Manage Users
3.4 Remote Authentication Configuration
3.4.1 Configure RADIUS to Be Remote
Authentication Server
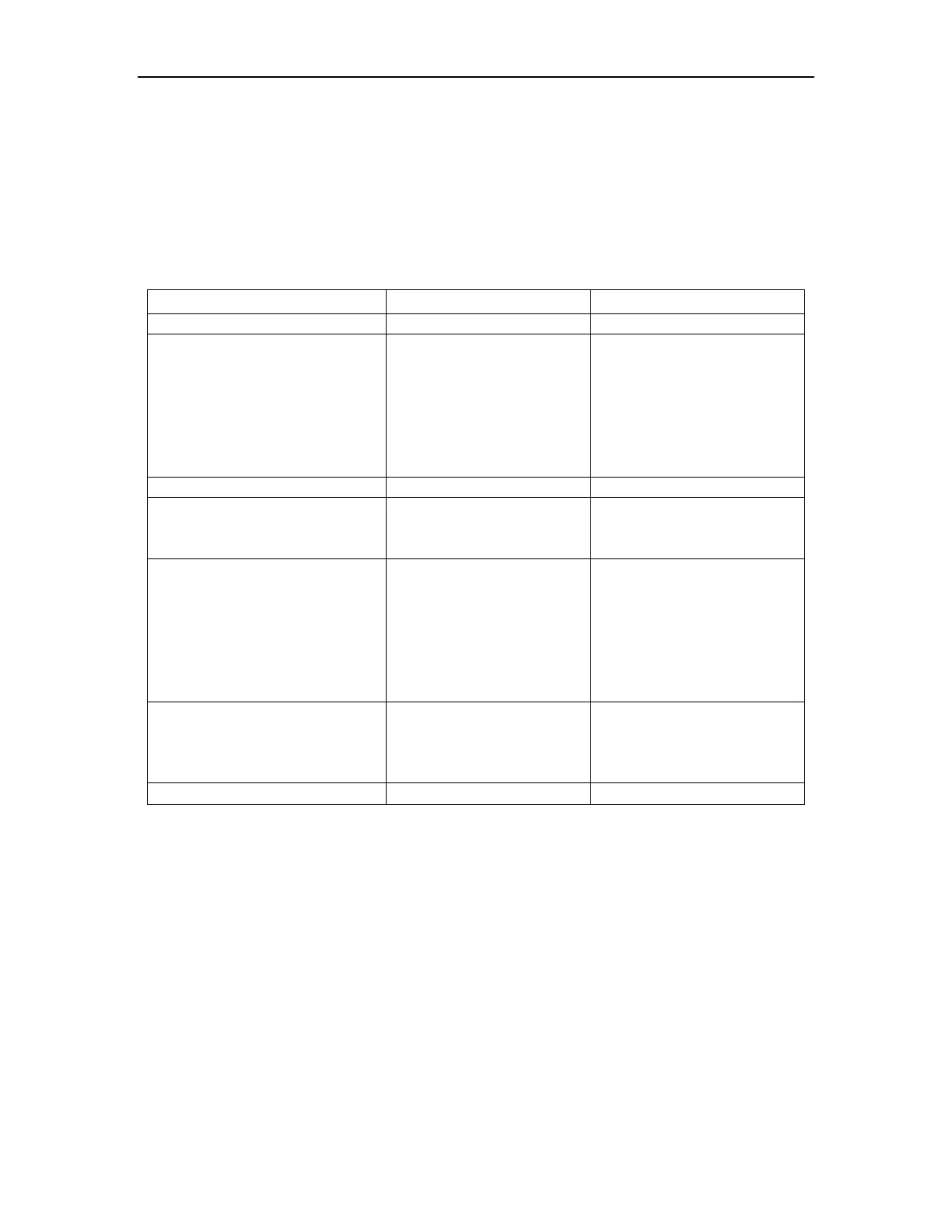
Table 3-6 Configure RADIUS remote authentication
Enter global configuration
Enable RADIUS remote
authentication
muser radius name
{chap|pap} [local]
Selected
If “local“ is configured, it
means local authentication is
used if remote authentication
failed.
By default, it is local
authentication
Enter AAA configuration mode
Create RADIUS server name and
enter RADIUS configuration
mode
Configure IP of
authentication/accounting
RADIUS server
{primary-acct-ip |
primary-auth-ip } A.B.C.D
{ accounting port |
authentication port }
Selected
Authentication and accounting
port should be the same as
that of RADIUS server.
Generally, they are:
Accounting port:1813
Authentication port:1812
Configure shared-key of
authentication/accounting
RADIUS server
{acct-secret-key|
auth-secret-key} key
Selected
Shared-key should be the
same as that of RADIUS
server.
3.4.2 Configure TACACS+ remote authentication
Configuring user’s login through TACACS+ server authentication, accounting and
authorization through TACACS+ server can be chosen. When configuring TACACS+
authorization, configure corresponded priority to users first. There are 16 levels (0-16)
priorities but there are only 2 levels (0-1 means normal users and 2-15 means administrators)
for switches. When configuring TACACS+ un-authorization, the priority is determined by
priv_lvl replied from remote server (no reply means administrator). Authorization failure
means normal user.
When configuring TACACS+ accounting, it begins with the pass of authentication and ends
with user’s exit.

 Loading...
Loading...