted” is created
automatically in the directory where the application tool is located.
2. Click Browse to locate configuration file(s) (e.g., y000000000058.cfg) from your local
system in the Select File(s) field.
Yealink also supplies a configuration encryption tool (yealinkencrypt) for Linux platform if
required. For more information, refer to
Yealink Configuration Encryption Tool User Guide
.

 Loading...
Loading...